Manual key typing
Typing long random looking keys is unavoidable, but everything has been done to make this as easy as it can be.
Firstly, the keys use Bitcoin's WIF format which means there are no characters that resemble each other, and the key the user is typing contains a checksum that detects if the user made a typo.
If after entering the key the program warns about checksum mismatch, the user can press <up arrow> to edit previously entered key. Furthermore, unlike in the pictures in the wiki articles that feature the local testing mode, the keys in non-local-testing mode are split into chunks (3 for local keys, 7 for public keys), and they come with a helpful guide of letters A..Q or A..L:
Local key encryption keys:
A B C D E F G H I J K L M N O P Q
5Ka 52G yNz vjF nM4 2jw Duu rWo 7di zgi Y8g iiy yGd 78L cCx mwQ mWV
X448 public keys:
A B C D E F H H I J K L
4EcuqaD ddsdsuc gBX2PY2 qR8hReA aeSN2oh JB9w5Cv q6BQjDa PPgzSvW 932aHio sT42SKJ Gu2PpS1 Za3Xrao
When a TFC account is being typed from the Relay Program to the Transmitter Program, if the user enters a value the checksum of which does not match, Transmitter Program will automatically export the incorrectly typed TFC account to the Relay Program.
If the Relay Program has received a contact request that is a likely match, it will assume the user meant to type that, and display the differences.
If on the other hand the Relay Program doesn't recognize which account the user intended to add, it will display a GUI prompt to which the user can then copy and paste the TFC account.
This prompt will only accept valid TFC accounts and will display an error if the user makes a typo (unlikely as the assumption is the user copy-pastes the account to it from some source).
Whether or not the GUI prompt needed to be displayed, the Relay program will then display the differences in the actual and typed account.
The diff viewer also works with TFC public keys that together with the guides help a lot with the typing process. The Relay Program always knows which public key the user should be typing so unlike in the case of TFC accounts, GUI prompt is not necessary.
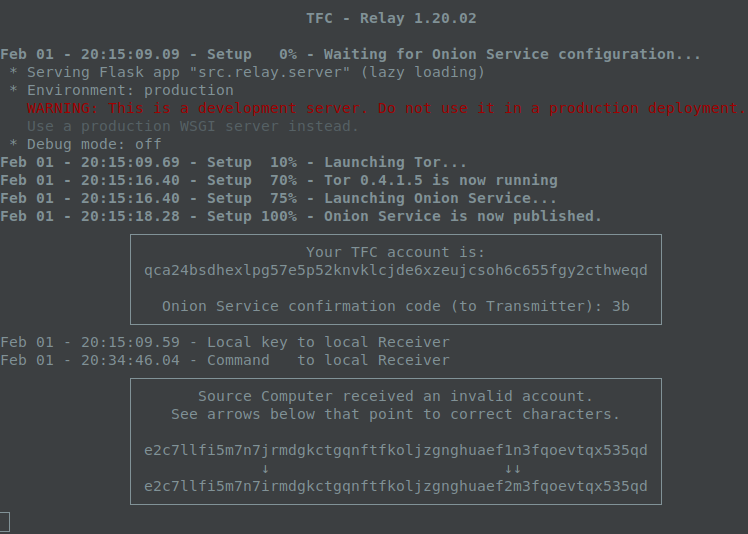
When the three computer setup is used (as opposed to the local testing mode in the picture above), Relay Program will also use the key input guide to make error locations on Transmitter Program even easier to spot:
┌─────────────────────────────────────────────────────────────────────────────────────────────────┐
│ Source Computer received an invalid public key. │
│ See arrows below that point to correct characters. │
│ │
│ A B C D E F G H I J K L │
│ 4EEJKap 9yReFo9 SdSKPhU gsQgskd 19nJBrh iBuDmcB 7yzucbY MaGtpQF 8de88KH WLqWtoh zLKWtqT v9HG5Fb │
│ ↓ ↓ ↓↓ ↓↓ │
│ 4EEjKap 9yReFo8 SdSKPhU gsQgsKD 19nJBrh iBuDmcB 7yzucbY MaGtpQF 8de99KH WLqWtoh zLKWtqT v9HG5Fb │
│ A B C D E F G H I J K L │
└─────────────────────────────────────────────────────────────────────────────────────────────────┘
To prevent the user from accidentally shooting themselves in the foot by copy-pasting the local key decryption key, the TFC account entry box only exports full length, lowercase strings.
As for the public key input that also uses Base58 encoding, the Transmitter Program also requires full length public key. Additionally, it stores the hash of the local key decryption key into the contact database, and in the event the user enters the local key decryption key somewhere amidst the public key, the Transmitter Program will detect it by hashing all 51-character long substrings, and by comparing the digests against the stored digest. If a match is found, the key won't be exported, but instead only a checksum error is displayed.
Note: These mechanisms do not prevent the user from doing stupid things intentionally, but they significantly reduce the probability of accidentally revealing the local key decryption key. It should also be noted that in normal three-computer system it's pointless to copy the local key decryption key on clipboard, but validation of what can be output is still good practice.