-
Notifications
You must be signed in to change notification settings - Fork 11
Cryptography
Cryptography is represented in an ontology, to enable certain services to use cryptographic techniques at highlevel of abstraction.
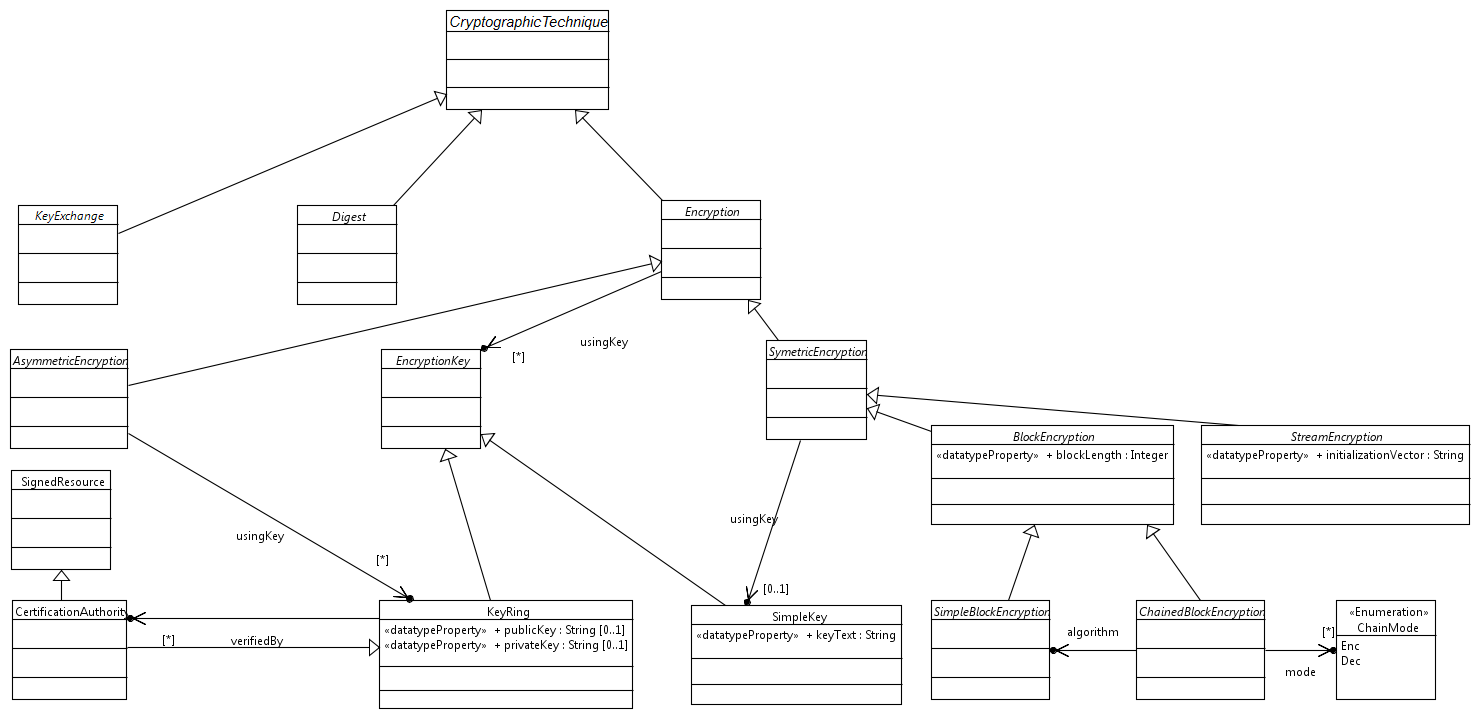
Definition for key exchange algorithms.
Or Hash, transforms uniformly data into a string of data. The ontology provides some instances like MD2, MD5, SHA, SHA256,SHA384, and SHA512.
A generic concept of ofuscating information so only the appropriate key holder is able to read it back.
An encryption method where the sender and receiver use the same key. Instances include AES, DES, and Blowfish.
An encryption method where the sender and receiver use different keys. Instances include DSA and RSA.
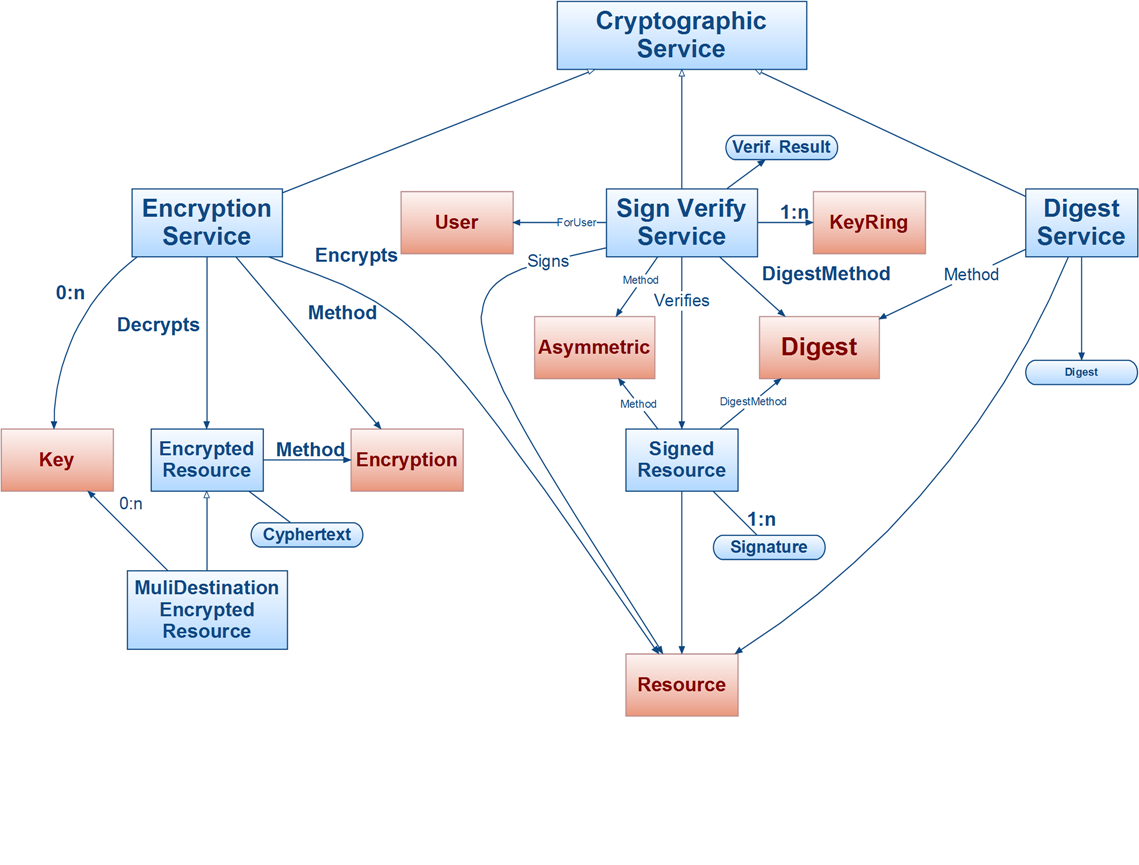
Enables the encryption, and decyphering, of RDF resources; using various methods.
Enables the use of asymetric encryption keys (and some Digest method) to assure a particular key holder to sign resources, wrapping them into a SignedResource instance. The same service can verify that the key holder has infact signed a particular SignedResource
Enables the use of Digest algorithms on RDF instances.