Quick tutorial:
This repository represents a merge of two powerful cyber adversary datasets, in order to capitalize on each one's strengths: MITRE ATT&CK and its Group-to-TTP linkages; and ETDA/ThaiCERT's Threat Group Cards and their structured "metadata" fields, containing supporting details about real-world cyber threat activity, such as victim industry & country and suspected attacker country & motivation.
Anecdotally, ThaiCERT's repository is less well-known yet it contains a wealth of useful - and importantly, structured, cyber threat event metadata. Among many other data points, the repository contains 400+ named adversary groups and event metadata covering:
- 41 industry sectors
- 149 victim countries
- 16 attacker countries
- 4 attacker motivation categories: Sabotage and destruction, Information theft and espionage, Financial gain (generally), and Financial crime (specifically)
MITRE ATT&CK's popular knowledge base contains profiles on 130+ actor groups. A key value of ATT&CK's dataset is its links between groups and their associated identified Tactics, Techniques, & Procedures, based on use observed in publicly reported threat activity. Tactics, Techniques & Sub-Techniques have unique identifiers allowing teams across the community to use a common language to refer back to the same TTPs.
The merge of the adversary datasets is based on a quick matching algorithm involving small twists on the very many actor names and variations (1,300+!) in each source. The script used to generate the dataset is available here and structured for continuous updates to the dataset over time. The first merge, on May 24, 2022, yielded the following metrics around the output dataset contained here:
- Total adversary groups: 124
- Total name variations: 1,351 (average of ~11 per group)
- Total number of associated ATT&CK techniques & sub-techniques: 364 (there are currently ~580 techniques & sub-techniques in the Enterprise ATT&CK matrix)
A key anticipated use case for this repository is to support faster development of inputs to an organization's cyber threat model/profile:
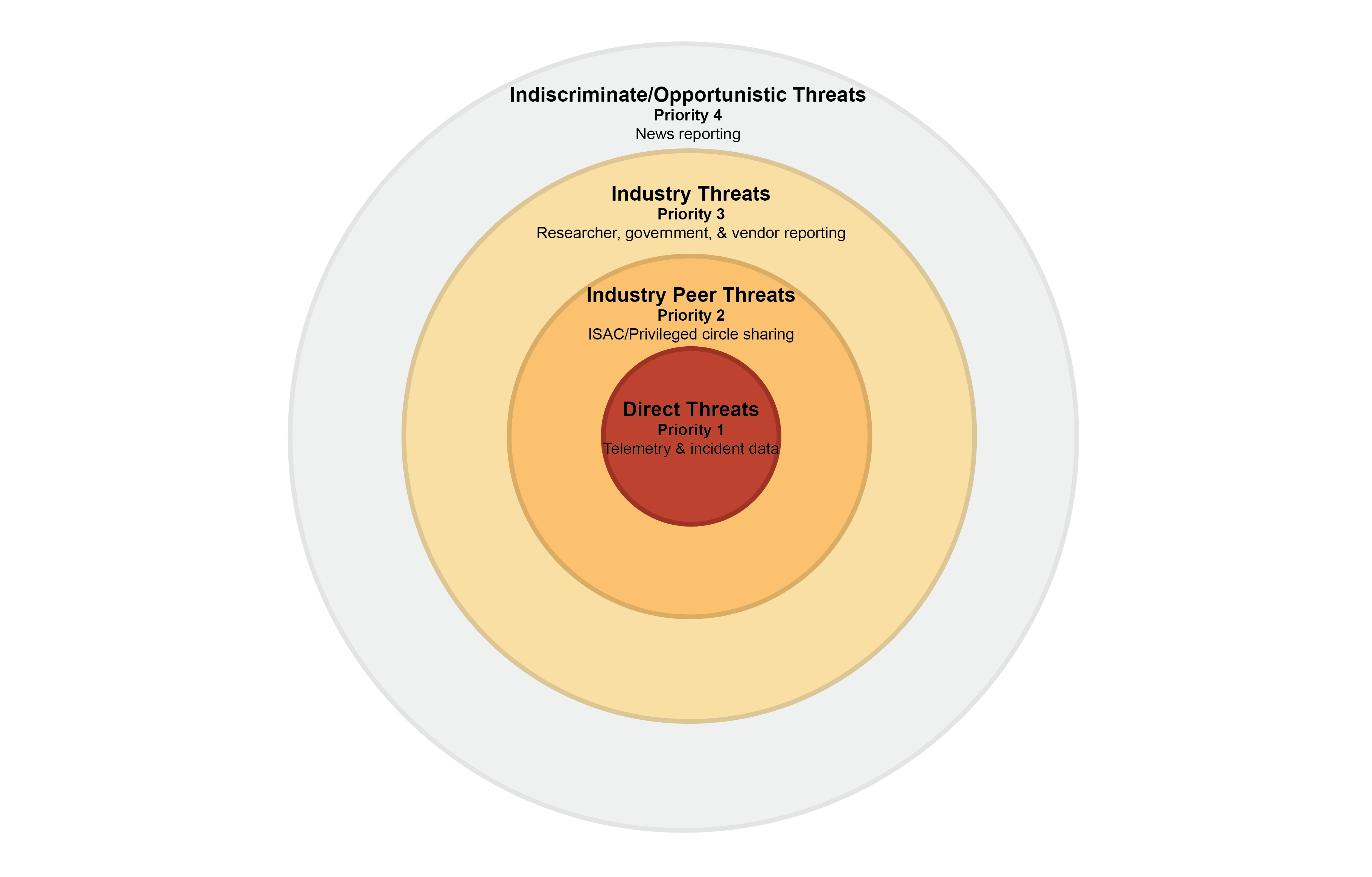 Dropping these inputs into Control Validation Compass enables further fast pivoting to relevant controls & validation tests aligned with each relevant top-priority TTP.
Dropping these inputs into Control Validation Compass enables further fast pivoting to relevant controls & validation tests aligned with each relevant top-priority TTP.
The rough merge of the datasets enables easier analysis along the following lines:
- What is the distribution of TTPs used against a given industry, and/or how does that compare to other industries? For example:
Aerospace Industry TTPs (data, live visualization)
Pharmaceutical Industry TTPs (data, live visualization)
- What is the distribution of TTPs used by certain types of adversaries, based on their motivations, and/or how does that compare to other types of adversaries? For example:
"Information theft and espionage" Adversary TTPs (data, live visualization)
"Financial crime" Adversary TTPs (data, live visualization)
See the quick tutorial here
Details and examples for using the data files in this repository are continuing to be built and live in the heatmaps and csv_for_pivot_tables folders.
Immense thanks to the supporting teams and independent contributors to MITRE ATT&CK, and to Martijn van der Heide, the rest of ThaiCERT, and contributing CERT teams and security researchers supporting the Threat Group Cards project. Thank you for continuing to maintain and make publicly available these critical security resources.
MITRE ATT&CK® is a registered trademark of The MITRE Corporation
Threat Group Cards: A Threat Actor Encyclopedia is a Copyright © Electronic Transactions Development Agency, 2019-2022