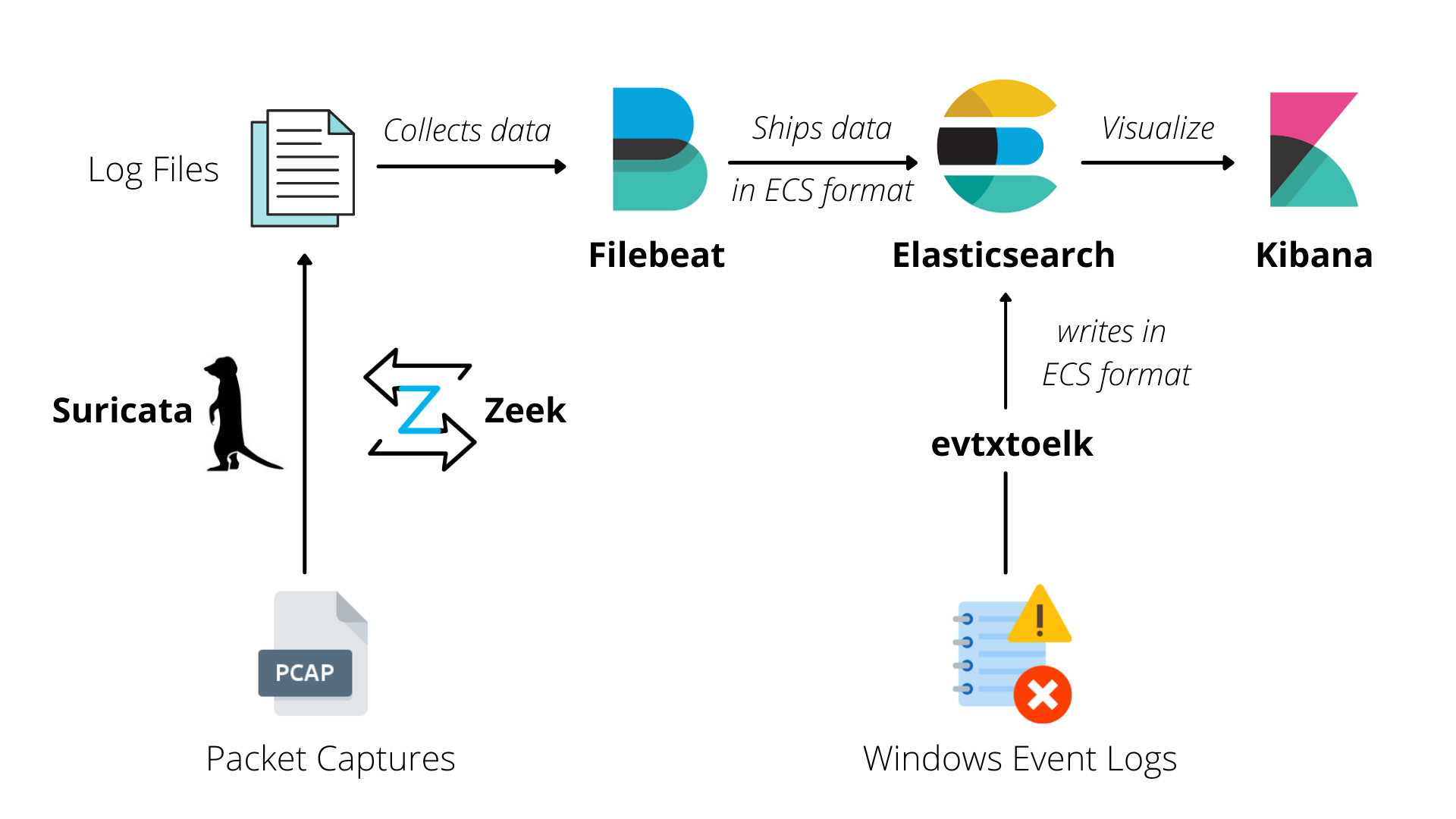
Pcapmonkey is a project that will provide an easy way to analyze pcap using the latest version of Suricata and Zeek. It can also save Suricata and Zeek logs in Elasticsearch using the new Elasticsearch Common Schema or the original field names.
Pcapmonkey uses the default docker container for most images and aims to be easy and straightforward to use.
Video tutorial: Startup, Pcap Analysis
Since its birth, this project has been participating in the GSoC under the Honeynet Project!
- 2021: Projects available
Stay tuned for the upcoming GSoC! Join the Honeynet Slack chat for more info.
Install Docker-CE:
Then just clone this repo to your local machine, run ./prepare.sh and you're ready to go. All the commands listed in this tutorial should be launched from whithin the root folder of this project.
To uninstall and remove all files, delete all containers with
sudo docker compose down -v
Then you can safely delete this repository.
To analyze a Packet Capture file, put it to the ./pcap/ and run:
sudo docker compose up -d elasticsearch filebeat kibanaThen download the Open-ET Rules for suricata.
sudo docker compose run --entrypoint='suricata-update -f' suricataFinally, start the Suricata and Zeek containers to analyze the pcap.
sudo docker compose up suricata zeekPut the .evtx file to be analyzed to import_event_logs/ and start evtxtoelk.
sudo docker compose up evtxtoelkCheck this wiki for detailed instructions.
PcapMonkey now supports live traffic analysis! Check wiki for instructions.
If you prefer using the command line, you can find suricata and zeek logs in the ./logs directory.
If you don't want to waste time starting filebeat/elasticsearch/kibana go to ./zeek/site/local.zeek and comment out the first line (@load policy/tuning/json-logs.zeek). Then start analyzing a new pcap and enjoy plaintext, tab-separated zeek logs. awk all the way, baby!
Even if you'd like to use directly the log file I suggest keeping them in .json format and use jq utility to query them. You can read a pretty good jq primer here
For more information, check PcapMonkey wiki: https://github.com/certego/PcapMonkey/wiki