Tutorial SensorClientFIFO LinuxSecurityMonitoring
This tutorial describes how you can monitor your Linux system for suspicious behavior to detect malware or other malicious behavior of an attacker on your system. For this, AlertR is used as notification channel to inform you of an suspicious event. To monitor your Linux system, a collection of Linux Security and Monitoring Scripts are used. For this to work, we assume you have set up the AlertR Server and the AlertR Sensor Client FIFO. Tutorials to set them up are linked.
The following gives you a short example on how to configure the AlertR Sensor Client FIFO with a collection of Linux Security and Monitoring Scripts. The configuration for the security and monitoring scripts has to be individually fine-tuned for your Linux environment and hence are not handled in detail in this tutorial.
On a high-level, the setup looks like the following:
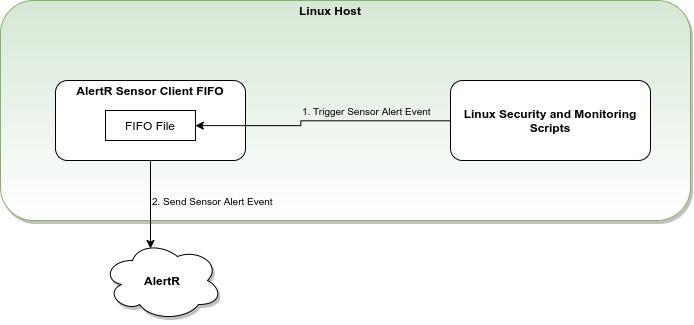
The Linux Security and Monitoring Scripts will notify the AlertR Sensor Client FIFO of a suspicious event by writing into the FIFO file. The AlertR client will then send a corresponding event to the AlertR server which then processes it accordingly.
This tutorial assumes the Alert Levels configured in the AlertR Server tutorial. The client will use the following for its configuration:
| Alert Level | Name | Profiles | Functionality |
|---|---|---|---|
| 3 | Security Event | Activated, Deactivated | Used to directly notify the user regardless of the used System Profile. |
Alert Level 3 is used for sensors that trigger a Sensor Alert that needs direct attention by the user. These sensors should notify the user immediately. This Alert Level is member of every System Profile and thus triggers always.
The following describes the configuration of the AlertR Sensor Client FIFO as well as a setup of a collection of Linux Security and Monitoring Scripts. It shows a basic configuration that can be used as a template for own installations.
To receive security events by the security and monitoring scripts, a FIFO file is used as communication interface. The following shows a basic configuration of a sensor for the AlertR Sensor Client FIFO instance:
[...]
<sensors>
<sensor>
<general
id="0"
description="Linux Security Event"
alertDelay="0"
triggerAlert="True"
triggerAlertNormal="True" />
<alertLevel>3</alertLevel>
<fifo
umask="0000"
fifoFile="./security_event.fifo"
dataType="0" />
</sensor>
</sensors>
[...]
This configuration sets up a FIFO file called security_event.fifo in the directory in which the AlertR client is installed. Using the basic tutorial for the AlertR Sensor Client FIFO as base for this example, the FIFO file will be placed at /home/alertr/sensorClientFIFO/security_event.fifo. The sensor is configured to create Sensor Alert events for triggered as well as normal states, since we want to let the security scripts handle for which state they create Sensor Alerts. The data type of the sensor is set to 0 (None) which means that this sensor does not hold any data.
In this example, we install the collection of Linux Security and Monitoring Scripts under /opt. To install them there, we have to execute the following command as root:
root@towelie:/opt# git clone git@github.com:sqall01/LSMS.git
Afterwards, we configure the scripts to use AlertR as notification channel by editing the file /opt/LSMS/scripts/config/config.py. The edited file looks like the following:
from typing import Optional
# NOTE: If no "AlertR alert settings" and "Mail alert settings" are set to
# None, each script will fall back to print its output.
# AlertR alert settings.
ALERTR_FIFO = "/home/alertr/sensorClientFIFO/security_event.fifo" # type: Optional[str]
# Mail alert settings.
FROM_ADDR = None # type: Optional[str]
TO_ADDR = None # type: Optional[str]
# Directory to hold states in. Defaults to "/tmp" if not set.
STATE_DIR = "state"
# If "start_search.py" is used to execute all scripts, this setting configures
# the time in seconds before a script times out.
START_PROCESS_TIMEOUT = 60
We leave the rest of the configuration files in their default setting. Since every Linux environment is different, you have to fine-tune the scripts yourself to fit your environment.
Finally, we set up cron to run these scripts every hour by executing /opt/LSMS/start_search.py. For this, we add the following lines to /etc/crontab:
# Security monitoring
0 * * * * root /opt/LSMS/start_search.py
#
Afterwards, we restart cron by executing:
root@towelie:/opt# systemctl restart cron
From now on, cron will execute the Linux Security and Monitoring Scripts every hour and changes/suspicious activity will be sent to AlertR.
To check your setup is actually working, you can activate the alert test script of the Linux Security and Monitoring Scripts by editing its configuration file located at /opt/LSMS/scripts/config/test_alert.py:
# Is the script allowed to run or not?
ACTIVATED = True
Next, you have to execute the scripts as root:
root@towelie:/opt# /opt/LSMS/start_search.py
If everything is set up correctly, the execution should run without errors and terminate after a while. The alert test script should have sent a Sensor Alert to AlertR via the configured FIFO file. If the Sensor Alert was received by AlertR, you can deactivate the alert test script in the configuration file again. Otherwise, check the log file of the AlertR Sensor Client FIFO (located at /home/alertr/sensorClientFIFO/logfile.log) and fix any problems that occurred.