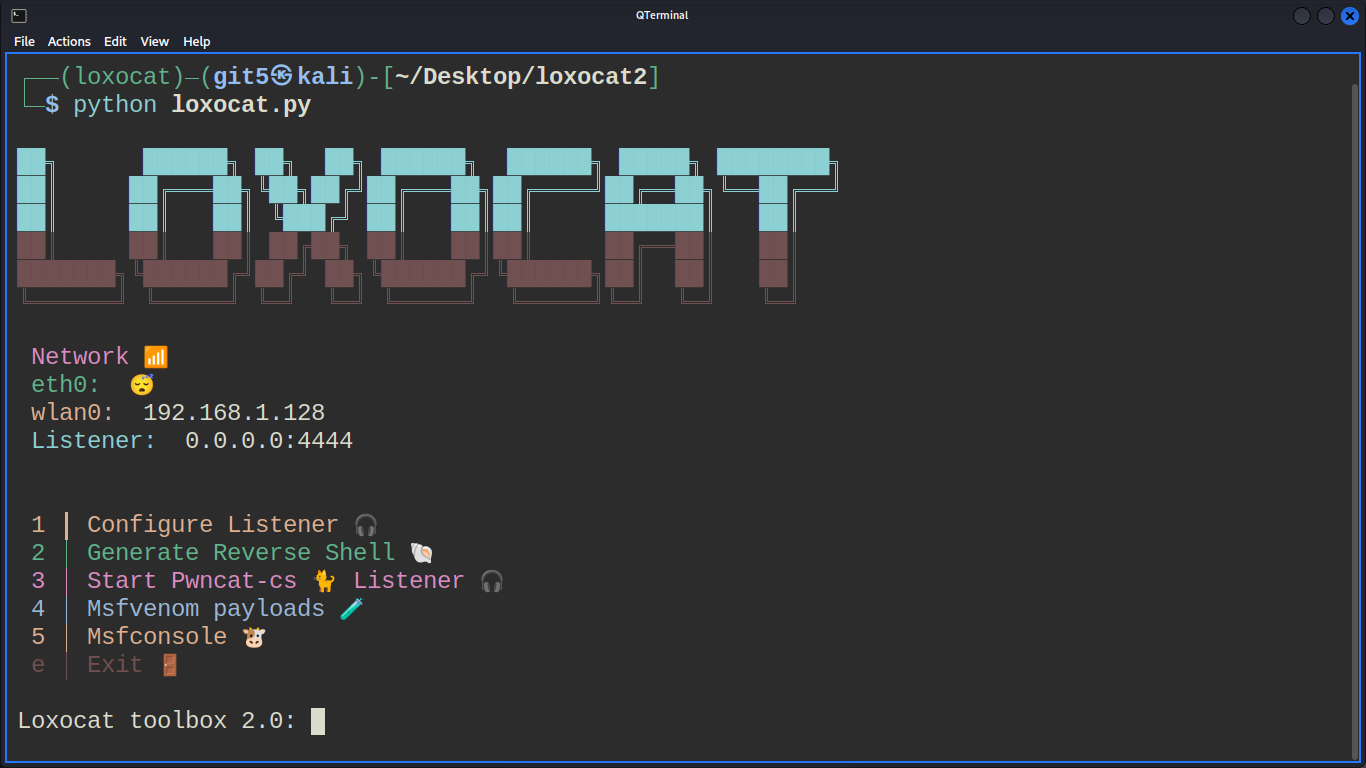
🐘 Loxocat 2.1 Toolbox - Your Ultimate Hacking Companion! 🐈
Introduction: Loxocat 2.1 is a cutting-edge hacking toolbox that empowers hackers with a diverse array of powerful tools and features. It's designed to facilitate undetectable netcat (ncat) oriented payloads, offering seamless integration with msfvenom payloads, and utilizes pwncat-cs as a listener handler for automatic privilege escalation upon establishing connections.
Key Features: 🛠️ Undetectable Ncat Payloads: Loxocat 2.1 excels in generating undetectable netcat (ncat) payloads, ensuring your activities remain stealthy and under the radar during penetration testing and security assessments.
🚀 Seamless Msfvenom Integration: Harness the power of msfvenom payloads within Loxocat 2.1, granting you the ability to conduct sophisticated exploits and gain remote access with ease.
🔐 Automatic Privilege Escalation: Loxocat 2.1 seamlessly integrates with pwncat-cs, empowering you to automatically escalate privileges once a successful connection is established, streamlining post-exploitation procedures.
💻 User-Friendly Interface: Loxocat 2.1 boasts an intuitive and user-friendly interface that streamlines your workflow, allowing you to focus on critical tasks without unnecessary complexities.
📚 Comprehensive Documentation: Empowering users with knowledge is vital. Loxocat 2.1 provides detailed documentation, ensuring you have all the necessary guidance to maximize the potential of each tool and feature.
Manual Installation Process:
Step 1 - Clone the Repository: Begin by cloning the Loxocat 2.1 repository from GitHub:
git clone https://github.com/git5loxosec/loxocat2.git
Step 2 - Set Up the Virtual Environment: Move into the Loxocat 2 directory and create a virtual environment named "loxocat":
cd loxocat2
python3 -m venv loxocat
Step 3 - Activate the Virtual Environment: Activate the virtual environment using:
source loxocat/bin/activate
Step 4 - Install Dependencies: While within the virtual environment, install the required project dependencies listed in "requirements.txt":
pip install -r requirements.txt
setp 5 - Run Loxocat 2:
python loxocat.py
OR
git clone https://github.com/git5loxosec/loxocat2.git
cd loxocat2
python3 -m venv loxocat
source loxocat/bin/activate
pip install -r requirements.txt
python loxocat.py
Generate Payloads:** With Loxocat 2.1 now set up, take advantage of its undetectable netcat payload generation and msfvenom integration to craft powerful payloads tailored to your objectives.
Utilize pwncat-cs for Privilege Escalation:** Upon establishing connections with your payloads, let pwncat-cs handle automatic privilege escalation for a seamless post-exploitation experience.
Securely Manage Connections:** Harness Loxocat 2.1 capabilities to securely manage and maintain connections, ensuring your operations are efficient and effective.
Caution: Ethical and responsible use of Loxocat 2.1 is paramount. Always adhere to applicable laws and regulations. Unleash your hacking prowess responsibly and elevate your cybersecurity skills with Loxocat 2! 🚀💻🔐
- git5