Monitoring authentication alternatives
This page talks about the monitoring authentication provided by our system and the nuxeo authentication which is need to get some nuxeo's informations.
- Enumerate all the authentication architectures availables to provide a secure system
- Consider the inconvenience and the advantages of the nuxeo authentication platform and our rails application possibilities
- And choose the best one to provide a flexibe and secure system
There is three alternatives envisaged for the monitoring authentication system.
We have three alternatives for the monitoring authentication system:
For a unique authentication provider for all services. This could be possible using a nodejs application proxy. TODO
The second one is to require two authentication forms, one in Nuxeo and the other one in the rails application. This alternative with perform like this: the user will connect his self from the rails application form and the application will check in her own database if the user exist and check if he have a valid access-token, if it's not the case the application will get a new one from Nuxeo using Oauth 1.0 protocol and save it in the database for the next user's connection.
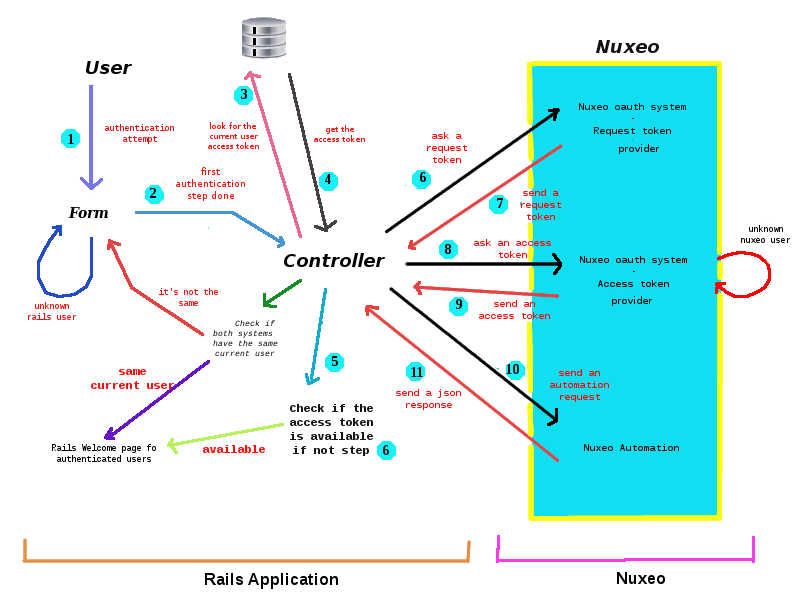
The third alter alternative is a little bit like the second one except the fact that in this case after the user's connection in the rails application the application get from Nuxeo a new access-token and save it (session browser/cookie). So this alternative provide one access-token for one connection and check if both applications(Nuxeo and rails application) have the same current user linked.
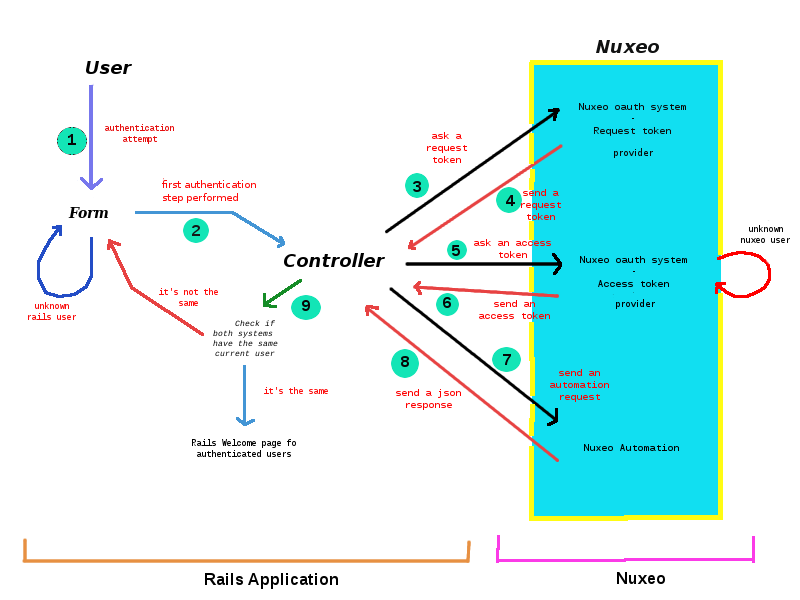
There is some important step which are not mentioned in this schema. After the fourth step the Controller save the request token in the user session and it does the same after the sixth step with the access token. This method is on the top of the three because it allows the user to use both system with only one authentication.