An easy way to make your Security Operations Center (SOC) analyst life easier. Instead of asking them to pivot to another screen to run a repeatable query against a table and pull the results back into Sentinel, have them run this very basic logic app. This logic app can be configured to be ran manually or automatically when the incident is generated by the system and provide an output that is ledgable in order to allow the analyst to make a quick determination / validation.
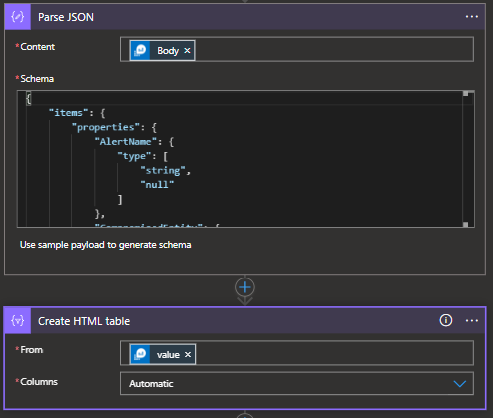
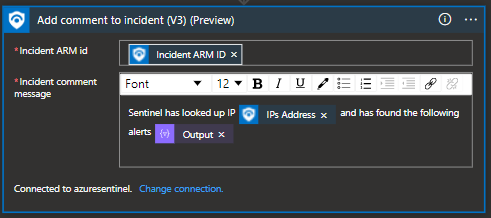
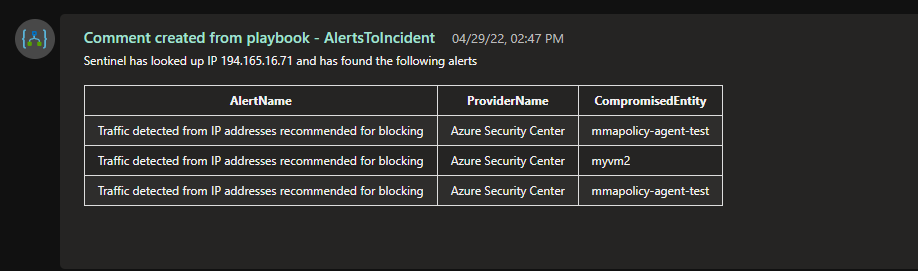
In this example, the logic app will read the incident, grab the IP addresses associated, and query each of the IPs against the Log Analytics workspace "SecurityAlert" table to pull back the AlertName, ProviderName, CompromisedEntity. The results will be parsed into a json, then formatted to an HTML table, and written to the comments.
Note: functionality exist to pull other entity types such as URLs, hostnames, etc. In addition, any column in the "SecurityAlert" table can be added to the query so it is outputed to the comments such as "Message" or "TimeGenerated".
This image the highlevel steps taken to complete this task. Remember, the query will need to be crafted for your specific use case. I do recommend making the query very specific so you don't exceed the comment limit of 30,000. This is a common error I made when my query was over a 24hr period and the logic app continued to fail.
Each of the subsequent screenshots displays an example of the value / fields required.
*Note: It is always good practice to run this logic app first with the thoughts it will fail. It will give you the parse json you need to insert into the parse json "raw output" field. Additionally, it is mission critical that if you have a loop in your logic app that you add the value of "null" into the "Type" of the Json. This does not add by default.
Below you see the basic output when the logic app is ran.
Enjoy and let me know if you have any feedback.