pip install confidential
Confidential manages secrets for your project, using AWS Secrets Manager and SSM Parameter Store.
First, store a secret in AWS Secrets Manager. Then, create a secrets file, say my_secrets.json. A value will be decrypted if the word secret precedes it, like the database value below:
{
"database": "secret:database_details",
"environment": "production",
"debug_mode": false
}Similarly, SSM Parameters can be referenced by providing a parameter key, e.g.: "ssm:some_ssm_parameter_key".
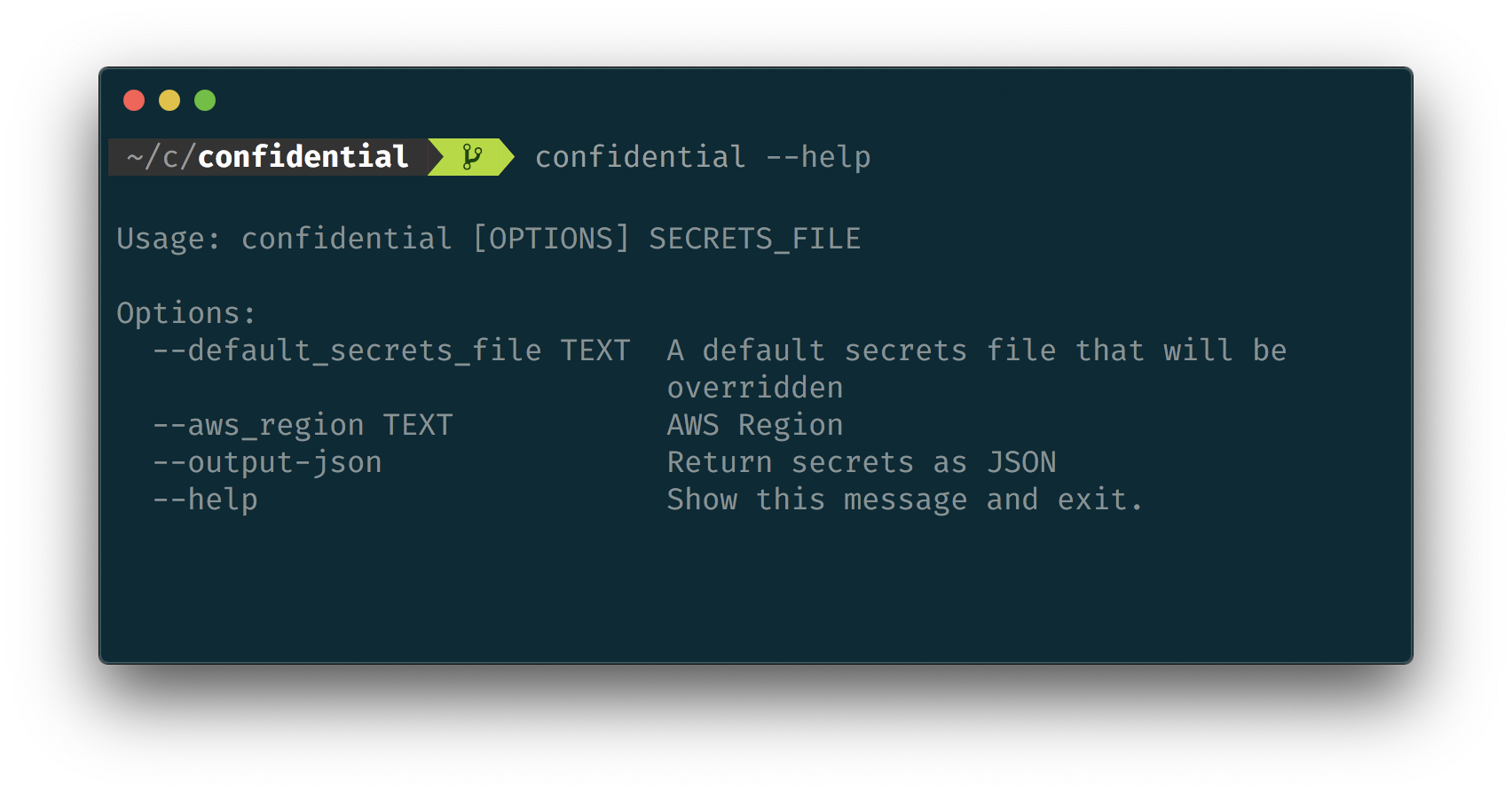
You can decrypt this file either in Python, or directly using the CLI. Ensure AWS CLI is set up, then run:
confidential my_secrets.jsonwhich outputs the file with decrypted values
{
"database": {
"url": "https://example.com",
"username": "admin",
"password": "p@55w0rd",
"port": 5678
},
"environment": "production",
"debug_mode": false
}Yes, simply import and instantiate SecretsManager, like so:
settings.py
from confidential import SecretsManager
secrets = SecretManager(
secrets_file=".secrets/production.json",
secrets_file_default=".secrets/defaults.json", # Overridable defaults you can use in common environments
region_name="us-east-1",
)
DATABASES = {
'default': secrets["database"]
}If export_env_variables is set to True, each secret will also be exported as an environment variable, with the uppercase key as the variable name, e.g.:
from confidential import SecretsManager
import os
secrets = SecretManager(
secrets_file=".secrets/production.json",
secrets_file_default=".secrets/defaults.json", # Overridable defaults you can use in common environments
region_name="us-east-1",
export_env_variables=True, # Optionally, export secrets as environment variables. Default is False.
)
# If the key of a secret is `api_key`, then the following is true:
assert secrets["api_key"] == os.environ.get("API_KEY")Trying to access an inexisting key returns None. On previous versions, it would throw an exception.
First, install all dependencies:
poetry installThen run the tests
poetry run pytest