Releases: guardicore/monkey
Infection Monkey v2.3.0
Highlights
Objective
This release is focused on adding high-value features to Infection Monkey.
New Features
Propagation via RDP
Infection Monkey can now use RDP to propagate itself to Windows targets. According to The DFIR Report's 2022 Year in Review, 41.2% of lateral movement occurs via RDP. Infection Monkey users can now simulate this behavior in their environments and ensure they are prepared to detect and handle it.
Cryptojacker simulation
A new cryptojacker payload has been added that performs cryptographic functions with the goal of consuming a configurable amount of CPU. It can also consume a configurable quantity of RAM, as well as simulate some bitcoin mining traffic.
Steal credentials from Chrome
Credentials can be stolen from Chrome-based browsers and used for lateral movement. On Windows hosts, credentials can be stolen from Chrome and Edge. On Linux hosts, credentials can be stolen from Chrome and Chromium.
Plugin installation menu
Infection Monkey provides capabilities for exploitation/propagation, credentials stealing, and payloads via plugins. These plugins are now installable from a remote repository. This results in some highly impactful advantages for users.
- Users can receive and use new features without completely reinstalling Infection Monkey.
- Users can receive bug fixes in certain modules without completely reinstalling Infection Monkey.
- Users can choose not to install certain plugins, eliminating the risk of certain kinds of misconfigurations. This makes Infection Monkey safer in mission-critical environments.
Changelog
Added
- Ability to filter Agent events by timestamp. #3397
- Ability to filter Agent events by tag. #3396
- Provide a common server object to the plugins that can be used to serve agent
binaries to the exploited machine over HTTP. #3410 - CPUConsumptionEvent. #3411
- RAMConsumptionEvent. #3411
- HTTPRequestEvent. #3411
- DefacementEvent. #1247
- RDP exploiter plugin. #3425
- A cryptojacker payload to simulate cryptojacker attacks. #3411
PUT /api/install-agent-plugin. #3417GET /api/agent-plugins/installed/manifests. #3424GET /api/agent-plugins/available/index. #3420POST /api/uninstall-agent-plugin# 3422- Chrome credentials collector plugin. #3426
- A plugin interface for payloads. #3390
- The ability to install plugins from an online repository. #3413, #3418, #3616
- Support for SMBv2+ in SMB exploiter. #3577
- A UI for uploading agent plugin archives. #3417, #3611
Changed
- Plugin source is now gzipped. #3392
- Allowed characters in Agent event tags. #3399, #3676
- Hard-coded Log4Shell exploiter to a plugin. #3388
- Hard-coded SSH exploiter to a plugin. #3170
- Identities and secrets can be associated when configuring credentials in the
UI. #3393 - Hard-coded ransomware payload to a plugin. #3391
- Text on the registration screen to improve clarity. #1984
Fixed
- Agent hanging if plugins do not shut down. #3557
- WMI exploiter hanging. #3543
- Discovered network services are displayed in reports. #3000
Removed
Security
- Fixed a ReDoS issue when validating ransomware file extensions. #3391
New contributors 🙌
Welcome and thanks to our new contributors:
@Akhil-Sharma30
@Mishrasubha
Infection Monkey v2.2.1
Infection Monkey v2.2.0
Highlights
Objective
In Infection Monkey v2.2.0, a long-standing objective has been achieved: Windows users can now install the Infection Monkey Island without encountering warnings or errors from their antivirus solutions*. Additionally, the Infection Monkey Agents may also go undetected in some circumstances. Since Infection Monkey Agents behave similarly to malware, it is expected that host-based antivirus or EDR solutions may be triggered by certain behaviors.
New Features
-
Polymorphic and metamorphic malware modify each copy of themselves in order to evade signature-based detection mechanisms. This results in each copy of the malware having a unique hash. A new feature has been added that, if enabled, allows Infection Monkey Agents to emulate this property by including unique data within the each copy of the Agent binary.
-
A common way of detecting and identifying an executable as malware is to write a detection rule (such as for a tool like YARA) that checks for the existence of strings or unique byte sequences within a file. The newly-added Malware Masquerade feature allows users to specify strings (characters) or arbitrary data (bytes) that will be injected into the Agent binaries. This allows Infection Monkey Agents to masquerade as specific types of malware. This is particularly useful for anyone who writes their own detection rules and needs a way to test them, or anyone looking to improve the fidelity of malware simulations.
Improvements
-
Credentials collectors can now be written as plugins** loaded by Infection Monkey at runtime. This flexibility will allow for the development and delivery of more credentials collection/theft techniques in the near future. . Furthermore, enhancements to the SSH credentials collector make it more adept at collecting SSH keys to be used for propagation.
-
Several bugs have been fixed, including a critical issue that caused agents spawned by the SMB exploiter to crash.
Footnotes
* Infection Monkey has been tested with various common antivirus/EDR solutions. While some solutions may still raise errors, our testing has not identified any specific issues.
** Please note that plugin interfaces are still considered experimental. They will be documented and made available to users in a future release.
Changelog
Added
PortScanData.openproperty. #3238{GET,PUT} /api/agent-binaries/<string:os>/masque. #3249- Placeholder values for empty plugin configuration fields having defaults. #3310
- Malware masquerading. #3241, #3242, #3243
- Support for plugin manifest files with the "yml" extension. #3097
- Randomize Agent binary hash (polymorphism) feature. #3244
- Agent binary's SHA256 to
AgentRegistrationData. #3244 EmailAddressidentity type. #3270- SNMP exploiter (CVE-2020-15862). #3234
- A plugin interface for credentials collectors. #3167
Changed
- Renamed "Credential collector" to "Credentials collector". #3167
- Hard-coded WMI exploiter to a plugin. #3163
- Hard-coded Mimikatz credentials collector to a plugin. #3168
- Hard-coded Zerologon exploiter to a plugin. #3164
- Hard-coded SSH credentials collector to a plugin. #3169
- SSH credentials collector's private-key search algorithm. #1882
- Manual run command includes all Island IP addresses. #2593
- Hard-coded MSSQL exploiter to a plugin. #3171
- Hard-coded PowerShell exploiter to a plugin. #3165
Fixed
- Agents were being caught by Windows Defender (and other antiviruses). #1289
- Plugins are now being checked for local OS compatibility. #3275
- A bug that could prevent multi-hop propagation via SMB. #3173
- Exceptions being raised when WMI and Zerologon are used together. #1774
- A bug that caused failing configuration imports to be marked as successful. #3341
- A bug where target hostnames with dashes were not being scanned. #3231
- A bug in URL sanitization. #3318
Security
Infection Monkey v2.1.0
Highlights
Infection Monkey version 2.1.0 introduces security, user experience, and tech stack enhancements.
Security
- All API endpoints now require authentication and authorization.
- Users can now log out.
- Minor security weaknesses, such as a local DoS error and a potential XSS vulnerability, have been mitigated.
User Experience
- Users are no longer logged out of the Web UI while working. They will be logged out automatically only when idle.
- Brute force exploitation using stolen credentials is now faster.
- The Docker image can now be installed simply with
sudo docker pull infectionmonkey/monkey-island:latest.
Tech Stack
- The Island and Agent have been upgraded from Python 3.7 to 3.11.2.
- The MongoDB dependency has been upgraded from version 4.x to 6.x.
Changelog
Added
- Logout button. #3063
- An option to the Hadoop exploiter to try all discovered HTTP ports. #2136
GET /api/agent-otp. #3076POST /api/agent-otp-loginendpoint. #3076- A smarter brute-forcing strategy for SMB exploiter. #3039
POST /api/refresh-authentication-tokenendpoint that allows refreshing of
the access token. #3181
Changed
- Migrated the hard-coded SMB exploiter to a plugin. #2952
- Python version from 3.7 to 3.11.2. #2705
- MSI installer is now build with InnoSetup. #1911
Fixed
- A UI deficiency where invalid configurations could be submitted to the
backend. #1301, #2989 - Notification spam bug. #2731
- Agent propagator crashes if exploiters malfunction. #2992
- Configuration order not preserved in debugging output. #2860
- A bug in the Hadoop exploiter that resulted in speculative execution of
multiple agents. #2758 - Formatting of the manual run command when copy/pasting from the web UI. #3115
- A bug where plugins received an incorrect agent ID. #3119
- Random logouts when the UI is being actively used. #2049, #3079, #3137
Security
- Fixed plaintext private key in SSHKey pair list in UI. #2950
- Upgraded MongoDB version from 4.x to 6.0.4. #2706
- Replaced the
SystemSingletoncomponent, which could allow local users to
execute a DoS attack against agents. #2817 - Replaced our bespoke authentication solution with
flask-security-too.
#2049, #2157, #3078, #3138 - Enforced access control around sensitive API endpoints. #2049, #2157
- Upgraded 3rd-party dependencies. #2705, #2970, #2865, #3125
- Fixed a potential XSS issue in exploiter plugins. #3081
Infection Monkey v2.0.0
Highlights
Change in mission
Infection Monkey began as means of vulnerability assessment, producing recommendations for improving network security.
The new mission focuses on adversary emulation. Organizations employ many measures to maintain network security. The only way for them to know whether or not these measures are working, and their networks are safe, is by testing. The basic assumption should be: if it’s not tested- it’s broken.
Infection Monkey is malware you can control, designed to be safe for production environments. It provides safe testing by emulating adversaries’ attacks to ensure that the security measures employed by the organization are not broken and, indeed, provide the necessary level of security.
In summary, v2.0.0 of Infection Monkey constitutes a shift in focus from vulnerability scanning and breach & attack simulation to adversary emulation.
Performance and overall simulation time
Infection Monkey is now faster and more reliable than ever before, as over 75 bugs were resolved. Notably, a longstanding issue that prevented Infection Monkey from stopping on command has been resolved. Thus, you can now ensure your network’s safety, with greater confidence, speed, and control.
Enhanced security
6 minor security weaknesses have been resolved as part of an effort to harden and secure Infection Monkey itself. Among these, we have upgraded some dependencies to newer, more secure versions.
A streamlined feature set
We reduced feature bloating by removing outdated exploitation techniques, as well as some reporting and scanning features that do not support our new mission. The existing features are now more robust and intuitive, ensuring better testing and faster results.
Changes to the API
We have redesigned the API to prepare to shift from private API to public API. Documentation will follow in the near future.
Changelog
Added
credentials.jsonfile for storing Monkey Island user login information. #1206GET /api/propagation-credentials/<string:guid>endpoint for agents to
retrieve updated credentials from the Island. #1538GET /api/island/ip-addressesendpoint to get IP addresses of the Island server
network interfaces. #1996- SSHCollector as a configurable System info Collector. #1606
- deployment_scrips/install-infection-monkey-service.sh to install an AppImage
as a service. #1552 - The ability to download the Monkey Island logs from the Infection Map page. #1640
POST /api/reset-agent-configurationendpoint. #2036POST /api/clear-simulation-dataendpoint. #2036GET /api/registration-statusendpoint. #2149- Authentication to
/api/island/version. #2109 - The ability to customize the file extension used by the ransomware payload
when encrypting files. #1242 {GET,POST} /api/agentsendpoint. #2362GET /api/agent-signalsendpoint. #2261GET /api/agent-logs/<uuid:agent_id>endpoint. #2274GET /api/machinesendpoint. #2362{GET,POST} /api/agent-eventsendpoints. #2405GET /api/nodesendpoint. #2155, #2300, #2334- Scrollbar to preview pane's exploit timeline in the map page. #2455
GET /api/agent-plugins/<string:os>/<string:type>/<string:name>endpoint. #2578, #2811GET /api/agent-configuration-schemaendpoint. #2710GET /api/agent-plugins/<string:type>/<string:name>/manifestendpoint. #2786GET /api/agent-binaries/<string:os>endpoint. #1675, #1978
Changed
- Reset workflow. Now it's possible to delete data gathered by agents without
resetting the configuration. Additionally, the reset procedure requires fewer
clicks. #957 - Reduced the map refresh rate from 5 seconds to 1.
- Cleaned up and removed duplication in the security report. #2885
- The setup procedure for custom
server_config.jsonfiles to be simpler. #1576 - The order and content of Monkey Island's initialization logging to give
clearer instructions to the user and avoid confusion. #1684 - The
GET /api/monkey/downloadto `GET /api/agent-binaries/string:os. #1675, #1978 - Log messages to contain human-readable thread names. #1766
- The log file name to
infection-monkey-agent-<TIMESTAMP>-<RANDOM_STRING>.log. #1761 - "Logs" page renamed to "Events". #1640, #2501
- Analytics and version update queries are sent separately instead of just one query. #2165
- Update MongoDB version to 4.4.x. #1924
- Depth flag (-d) on the agent now acts the way you would expect (it represents
the current depth of the agent, not hops remaining). #2033 - Agent configuration structure. #1996, #1998, #1961, #1997, #1994, #1741,
#1761, #1695, #1605, #2028, #2003, #2785 /api/island-modeto accept and return new "unset" mode. #2036/api/version-updatetoapi/island/version. #2109/api/island-modeto/api/island/mode. #2106/api/log/island/downloadendpoint to/api/island/log. #2107/api/authendpoint to/api/authenticate. #2105/api/registrationendpoint to/api/register. #2105- Improved the speed of ransomware encryption by 2-3x. #2123
-s/--serverto-s/--servers. #2216-s/--serversaccepts list a comma-separated list of servers. #2216- Tunneling to relays to provide better firewall evasion, faster Island
connection times, unlimited hops, and a more resilient way for agents to call
home. #2216, #1583 /api/monkey-control/stop-all-agentstoPOST /api/agent-signals/terminate-all-agents. #2261- Format of scanned machines table in the security report. #2267
- "Local network scan" option to "Scan Agent's networks". #2299
- Information displayed in the preview pane in the map page. #2455
- The Hadoop exploiter to a plugin. #2826
- The Guardicore logo to Akamai logo. #2913
Removed
- VSFTPD exploiter. #1533
- Manual agent run command for CMD. #1556
- Sambacry exploiter. #1567, #1693
- "Kill file" option in the config. #1536
- Netstat collector, because network connection information wasn't used anywhere. #1535
- Checkbox to disable/enable sending log to server. #1537
- Checkbox for self deleting a monkey agent on cleanup. #1537
- Checkbox for file logging. #1537
- Serialization of config. #1537
- Checkbox that gave the option to not try to first move the dropper file. #1537
- Custom singleton mutex name config option. #1589
- Environment system info collector #1535
- Azure credential collector, because it was broken (not gathering credentials). #1535
- Custom monkey directory name config option. #1537
- Hostname system info collector. #1535
- Max iterations config option. #1600
- Timeout between iterations config options. #1600
- MITRE ATT&CK configuration screen. #1532
- Propagation credentials from
GET /api/monkey/<string:guid>endpoint. #1538 GET /api/monkey_control/check_remote_port/<string:port>endpoint. #1635- Max victims to find/exploit, TCP scan interval and TCP scan get banner internal options. #1597
- MySQL fingerprinter. #1648
- MS08-067 (Conficker) exploiter. #1677
- Agent bootloader. #1676
- Zero Trust integration with ScoutSuite. #1669
- ShellShock exploiter. #1733
- ElasticGroovy exploiter. #1732
- T1082 attack technique report. #1695
- 32-bit agents. #1675
- Log path config options. #1761
- "smb_service_name" option. #1741
- Struts2 exploiter. #1869
- Drupal exploiter. #1869
- WebLogic exploiter. #1869
- The /api/t1216-pba/download endpoint. #1864
/api/test/clear_cachesendpoint. #1888, #2092- All
/api/monkey_controlendpoints. #1888, #2261 - Island log download button from "Events" (previously called "Logs") page. #1640
/api/client-monkeyendpoint. #1889- "+dev" from version numbers. #1553
- agent's
--configargument. #906 - Option to export monkey telemetries. #1998
/api/configuration/importendpoint. #2002/api/configuration/exportendpoint. #2002/api/island-configurationendpoint. #2003-t/--tunnelfrom agent command line arguments. #2216/api/monkey-control/needs-to-stop. #2261GET /api/test/monkeyendpoint. #2269GET /api/test/logendpoint. #2269- Node Map from Security Report. #2334
- "Accessible From" and "Services" from the preview pane in the map page. #2430
- All
GET /api/netmapendpoints. #2334, #2453 - The MITRE ATT&CK report. #2440
- The Zero Trust report. #2441
GET /api/zero-trust/finding-event/<string:finding_id>endpoint. #2441
-"GET /api/report/zero-trust/<string:report_data>endpoint. #2441- AWS Security Hub integration. #2443
- The Post breach actions configuration tab. #2442
- The Custom PBA configuration tab. #2442
- All
/api/pbaendpoints. #2442 - The TelemetryLog component from the Infection Map page. #2500
GET /api/telemetry-feedendpoint. #2502{GET,POST} /api/logendpoint. #2485GET /api/local-monkeyendpoint. #2506/api/telemetryendpoint. #2503/api/agentendpoint. #2542/api/exploitations/manualendpoint. #2509/api/island/ip-addressesendpoint. #2565- ElasticSearch fingerprinter. #2674
Fixed
- Various bugs that prevented agents from stopping reliably. #556, #578, #581,
#594, #1635, #2261 - A bug in the network map where it would drift away and
improved overall stability of the map. #2939 - Windows "run as a user" powershell command for manual agent runs. #1556
- A bug in the map where side pane would not appear if the node was
dragged around before click. #2914 - Unnecessary collection of kerberos credentials. #1771
- A bug where bogus users were collected by Mimikatz and added to the config. #1860
- A bug where windows executable was not self deleting. #1763
- 2-second delay when the Island server starts, and it's not running on AWS. #1636
- Malformed MSSQL agent launch command. #2018
- A bug where the Log4Shell exploiter could leave LDAP servers and child
processes running. #2820 - A bug in registration process that caused the button to be stuck with ...
Infection Monkey v1.13.0
This release adds a new exploiter to the Infection Monkey, which exploits the Log4Shell vulnerability (CVE-2021-44228). To start downloading it while you read the release notes, go to the Infection Monkey website.
Changelog
Added
- A new exploiter that allows propagation via the Log4Shell vulnerability
(CVE-2021-44228). #1663
Fixed
- Exploiters attempting to start servers listening on privileged ports,
resulting in failed propagation. 8f53a5c
Attached binaries and hashes:
| Filename | Type | Version | SHA256 Hash |
|---|---|---|---|
| InfectionMonkey-v1.13.0.AppImage | Island | 1.13.0 | cded4e8394a4d2a809ba9b74b924aea590317515b9b032ba8005a93dfce1c861 |
| monkey-linux-32 | agent | 1.13.0 | 24c5779825f26c76a8910794836647096f4bb4b47cfd6ad213cc48116d140fab |
| monkey-linux-64 | agent | 1.13.0 | f21e709cb7ba8daf90b908af5fe485ba43866c325d3c7ce1eb07e8a2323e07c1 |
| monkey-windows-32 | agent | 1.13.0 | 7497907e3cf4ffeb121a7795bfa16709800e6e0f99770f64af7fff684ecba6d6 |
| monkey-windows-64 | agent | 1.13.0 | 3edd20de2247047c8a822c84145981936ce2fd0bdf843eb5ca777ca4d2478b35 |
| sc_monkey_runner32.so | sambacry | 68fd441c92f9d2c3201f7072eafbe9a4c56339139395daeba959836bd3f8b212 | |
| sc_monkey_runner64.so | sambacry | 94e1d1ac64bfc4a63f590f8add21c10f26b2b0ffb6b69518ed2c53909c8faf18 |
Infection Monkey v1.12.0
This release enhances Infection Monkey's ransomware simulation capability by adding the ability to propagate via PowerShell remoting. It also provides numerous bug fixes, as well as UX and security improvements. To start downloading it while you read the release notes, go to the Infection Monkey website.
Changelog
Added
- A new exploiter that allows propagation via PowerShell Remoting. #1246
- A warning regarding antivirus when agent binaries are missing. #1450
- A deployment.json file to store the deployment type. #1205
Changed
- The name of the "Communicate as new user" post-breach action to "Communicate
as backdoor user". #1410 - Resetting login credentials also cleans the contents of the database. #1495
- ATT&CK report messages (more accurate now). #1483
- T1086 (PowerShell) now also reports if ps1 scripts were run by PBAs. #1513
- ATT&CK report messages to include internal config options as reasons
for unscanned attack techniques. #1518
Removed
- Internet access check on agent start. #1402
- The "internal.monkey.internet_services" configuration option that enabled
internet access checks. #1402 - Disused traceroute binaries. #1397
- "Back door user" post-breach action. #1410
- Stale code in the Windows system info collector that collected installed
packages and WMI info. #1389 - Insecure access feature in the Monkey Island. #1418
- The "deployment" field from the server_config.json. #1205
- The "Execution through module load" ATT&CK technique,
since it can no longer be exercise with current code. #1416 - Browser window pop-up when Monkey Island starts on Windows. #1428
Fixed
- Misaligned buttons and input fields on exploiter and network configuration
pages. #1353 - Credentials shown in plain text on configuration screens. #1183
- Crash when unexpected character encoding is used by ping command on German
language systems. #1175 - Malfunctioning timestomping PBA. #1405
- Malfunctioning shell startup script PBA. #1419
- Trap command produced no output. #1406
- Overlapping Guardicore logo in the landing page. #1441
- PBA table collapse in security report on data change. #1423
- Unsigned Windows agent binaries in Linux packages are now signed. #1444
- Some of the gathered credentials no longer appear in plaintext in the
database. #1454 - Encryptor breaking with UTF-8 characters. (Passwords in different languages
can be submitted in the config successfully now.) #1490 - Mimikatz collector no longer fails if Azure credential collector is disabled.
#1512, #1493 - Unhandled error when "modify shell startup files PBA" is unable to find
regular users. #1507 - ATT&CK report bug that showed different techniques' results under a technique
if the PBA behind them was the same. #1514 - ATT&CK report bug that said that the technique "
.bash_profileand
.bashrc" was not attempted when it actually was attempted but failed. #1511 - Bug that periodically cleared the telemetry table's filter. #1392
- Crashes, stack traces, and other malfunctions when data from older versions
of Infection Monkey is present in the data directory. #1114 - Broken update links. #1524
Security
- Generate a random password when creating a new user for CommunicateAsNewUser
PBA. #1434 - Credentials gathered from victim machines are no longer stored plaintext in
the database. #1454 - Encrypt the database key with user's credentials. #1463
New contributors 🙌
Welcome and thanks to our new contributors:
@TRGamer-tech
Attached binaries and hashes:
| Filename | Type | Version | SHA256 Hash |
|---|---|---|---|
| InfectionMonkey-v1.12.0.AppImage | island | 1.12.0 | 1325f2aa1d0c27aec2e2f9864ed53c53c524bd208313f87ea6606f59c90ff310 |
| monkey-linux-32 | agent | 1.12.0 | d941943046db48cf0eb7f11e144a79749848ae6b50014833c5390936e829f6c3 |
| monkey-linux-64 | agent | 1.12.0 | 1ad52eabd704a9b0fbf642fa552629f30d3c5c27e431a687bd4cba4e0104d3f7 |
| monkey-windows-32 | agent | 1.12.0 | 3c10f610f47c4fd227cf85f6bf800d66ed31fe37dc2e2ed408860483685ba504 |
| monkey-windows-64 | agent | 1.12.0 | 02e5e051a96e2ca61ae8e661b3a5828ee53a0fc00aca6502d5c73a46754f0d07 |
| sc_monkey_runner32.so | sambacry | 68fd441c92f9d2c3201f7072eafbe9a4c56339139395daeba959836bd3f8b212 | |
| sc_monkey_runner64.so | sambacry | 94e1d1ac64bfc4a63f590f8add21c10f26b2b0ffb6b69518ed2c53909c8faf18 |
Infection Monkey v1.11.0
This release introduces Infection Monkey's ransomware simulation capability. It also adds a number of security enhancements and configuration options. To start downloading it while you read the release notes, go to the Infection Monkey website.
Changelog
Added
- A runtime-configurable option to specify a data directory where runtime configuration and other artifacts can be stored. #994
- Scripts to build an AppImage for Monkey Island. #1069, #1090, #1136, #1381
log_leveloption to server config. #1151- A ransomware simulation payload. #1238
- The capability for a user to specify their own SSL certificate. #1208
- API endpoint for ransomware report. #1297
- A ransomware report. #1240
- A script to build a docker image locally. #1140
Changed
- Select server_config.json at runtime. #963
- Select Logger configuration at runtime. #971
- Select
mongo_key.binfile location at runtime. #994 - Store Monkey agents in the configurable data_dir when monkey is "run from the island". #997
- Reformat all code using black. #1070
- Sort all imports using isort. #1081
- Address all flake8 issues. #1071
- Use pipenv for python dependency management. #1091
- Move unit tests to a dedicated
tests/directory to improve pytest collection time. #1102 - Skip BB performance tests by default. Run them if
--run-performance-testsflag is specified. - Write Zerologon exploiter's runtime artifacts to a secure temporary directory instead of $HOME. #1143
- Put environment config options in
server_config.jsoninto a separate section named "environment". #1161 - Automatically register if BlackBox tests are run on a fresh installation. #1180
- Limit the ports used for scanning in blackbox tests. #1368
- Limit the propagation depth of most blackbox tests. #1400
- Wait less time for monkeys to die when running BlackBox tests. #1400
- Improve the structure of unit tests by scoping fixtures only to relevant modules instead of having a one huge fixture file. #1178
- Improve and rename the directory structure of unit tests and unit test infrastructure. #1178
- Launch MongoDB when the Island starts via python. #1148
- Create/check data directory on Island initialization. #1170
- Format some log messages to make them more readable. #1283
- Improve runtime of some unit tests. #1125
- Run curl OR wget (not both) when attempting to communicate as a new user on Linux. #1407
Removed
- Relevant dead code as reported by Vulture. #1149
- Island logger config and --logger-config CLI option. #1151
Fixed
- Attempt to delete a directory when monkey config reset was called. #1054
- An errant space in the windows commands to run monkey manually. #1153
- Gevent tracebacks in console output. #859
- Crash and failure to run PBAs if max depth reached. #1374
Security
- Address minor issues discovered by Dlint. #1075
- Hash passwords on server-side instead of client side. #1139
- Generate random passwords when creating a new user (create user PBA, ms08_67 exploit). #1174
- Implemented configuration encryption/decryption. #1189, #1204
- Create local custom PBA directory with secure permissions. #1270
- Create encryption key file for MongoDB with secure permissions. #1232
New contributors 🙌
Welcome and thanks to our new contributors:
@ilija-lazoroski
@kur1mi
@Vertrauensstellung
Attached binaries and hashes:
| Filename | Type | Version | SHA256 Hash |
|---|---|---|---|
| Infection_Monkey-1.11.0-x86_64.AppImage | island | 1.11.0 | 6312b6bff18c11c7db694f42cf5a41e894786c39e3e093b6b15abcbff80337f2 |
| monkey-linux-32 | agent | 1.11.0 | b0615fc0369bf6f0900e89acbc300cfe63bc754e4e3d50c2cba2dbdb2de8e511 |
| monkey-linux-64 | agent | 1.11.0 | fb4c979ce6c29bb458be50a44cc6839650826b831da849da69a05dfefdc66462 |
| monkey-windows-32 | agent | 1.11.0 | e006b26663f59b92bad8d49b034cd8101dd481f881e3c4839a9c1e64fd99e849 |
| monkey-windows-64 | agent | 1.11.0 | 12c55377381a8fc7d8ff731db52302ef2f8bb894d8712769e5a91a140ba22b0a |
| sc_monkey_runner32.so | sambacry | 68fd441c92f9d2c3201f7072eafbe9a4c56339139395daeba959836bd3f8b212 | |
| sc_monkey_runner64.so | sambacry | 94e1d1ac64bfc4a63f590f8add21c10f26b2b0ffb6b69518ed2c53909c8faf18 | |
| tracerouter32 | traceroute | c15a8a7612af31ff973d424c6473eb34e2ca66dddc6aef3067a1e9927e368f23 | |
| traceroute64 | sambacry | 64d5c9c9b7c0aaf6447bd6fd439b87052fe72bba769c4de454bc1f817cffcad4 |
Infection Monkey v1.10.0
This release introduces exciting new features, performance improvements, and lots of bug fixes. To start downloading it while you read the release notes, go to the Infection Monkey website.
New Features 🆕
New exploits 💣
Infection Monkey can now exploit two new remote code execution vulnerabilities:
- Exploit CVE-2019-6340 in Drupal #669
- Exploit Zerologon CVE-2020-1472 in Windows domain controllers #846, #868, #998, #1004
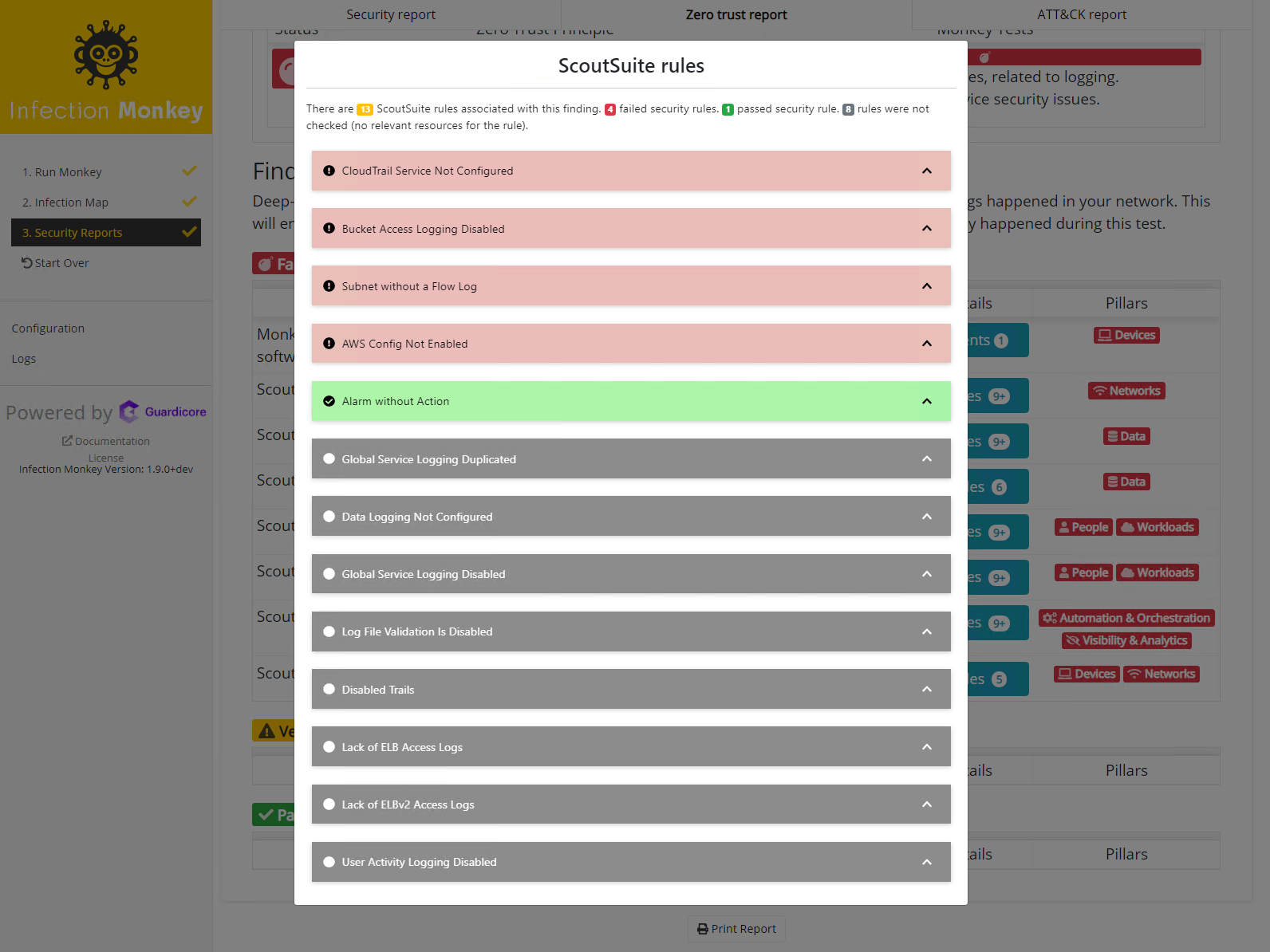
AWS Zero Trust security scans with ScoutSuite 🔍
Scout Suite is an open-source cloud security-auditing tool. It queries the cloud API to gather configuration data. Based on the configuration data gathered, ScoutSuite shows security issues and risks present in your cloud infrastructure. Infection Monkey will run a ScoutSuite scan against your AWS environment and categorize any alerts according to the Zero Trust framework. #519
New MITRE ATT&CK techniques 💥
We're continuing to improve our MITRE ATT&CK capabilities. We've added four new ATT&CK techniques to Infection Monkey, for a total of 36!
- Signed script proxy execution (T1216) #776
- Account discovery(T1087) #793
- Indicator removal on host: timestomp (T1099) #796
- Clear command history (T1146) #799
Improvements ⤴
Secured dependencies using snyk.io
Performance improvements 🚤
- Use multithreading to run PBAs #696
- Refactor tornado WSGE container into gevent WSGI container #858 #862
- Add sane timeouts to reduce excessive blocking #885
Documentation improvements 📖
We've updated our documentation for readability and consistency, as well as added swimm tutorials for developers.
- Improve report documentation #887
- Updates to monkey zoo docs #927
- Copyediting #909 #932 #933 #934 #935 #936 #937 #965
- Swimm tutorials #766 #837 #850 #904
- Add high-level architecture explanation #1047
Miscellaneous
- Add Windows XP support to MS08_067 exploit #809
- Reintroduce AWS run option #865
- Update Linux deployment scripts #900
UI
- Specify a user that will run the infection monkey agent #792 #830 #838 #840
- Clarified cross-segment issue reporting #819
- Improve ATT&CK UI #820
- Modify master checkboxes to conform to human interface guidelines #920
- Provide warning icon and language for unsafe options #920
- Show "None" in zero trust report sections with zero findings #947
- Show confirmation dialog when unsafe config is submitted or imported #1000
- Show warning dialog when unsafe ATT&CK config is submitted #1006
- Clarify custom PBA field descriptions in configuration menu #1027
Bug fixes 🐛
- Scale Monkey Island map component to window size #150
- Center Guardicore logo on smaller screens #612
- Fix typo that caused missing telemetry type on Log page #689
- Redirect to login page when JWT expires #739
- Link related ATT&CK techniques of the same PBA #761
- Fix rendering in security report generation #762
- Fix PBA file upload failure #784
- Evade detection by Windows defender #801, #929
- Fix hang on update check #857
- Fix creation of scheduled jobs (PBA) #861
- Fix wrong initial state in plugin selector control #891
- Fix failing SMB exploiter #895
- Catch exceptions thrown by fingerprinters #897
- Fix logic used to detect AWS, GCP, and Azure cloud instances #902
- Fix uncaught error in ATT&CK report #948
- Fix failure to scan configured TCP ports #956
- Add missing authentication check to
local_runendpoint #981 - Do not automatically execute custom PBA script #1020 #1027
- Fix pyjwt dependency at version 1.7 #1042
- Properly handle unicode decode errors #798
New contributors 🙌
Welcome and thanks to our new contributors:
Attached binaries and hashes:
| Filename | Type | Version | SHA256 Hash |
|---|---|---|---|
| monkey-linux-32 | agent | 1.10.0 | a6de7d571051292b9db966afe025413dc20b214c4aab53e48d90d8e04264f4f5 |
| monkey-linux-64 | agent | 1.10.0 | 932f703510b6484c3824fc797f90f99722e38a7f8956cf6fa58fdecb3790ab93 |
| monkey-windows-32 | agent | 1.10.0 | 8e891e90b11b97fbbef27f1408c1fcad486b19c612773f2d6a9edac5d4cdb47f |
| monkey-windows-64 | agent | 1.10.0 | 3b499a4cf1a67a33a91c73b05884e4d6749e990e444fa1d2a3281af4db833fa1 |
| sc_monkey_runner32.so | sambacry | 68fd441c92f9d2c3201f7072eafbe9a4c56339139395daeba959836bd3f8b212 | |
| sc_monkey_runner64.so | sambacry | 94e1d1ac64bfc4a63f590f8add21c10f26b2b0ffb6b69518ed2c53909c8faf18 | |
| tracerouter32 | traceroute | c15a8a7612af31ff973d424c6473eb34e2ca66dddc6aef3067a1e9927e368f23 | |
| traceroute64 | sambacry | 64d5c9c9b7c0aaf6447bd6fd439b87052fe72bba769c4de454bc1f817cffcad4 |
Infection Monkey v1.9.0
Infection Monkey 1.9.0
This is a BIG, exciting release, with a ton of new features and improvements. To start downloading it while you read the release notes, go to the Infection Monkey website.
New Features 🆕
Improved MITRE ATT&CK coverage and reporting
We're continuing to improve our MITRE ATT&CK capabilities, with many new techniques added and a new report with more information.
New ATT&CK techniques 💥
We've added 8 new ATT&CK techniques to the Monkey, which brings our total coverage to 32!
setuidandsetgid" attack technique (T1166) #702- "Trap" attack technique (T1154) #697
- "PowerShell Profile" attack technique (T1504) #686
- "Scheduled Task" attack technique (T1053) #685
- "Local Job Scheduling" attack technique (T1168) #683
- "
.bash_profileand.bashrc" attack technique (T1156) #682 - "Hidden Files and Directories" attack technique (T1158) #672
- User creation and impersonation attack technique (T1136) #579
New ATT&CK report 📊
The new report added a new status to help you discern WHY a technique was or was not attempted, so you can optimise future Monkey executions. Here's how it looks:
Improved configuration (#637) ⚙
In our effort to improve the user experience and make Monkey more accessible and useable we've revamped our entire Configuration screen! Easily control the credentials used in simulations, the target list the Monkey will scan, and which exploits the Monkey will attempt to use.
Replaced mimikatz DLL with pypykatz for better defence evasion (#471, #583) 💂♂️
Most AVs recognize and delete the Mimikatz DLL or even disrupt the entire Monkey installation process on Windows. We've replaced Mimikatz with pypykatz and for now, it'll be much harder for endpoint protection software to stop the Monkey.
New Documentation site and framework (#602) 📖
Due to the limited control and ease of use of the GitHub wiki, we've decided to move our documentation to a self-hosted solution based on Hugo.
Monkey Island is secure by default (#596) 🔐
The first time you launch Monkey Island (Infection Monkey CC server), you'll be prompted to create an account and secure your island. After your account is created, the server will only be accessible via the credentials you chose.
If you want Island to be accessible without credentials press I want anyone to access the island. Please note that this option is insecure: you should only pick this for use in development environments.
Read related documentation here.
Improvements ⤴
Secured dependencies using snyk.io
We have a new integration with snyk.io, a service which checks our dependencies for vulnerabilities! So we've locked all our dependencies (#627) and updated lots of them as well:
Improvements to our CI process
- Python import linting #727
- Added Snyk.io to our PRs to test if new vulns are added through dependencies
Other improvements
- Edge refactoring to DAL #671
- Revamps UI to bootstrap v4 #688
- Updated MongoDB version #692
- Various Typos fixed #726
Bug fixes 🐛
Everything that was fixed in 1.8.2 and:
- Reset env UI bug #666
- Handle missing binaries #485
- Fixes SMB exploiter not passing vulnerable port (thus causing redundant exploitation) #664
- Removed PTH map #691
New contributors 🙌
Welcome and thanks to our new contributors:
Attached binaries and hashes:
| Filename | Type | Version | Hash |
|---|---|---|---|
| monkey-linux-32 | agent | 1.9.0 | 4c24318026239530ed2437bfef1a01147bb1f3479696eb4eee6009326ce6b380 |
| monkey-linux-64 | agent | 1.9.0 | aec6b14dc2bea694eb01b517cca70477deeb695f39d40b1d9e5ce02a8075c956 |
| monkey-windows-32 | agent | 1.9.0 | 67f12171c3859a21fc8f54c5b2299790985453e9ac028bb80efc7328927be3d8 |
| monkey-windows-64 | agent | 1.9.0 | 24622cb8dbabb0cf4b25ecd3c13800c72ec5b59b76895b737ece509640d4c068 |