Releases: simeononsecurity/Windows-Optimize-Harden-Debloat
4.0.2
Full Changelog: 4.0.1...4.0.2
How to run the script:
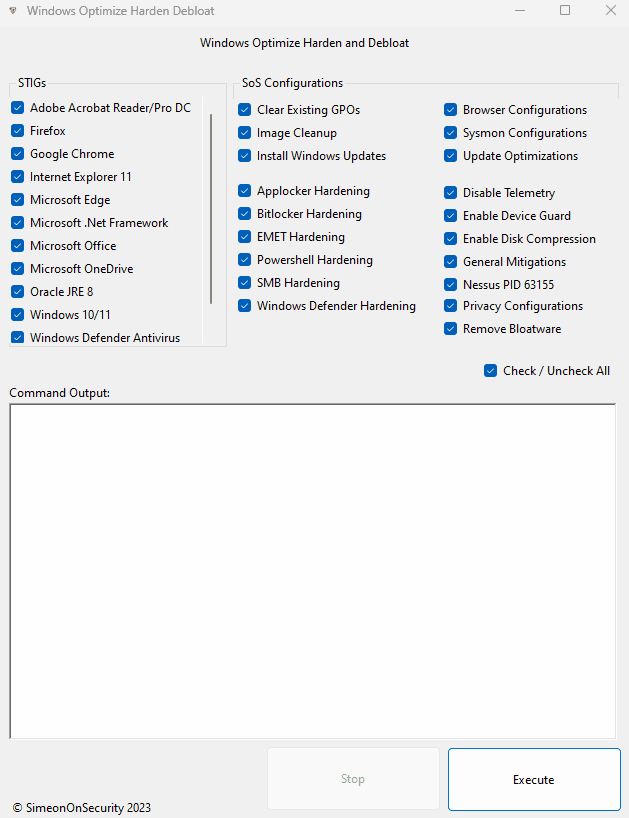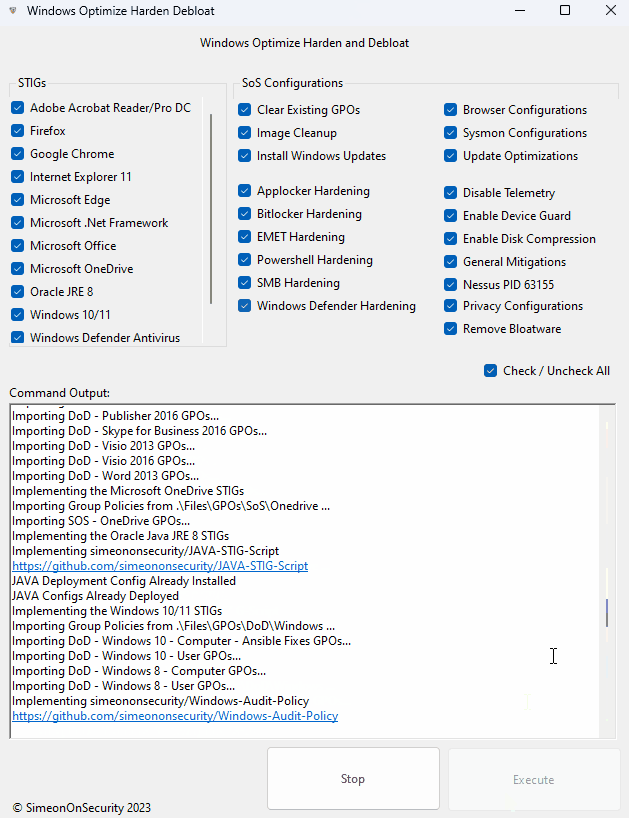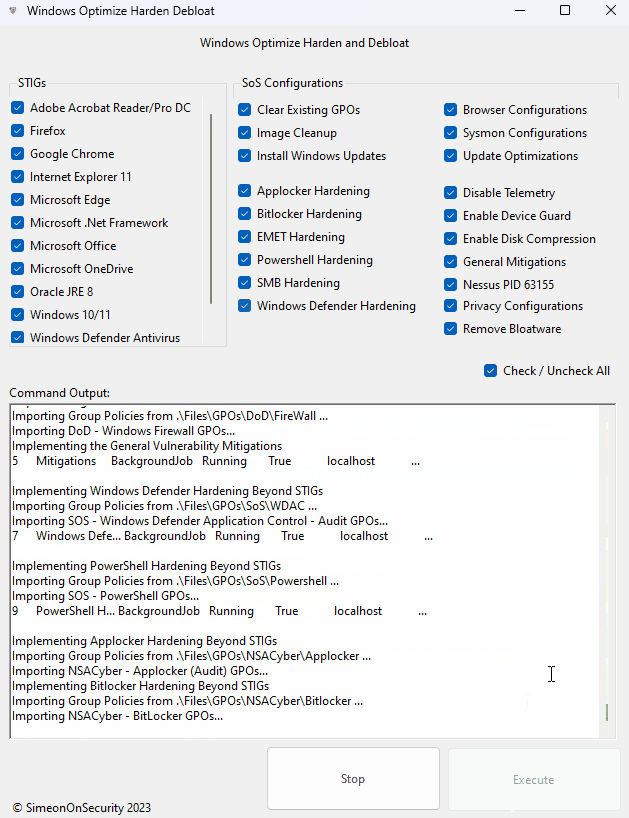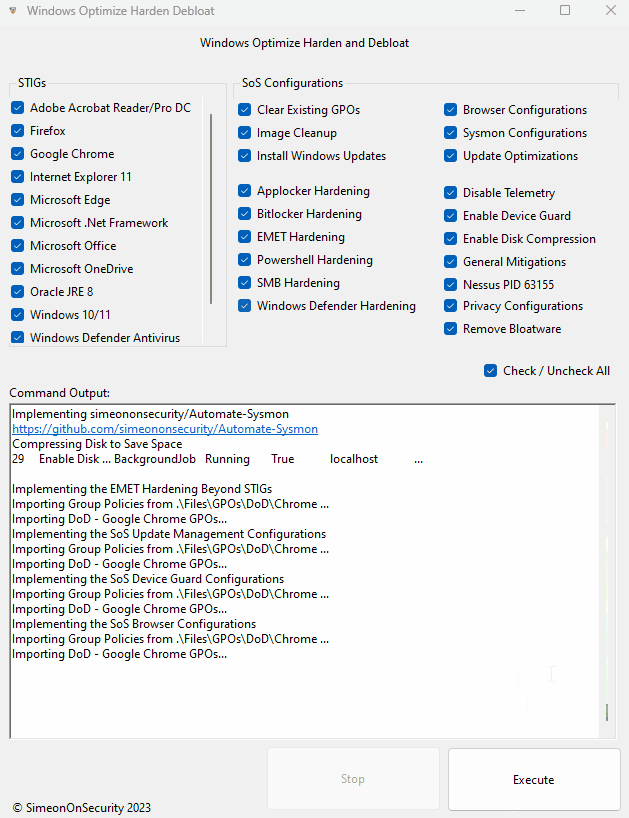
GUI - Guided Install:
Download the latest release here, choose the options you want and hit execute.
Automated Install:
Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iexManual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
The script "sos-optimize-windows.ps1" includes several parameters that allow for customization of the optimization process. Each parameter is a boolean value that defaults to true if not specified.
- cleargpos: Clears Group Policy Objects settings.
- installupdates: Installs updates to the system.
- adobe: Implements the Adobe Acrobat Reader STIGs.
- firefox: Implements the FireFox STIG.
- chrome: Implements the Google Chrome STIG.
- IE11: Implements the Internet Explorer 11 STIG.
- edge: Implements the Microsoft Chromium Edge STIG.
- dotnet: Implements the Dot Net 4 STIG.
- office: Implements the Microsoft Office Related STIGs.
- onedrive: Implements the Onedrive STIGs.
- java: Implements the Oracle Java JRE 8 STIG.
- windows: Implements the Windows Desktop STIGs.
- defender: Implements the Windows Defender STIG.
- firewall: Implements the Windows Firewall STIG.
- mitigations: Implements General Best Practice Mitigations.
- defenderhardening: Implements and Hardens Windows Defender Beyond STIG Requirements.
- pshardening: Implements PowerShell Hardening and Logging.
- sslhardening: Implements SSL Hardening.
- smbhardening: Hardens SMB Client and Server Settings.
- applockerhardening: Installs and Configures Applocker (In Audit Only Mode).
- bitlockerhardening: Harden Bitlocker Implementation.
- removebloatware: Removes unnecessary programs and features from the system.
- disabletelemetry: Disables data collection and telemetry.
- privacy: Makes changes to improve privacy.
- imagecleanup: Cleans up unneeded files from the system.
- nessusPID: Resolves Unquoted System Strings in Path.
- sysmon: Installs and configures sysmon to improve auditing capabilities.
- diskcompression: Compresses the system disk.
- emet: Implements STIG Requirements and Hardening for EMET on Windows 7 Systems.
- updatemanagement: Changes the way updates are managed and improved on the system.
- deviceguard: Enables Device Guard Hardening.
- sosbrowsers: Optimizes the system's web browsers.
An example of how to launch the script with specific parameters would be:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
powershell.exe -ExecutionPolicy ByPass -File .\sos-optimize-windows.ps1 -cleargpos:$false -installupdates:$false4.0.1
Full Changelog: 4.0...4.0.1
How to run the script:
GUI - Guided Install:
Download the latest release here, choose the options you want and hit execute.
Automated Install:
Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iexManual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
The script "sos-optimize-windows.ps1" includes several parameters that allow for customization of the optimization process. Each parameter is a boolean value that defaults to true if not specified.
- cleargpos: Clears Group Policy Objects settings.
- installupdates: Installs updates to the system.
- adobe: Implements the Adobe Acrobat Reader STIGs.
- firefox: Implements the FireFox STIG.
- chrome: Implements the Google Chrome STIG.
- IE11: Implements the Internet Explorer 11 STIG.
- edge: Implements the Microsoft Chromium Edge STIG.
- dotnet: Implements the Dot Net 4 STIG.
- office: Implements the Microsoft Office Related STIGs.
- onedrive: Implements the Onedrive STIGs.
- java: Implements the Oracle Java JRE 8 STIG.
- windows: Implements the Windows Desktop STIGs.
- defender: Implements the Windows Defender STIG.
- firewall: Implements the Windows Firewall STIG.
- mitigations: Implements General Best Practice Mitigations.
- defenderhardening: Implements and Hardens Windows Defender Beyond STIG Requirements.
- pshardening: Implements PowerShell Hardening and Logging.
- sslhardening: Implements SSL Hardening.
- smbhardening: Hardens SMB Client and Server Settings.
- applockerhardening: Installs and Configures Applocker (In Audit Only Mode).
- bitlockerhardening: Harden Bitlocker Implementation.
- removebloatware: Removes unnecessary programs and features from the system.
- disabletelemetry: Disables data collection and telemetry.
- privacy: Makes changes to improve privacy.
- imagecleanup: Cleans up unneeded files from the system.
- nessusPID: Resolves Unquoted System Strings in Path.
- sysmon: Installs and configures sysmon to improve auditing capabilities.
- diskcompression: Compresses the system disk.
- emet: Implements STIG Requirements and Hardening for EMET on Windows 7 Systems.
- updatemanagement: Changes the way updates are managed and improved on the system.
- deviceguard: Enables Device Guard Hardening.
- sosbrowsers: Optimizes the system's web browsers.
An example of how to launch the script with specific parameters would be:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
powershell.exe -ExecutionPolicy ByPass -File .\sos-optimize-windows.ps1 -cleargpos:$false -installupdates:$false4.0 - Optimize, Harden, and Debloat Windows 10 and Windows 11 Deployments
What's Changed
Full Changelog: 3.5...4.0
How to run the script:
GUI - Guided Install:
Download the latest release here, choose the options you want and hit execute.
Automated Install:
Use this one-liner to automatically download, unzip all supporting files, and run the latest version of the script.
iwr -useb 'https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'|iexManual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
The script "sos-optimize-windows.ps1" includes several parameters that allow for customization of the optimization process. Each parameter is a boolean value that defaults to true if not specified.
- cleargpos: Clears Group Policy Objects settings.
- installupdates: Installs updates to the system.
- adobe: Implements the Adobe Acrobat Reader STIGs.
- firefox: Implements the FireFox STIG.
- chrome: Implements the Google Chrome STIG.
- IE11: Implements the Internet Explorer 11 STIG.
- edge: Implements the Microsoft Chromium Edge STIG.
- dotnet: Implements the Dot Net 4 STIG.
- office: Implements the Microsoft Office Related STIGs.
- onedrive: Implements the Onedrive STIGs.
- java: Implements the Oracle Java JRE 8 STIG.
- windows: Implements the Windows Desktop STIGs.
- defender: Implements the Windows Defender STIG.
- firewall: Implements the Windows Firewall STIG.
- mitigations: Implements General Best Practice Mitigations.
- defenderhardening: Implements and Hardens Windows Defender Beyond STIG Requirements.
- pshardening: Implements PowerShell Hardening and Logging.
- sslhardening: Implements SSL Hardening.
- smbhardening: Hardens SMB Client and Server Settings.
- applockerhardening: Installs and Configures Applocker (In Audit Only Mode).
- bitlockerhardening: Harden Bitlocker Implementation.
- removebloatware: Removes unnecessary programs and features from the system.
- disabletelemetry: Disables data collection and telemetry.
- privacy: Makes changes to improve privacy.
- imagecleanup: Cleans up unneeded files from the system.
- nessusPID: Resolves Unquoted System Strings in Path.
- sysmon: Installs and configures sysmon to improve auditing capabilities.
- diskcompression: Compresses the system disk.
- emet: Implements STIG Requirements and Hardening for EMET on Windows 7 Systems.
- updatemanagement: Changes the way updates are managed and improved on the system.
- deviceguard: Enables Device Guard Hardening.
- sosbrowsers: Optimizes the system's web browsers.
An example of how to launch the script with specific parameters would be:
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
powershell.exe -ExecutionPolicy ByPass -File .\sos-optimize-windows.ps1 -cleargpos:$false -installupdates:$falseOptimize, Harden, and Debloat Windows 10 Deployments
How to run the script:
Manual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
.\sos-optimize-windows.ps1Optimize, Harden, and Debloat Windows 10 Deployments
##Whats New?
- STIG Updates
- Updated to cover Q4 STIG Changes
- FireFox STIG
- Oracle JRE 8 Java STIG
- .NET STIG changes
- More Debloating
- Remove Telemetry from Nvidia, Office 2013-2019, PowerShell 6, and VSCode
- Covers Windows 10 20H2 Apps and Bloatware
- More Hardening
- Disable LLMNR
- Disable NETBIOS/TCP-IP
- Windows Defender Hardening
- WDAC Policies
- ASR Rules
How to run the script:
Manual Install:
If manually downloaded, the script must be launched from an administrative powershell in the directory containing all the files from the GitHub Repository
Set-ExecutionPolicy -ExecutionPolicy RemoteSigned -Force
Get-ChildItem -Recurse *.ps1 | Unblock-File
.\sos-optimize-windows.ps1Automated Install:
The script may be launched from the extracted GitHub download like this:
iex ((New-Object System.Net.WebClient).DownloadString('https://simeononsecurity.ch/scripts/windowsoptimizeandharden.ps1'))2.5.0 - Optimize and Harden Windows 10 Deployments
Optimizing and Hardening Windows 10 Deployments
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
The script may be launched from the extracted GitHub download like this:
.\W10-Optimize-and-Harden-master\installallstandalone.ps1
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
In order to enable the Windows 10 VDI Optimizations you must uncomment the line below:
.\Files\Optional\"Windows_10_VDI"\1909_WindowsUpdateEnabled\Win10_1909_VDI_Optimize.ps1
In order to enable the SSL Hardening you must uncomment the line below:
.\Files\Optional\"SSL Hardening Registries.ps1"
2.0.0 - Optimize and Harden Windows 10 Deployments
Optimizing and Hardening Windows 10 Deployments
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
The script may be launched from the extracted GitHub download like this:
.\W10-Optimize-and-Harden-master\installallstandalone.ps1
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
In order to enable the Windows 10 VDI Optimizations you must uncomment the line below:
.\Scripts\"Debloating, Optimization, and Privacy"\"Windows_10_VDI"\1909_WindowsUpdateEnabled\Win10_1909_VDI_Optimize.ps1
In order to enable the SSL Hardening you must uncomment the line below:
.\Scripts\"Security, Hardening, and Mitigation"\"SSL Hardening Registries.ps1"
1.0.5 - Optimize and Harden Windows 10 Deployments
Optimizing and Hardening Windows 10 Deployments
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
In order to enable the Windows 10 VDI Optimizations you must uncomment the line below:
.\Scripts\"Debloating, Optimization, and Privacy"\"Windows_10_VDI"\1909_WindowsUpdateEnabled\Win10_1909_VDI_Optimize.ps1
In order to enable the SSL Hardening you must uncomment the line below:
.\Scripts\"Security, Hardening, and Mitigations"\"SSL Hardening Registries.ps1"
The script may be launched from the extracted GitHub download like this:
.\W10-Optimize-and-Harden-master\installallstandalone.ps1
Or with the optional executable
.\W10-Optimize-and-Harden-master\installallstandalone.exe
1.0.0 - Optimize and Harden Windows 10 Deployments
Optimizing and Hardening Windows 10 Deployments
The script we will be using must be launched from the directory containing all the other files from the GitHub Repository
In order to enable the Windows 10 VDI Optimizations you must uncomment the line below:
.\Scripts\"Debloating, Optimization, and Privacy"\"Windows_10_VDI"\1909_WindowsUpdateEnabled\Win10_1909_VDI_Optimize.ps1
In order to enable the SSL Hardening you must uncomment the line below:
.\Scripts\"Security, Hardening, and Mitigations"\"SSL Hardening Registries.ps1"
The script may be lauched from the extracted GitHub download like this:
.\W10-Optimize-and-Harden-master\installallstandalone.ps1