What medor's master can say about him:
medor is a good dog. Provided you send him far enough, he can come back with a juicy bone 🦴
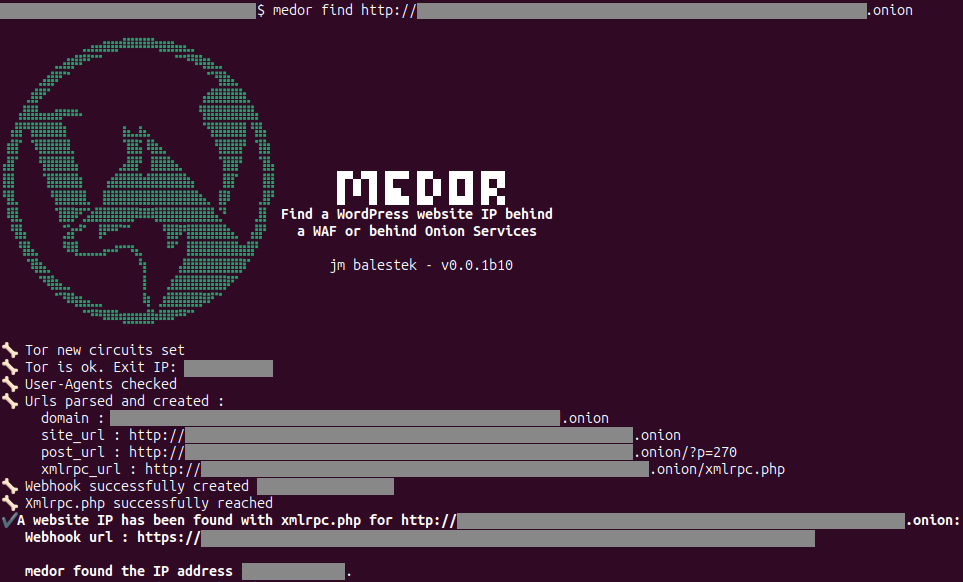
Medor is an OSINT (Open Source Intelligence) tool that enables you to discover the IP address of a WordPress site, even if it's obscured by a WAF (Web Application Firewall) or located within the darknet (onion services). It requests xmlrpc.php to get the IP behind the WAF thanks to a webhook provider.
It requires several kibbles to work:
- a WordPress website with an unsecured xmlrpc.php
- a post from the WordPress website (not a page!)
medor comes with few features:
- it works with the domain, the website url or a wp post
- it can find a blog post with WordPress REST API or the feed
- it updates and rotates user-agents per request
- a proxy can be used
- tor support for .onion
- option to customize the xmlrpc response webhook URL
- todo : an optional flask server to handle the xmlrpc.php response
- todo : use list of proxies with random selection per request
- todo : check an imported list of domains, hosts or url
Python 3.8+ is required.
pipx install medorpipenv install medorpip install medorThe command to find the IP address associated with a particular item is find, followed by the item you want to investigate (such as a domain, a website URL, or a post URL)
medor find website.com
# or
medor find https://www.website.com
# or
medor find https://www.website.com/a-blog-post/Proxy format should be protocol://user.password@IP:port if you use authentication or
protocol://IP:port if not. The optional argument is --proxy=yourproxy or -p yourproxy.
Proxy doesn't work with .onion services as tor is used instead.
Allowed protocols :
- http
- https
- socks5(h). For socks5h:// use socks5:// (httpx[socks] uses socks5h by default)
medor find website.com -p http://user.password@255.255.255.255:8080
# or
medor find https://www.website.com --proxy socks5://user.password@255.255.255.255:6154By default, medor uses a new webhook from webhook.site (see credits) but you can use another service or your own with the option --webhook= or -w followed by the webhook URL.
medor find https://www.website.com -w https://website.com/webhook/kjqh4sfkq4sj5h5f
# or
medor find website.com --webhook https://website.com/webhook/kjqh4sfkq4sj5h5fmedor works as well with onion websites. For that, you need tor. There are 2 ways:
- Tor Browser running and connected to tor. medor will use it to connect to onion services.
- Installing tor on your system. To install tor, see below.
medor find rtfjdnrppk7yj0424wa5i1hc6chq4nj6p3w7tu2q5qh47fmf6pi3.onion
# or
medor find http://rtfjdnrppk7yj0424wa5i1hc3chq4nj6p3w7tu2q5qh47fmf6pi3.onion- Download Tor
Download the Tor Expert Bundle for your Windows architecture from the following link: https://www.torproject.org/download/tor/.
- Extract the archive
Extract the tor.exe from the archive to a convenient location on your computer, such as C:\tor\.
- Enter the full path of the tor.exe
When prompted during the first search for a .onion website, enter the full path of the tor.exe executable. For example, C:\tor\tor.exe.
You can also set or change the path later by using the command medor tor_path.
- Setup tor repo and install Tor
To obtain the latest version of Tor, you need to set the Tor package repository. This is important for security reasons.
Instructions for installing Tor can be found here: https://community.torproject.org/onion-services/setup/install/
After installing tor, you can test it by opening a terminal and running the command tor. This should start the tor process and print some log messages to the terminal. Once you have verified that Tor is working correctly, you can close the terminal or stop the tor process by pressing Ctrl+C in the terminal.
- Enter the tor command when prompted
When prompted during the first search for a .onion website, enter tor.
You can also set or change the command or path later by using the command medor tor_path.
- If tor is already running on your system, medor may not be able to launch a new instance of tor.
To resolve this issue, you need to kill the tor process. When installing tor on Ubuntu, it will start tor at every boot. You need to kill tor process before using medor or disable tor from starting at boot (
sudo systemctl disable tor.service). - If you get a "Timeout" error, especially with onion services, it may be a temporary issue with the Tor network. Try again.
Strongly inspired by Dan Nemec's post.
httpx and httpx[socks]
brotlipy
stem
halo
colorama
docopt
lxml
beautifulsoup4
validators
python-dotenv
medor utilizes the excellent webhook service provided by Simon Fredsted's webhook.site. If you require a webhook service with a multitude of features, consider using it.
GPLv3