This example shows how a Spring Security application can connect to Casdoor via OAuth 2.0.
We assume you have deployed Casdoor in your own URL (refer to: Server Installation), in this example, we use the Casdoor demo site: https//door.casdoor.com
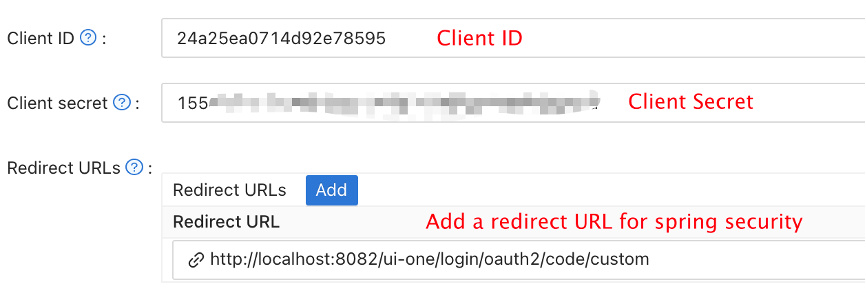
In the application edit page of your Casdoor (like: https://door.casdoor.com/applications/casbin/app-vue-python-example), you can get the Client ID and Client secret of the application. Remember to add your application's URL: http://localhost:8080/ to Casdoor's "Redirect URLs":
Open in a browser: https://door.casdoor.com/.well-known/openid-configuration, you will get the OIDC endpoints of Casdoor.
{
"issuer": "https://door.casdoor.com",
"authorization_endpoint": "https://door.casdoor.com/login/oauth/authorize",
"token_endpoint": "https://door.casdoor.com/api/login/oauth/access_token",
"userinfo_endpoint": "https://door.casdoor.com/api/userinfo",
"jwks_uri": "https://door.casdoor.com/.well-known/jwks",
"introspection_endpoint": "https://door.casdoor.com/api/login/oauth/introspect",
"response_types_supported": [
"code",
"token",
"id_token",
"code token",
"code id_token",
"token id_token",
"code token id_token",
"none"
],
"response_modes_supported": [
"query",
"fragment",
"login",
"code",
"link"
],
"grant_types_supported": [
"password",
"authorization_code"
],
"subject_types_supported": [
"public"
],
"id_token_signing_alg_values_supported": [
"RS256"
],
"scopes_supported": [
"openid",
"email",
"profile",
"address",
"phone",
"offline_access"
],
"claims_supported": [
"iss",
...
],
"request_parameter_supported": true,
"request_object_signing_alg_values_supported": [
"HS256",
"HS384",
"HS512"
],
"end_session_endpoint": "https://door.casdoor.com/api/logout"
}Replace the settings in this application's YAML file: application.yml with your own Casdoor's settings.
spring:
security:
oauth2:
client:
registration:
casdoor:
client-id: 294b09fbc17f95daf2fe
client-secret: dd8982f7046ccba1bbd7851d5c1ece4e52bf039d
scope: read,write
authorization-grant-type: authorization_code
redirect-uri: http://localhost:8080/login/oauth2/code/custom
provider:
casdoor:
authorization-uri: https://door.casdoor.com/login/oauth/authorize
token-uri: https://door.casdoor.com/api/login/oauth/access_token
user-info-uri: https://door.casdoor.com/api/get-account
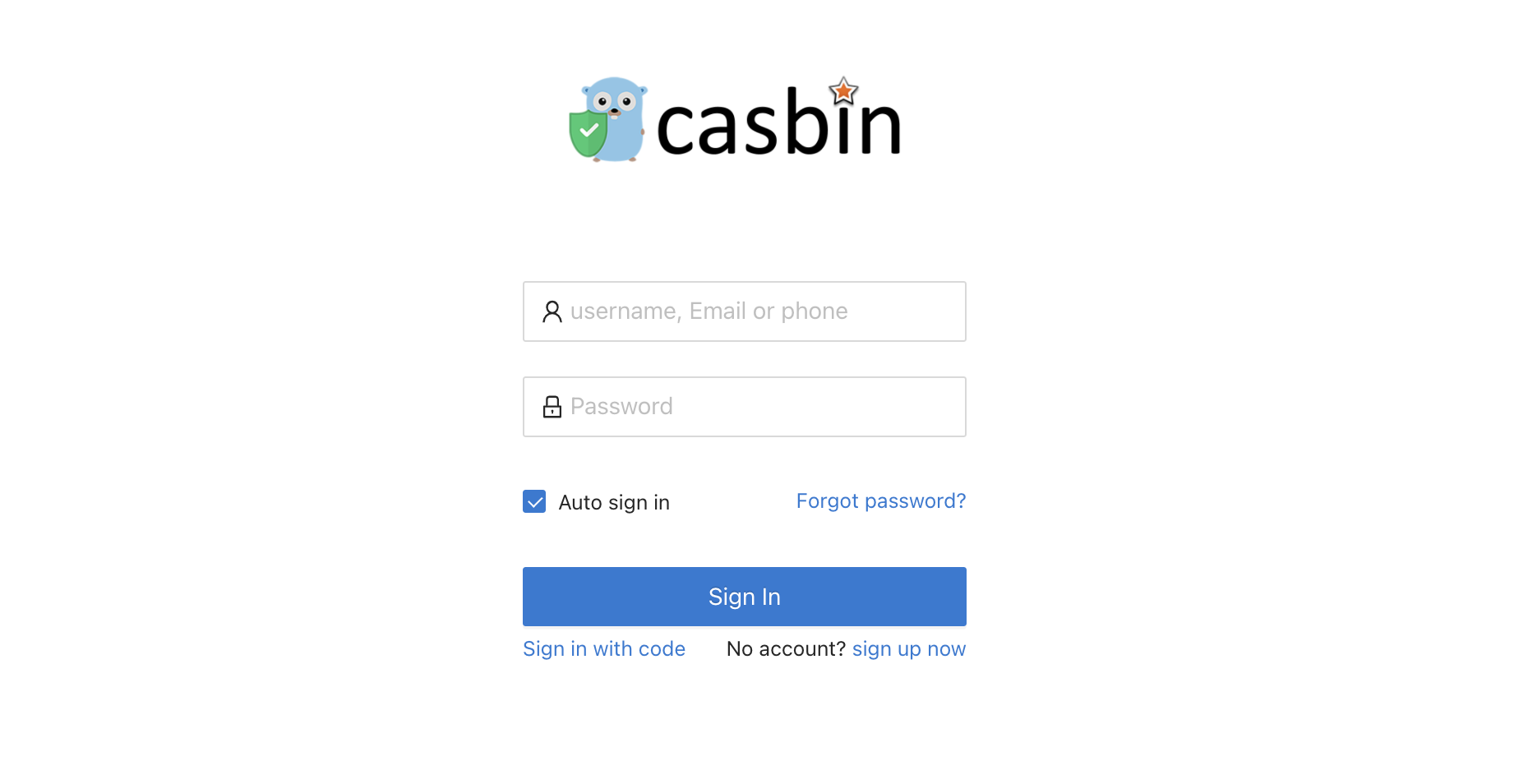
user-name-attribute: nameIn the browser, visit: http://localhost:8080/foos. It will automatically redirect to Casdoor's login page. Login with username: admin and password: 123.
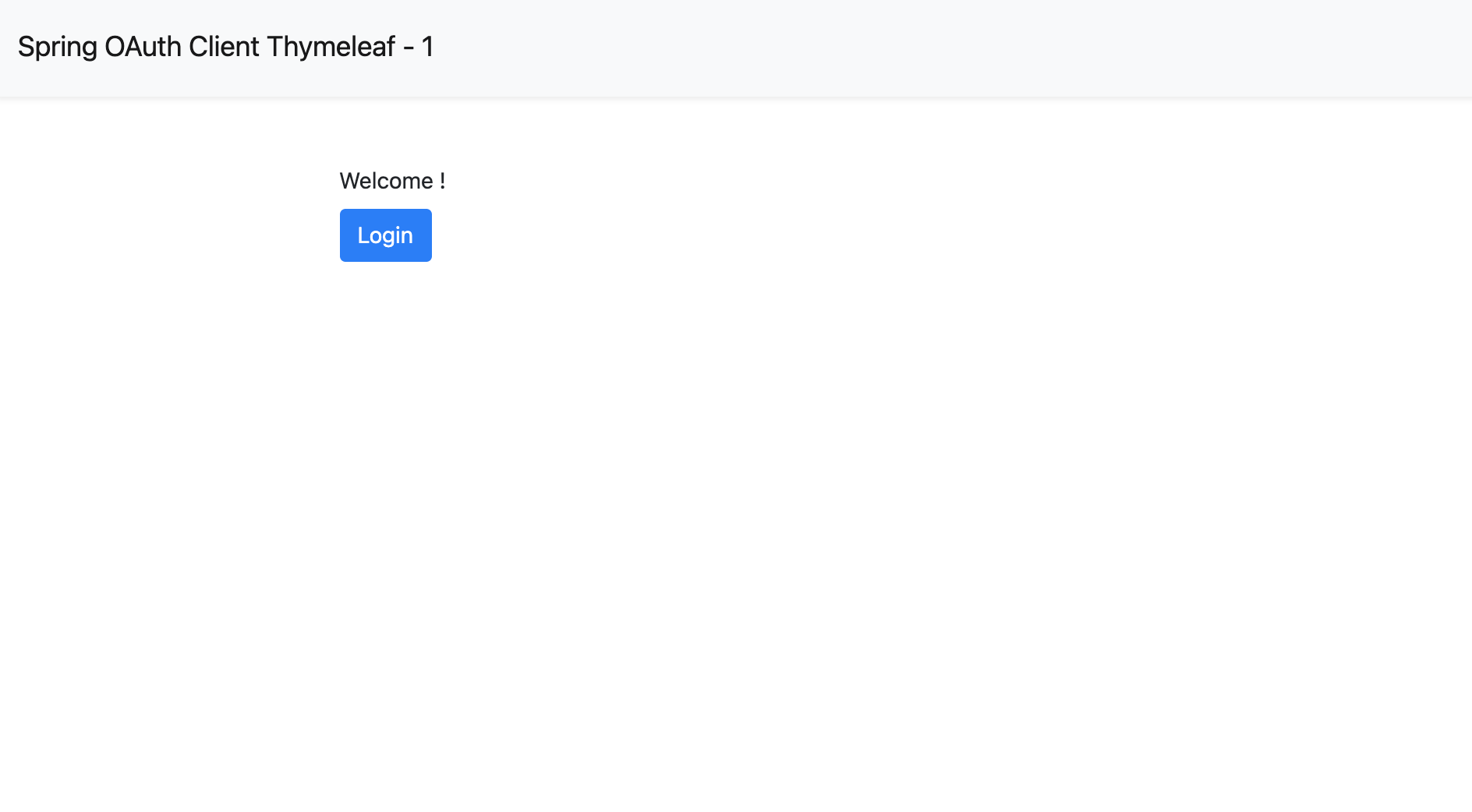
If you visit your root page: http://localhost:8080, you will see:
Click the Login button to redirect to Casdoor's login page.
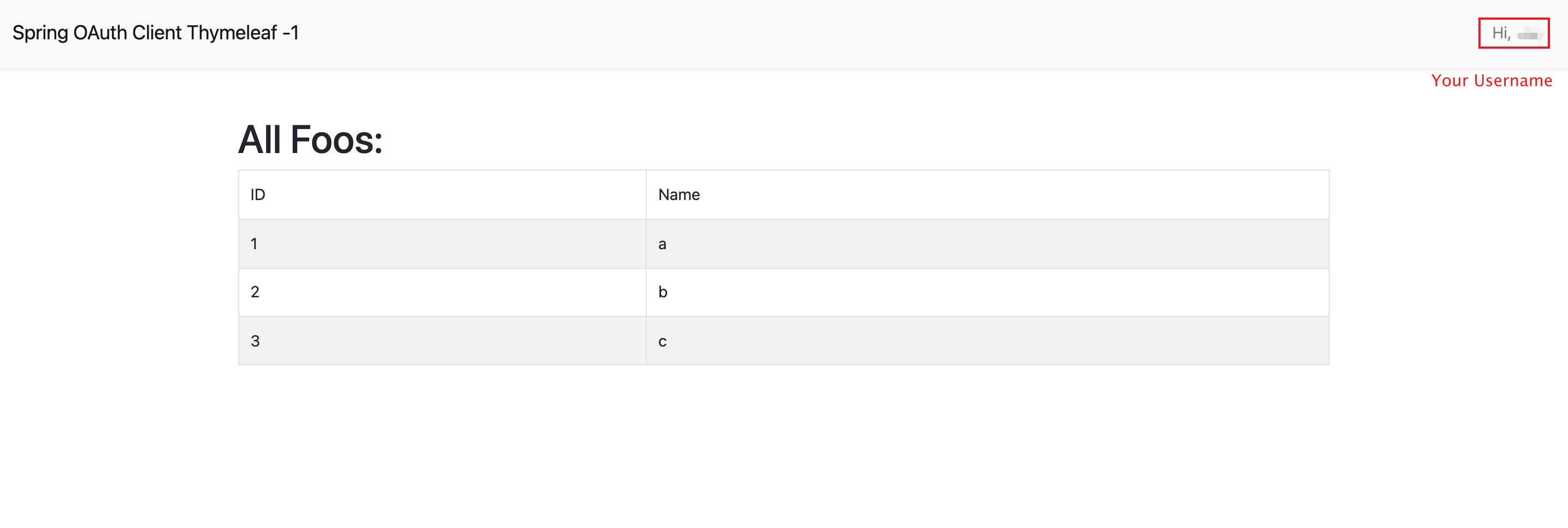
After you logged in, the page will redirect to /foos.
-
Create a Spring Boot application in
SSOClientApplication. -
Add a configuration which protects all endpoints except
/and/login**for users to loginUiSecurityConfiguration. -
Add a naive page for user to login in
resources/templates/index.html. When user clicks theloginbutton, he will be redirected tocasdoor. -
Define our protected resource. We can export an endpoint called
/foosand a web page for display.