This integration is focusing on the automated threat intelligence collection with McAfee ATD, OpenDXL and MISP. McAfee Advanced Threat Defense (ATD) will produce local threat intelligence that will be pushed via DXL. An OpenDXL wrapper will subscribe and parse indicators ATD produced and will import indicators into a threat intelligence management platform (MISP). The wrapper will also upload the ATD PDF report and original detonated sample to MISP.
McAfee Advanced Threat Defense (ATD) is a malware analytics solution combining signatures and behavioral analysis techniques to rapidly identify malicious content and provides local threat intelligence. ATD exports IOC data in STIX format in several ways including the DXL. https://www.mcafee.com/in/products/advanced-threat-defense.aspx
MISP threat sharing platform is free and open source software helping information sharing of threat and cyber security indicators. https://github.com/MISP/MISP
Download the Latest Release
- Extract the release .zip file
MISP platform installation (Link) (tested with MISP 2.4.116)
Requests (Link)
PyMISP library installation (Link)
git clone https://github.com/MISP/PyMISP.git
cd PyMISP/
python setup.py installOpenDXL SDK (Link)
git clone https://github.com/opendxl/opendxl-client-python.git
cd opendxl-client-python/
python setup.py installCertificate Files Creation (Link). DXL 4.x support a simplyfied way to create certificates (Link).
McAfee ATD solution (tested with ATD 4.6.2)
McAfee ATD receives files from multiple sensors like Endpoints, Web Gateways, Network IPS or via Rest API. ATD will perform malware analytics and produce local threat intelligence. After an analysis every indicator of comprise will be published via the Data Exchange Layer (topic: /mcafee/event/atd/file/report).
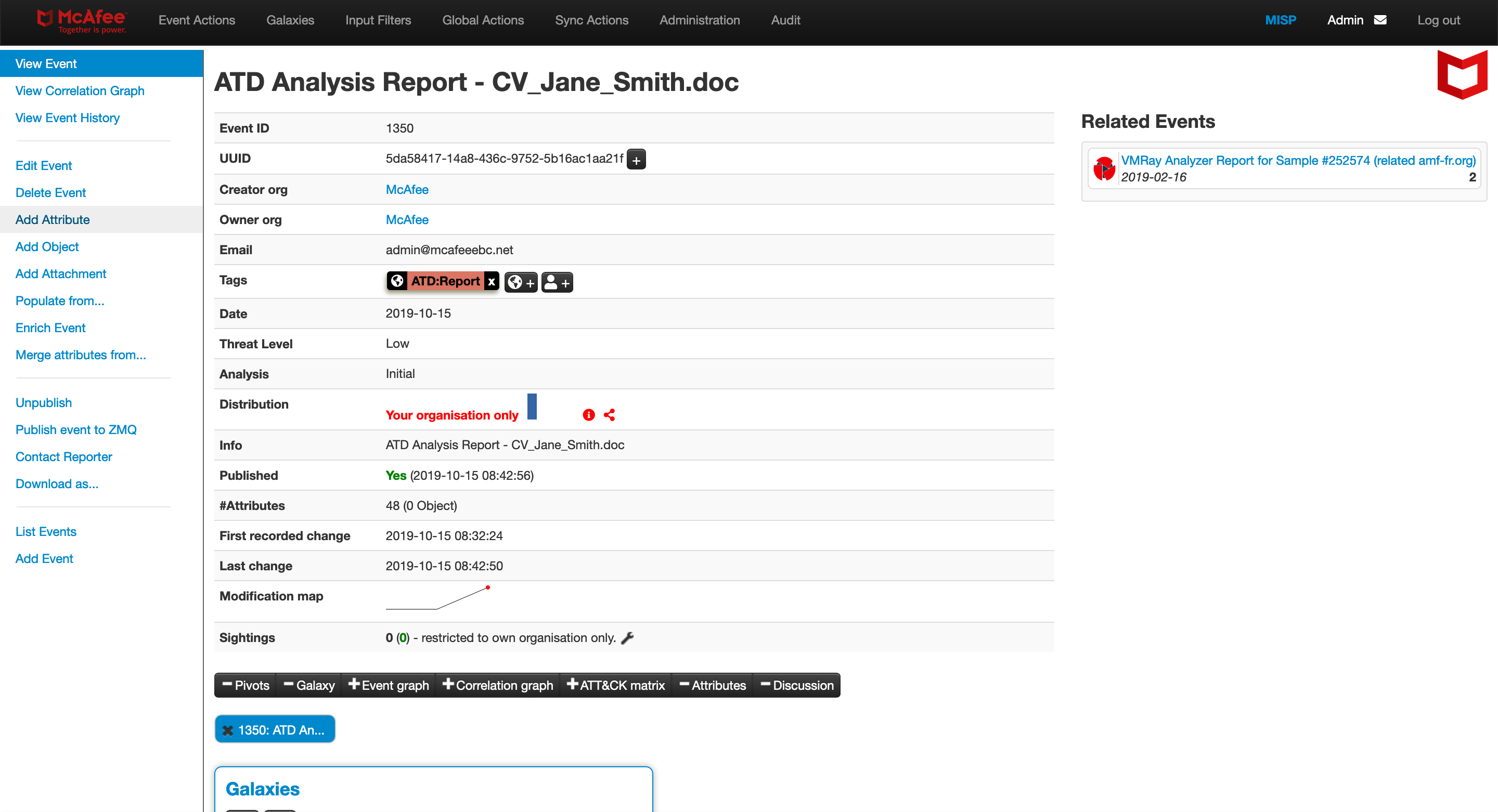
The script will subscribe to the DXL messaging fabric to retrieve McAfee ATD analysis results. Additionally the script will parse IOCs and use the API from MISP (PyMISP) to create a new threat event, add atributes and assign a tag.
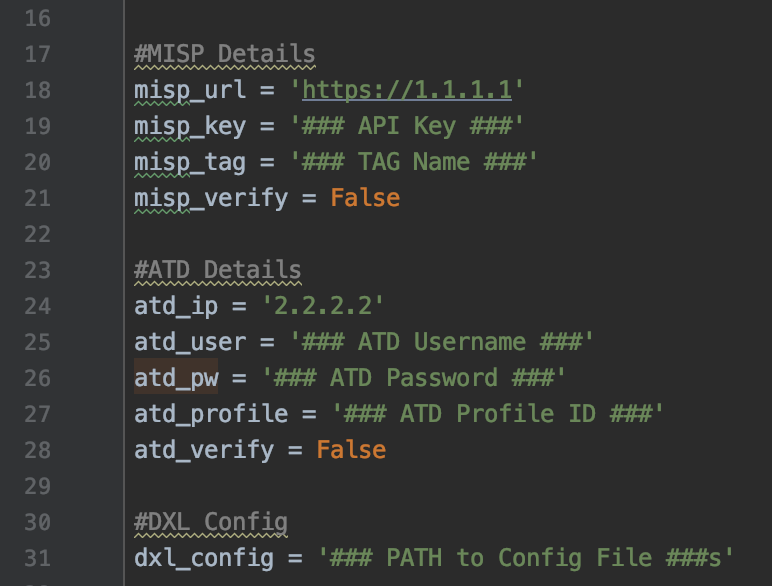
Change the following information
The misp.py script will also download the PDF and original detonated sample from ATD and upload it to MISP. Make sure that the ATD user specified in line 25 is authorized to download reports and samples.
python3 atd_misp.py
or
nohup python3 atd_misp.py &
With this use case, ATD produces local intelligence and contributes information to an intelligence management platform like MISP. MISP is able to aggregate global, community and locally produced intelligence.