The essence of our work as security professionals is our understanding of two key terms: security and risk.
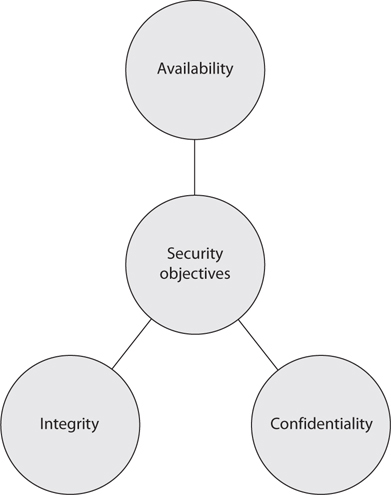
The core goals of security, are to provide availability, integrity, and confidentiality (often referred as CIA triad) protection for critical assets. All risks, threats, and vulnerabilities are measured for their potential capability to compromise one or all of the CIA principles.
Availability protection ensures reliability and timely access to data and resources to authorized individuals. Necessary protection mechanisms must be in place to protect against inside and outside threats that could affect the availability and productivity of all business-processing components.
- Redundant array of independent disks (RAID)
- Clustering
- Load balancing
- Redundant data and power lines
- Software and data backups
- Disk shadowing
- Co-location and offsite facilities
- Rollback functions
- Failover configurations
Integrity is upheld when the assurance of the accuracy and reliability of information and systems is provided and any unauthorized modification is prevented.
- Hashing (data integrity)
- Configuration management (system integrity)
- Change control (process integrity)
- Access control (physical and technical)
- Software digital signing
- Transmission cyclic redundancy check (CRC) functions
Confidentiality ensures that the necessary level of secrecy is enforced at each junction of data processing and prevents unauthorized disclosure. This level of secrecy should prevail while data resides on systems and devices within the network, as it is transmitted, and once it reaches its destination.
- Encryption for data at rest (whole disk, database encryption)
- Encryption for data in transit (IPSec, TLS, PPTP, SSH)
- Access control (physical and technical)
Vulnerability is a weakness in a system that allows a threat source to compromise its security.
Threat is any potential danger that is associated with the exploitation of a vulnerability. The entity that takes advantage of a vulnerability is referred to as a threat agent.
Risk is the likelihood of a threat source exploiting a vulnerability and the corresponding business impact. Risk ties the vulnerability, threat, and the likelihood of exploitation to the resulting business impact.
Exposure is an instance of being exposed to losses. A vulnerability exposes an organization to possible damages.
Control or countermeasure, is put into place to mitigate the potential risk.
Applying the right countermeasure can eliminate the vulnerability and exposure, and thus reduce the risk. The company cannot eliminate the threat agent, but it can protect itself and prevent this threat agent from exploiting vulnerabilities within the environment.
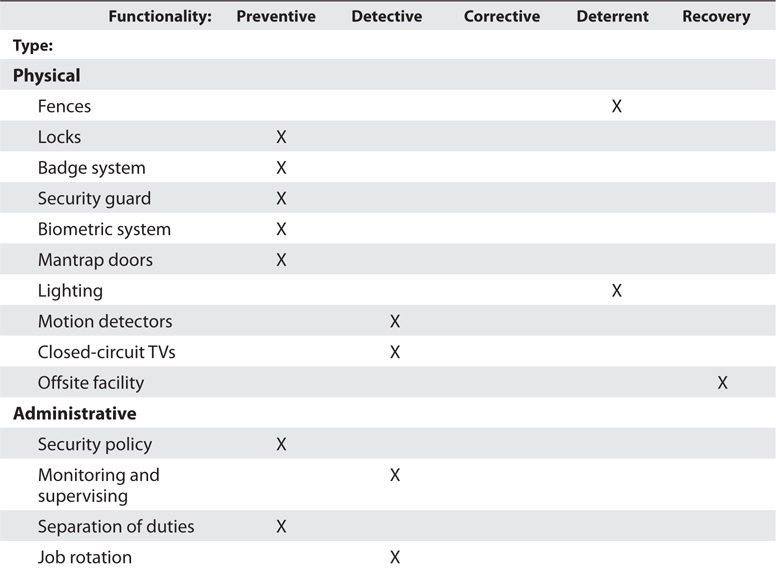
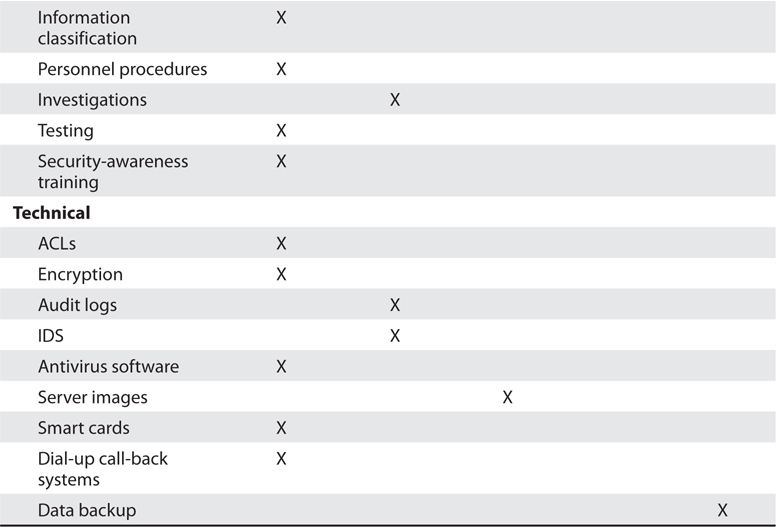
Controls are put into place to reduce the risk an organization faces, and they come in three main flavors: administrative, technical, and physical. Administrative controls are commonly referred to as "soft controls" because they are more management oriented (security documentation, risk management, training). Technical controls (also called logical controls) are software or hardware components (firewalls, IDS, encryption, identification and authentication mechanisms). And physical controls are items put into place to protect facility, personnel, and resources (security guards, locks, fencing)
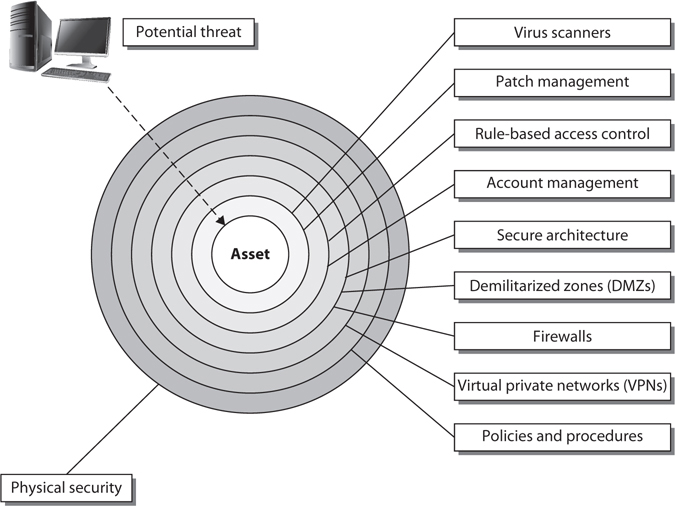
These controls need to be put into place to provide defense-in-depth, which is the coordinated use of multiple security controls in a layered approach.
The types of controls that are actually implemented must map to the threats the company faces, and the number of layers that are put into place must map to the sensitivity of the asset. The rule of thumb is the more sensitive the asset, the more layers of protection that must be put into place.
The different functionalities of security controls are:
- Preventive: intended to avoid an incident from occurring
- Detective: Helps identify an incident's activities and potentially an intruder
- Corrective: Fixes components or systems after an incident has occurred
- Deterrent: Intended to discourage a potential attacker
- Recovery: Intended to bring the environment back to regular operations
- Compensating: Controls that provide an alternative measure of control that provides similar protection as the original control, but has to be used because it is more affordable or allows specifically required business functionality.
It is not feasible to prevent everything; therefore, what you cannot prevent, you should be able to quickly detect. That's why preventive and detective controls should always be implemented together and should complement each other.
When trying to map the functionality requirement to a control, think of the main reason that control would be put into place.
Controls should work in harmony to provide healthy, safe, and productive environments.
A security program is a framework made up of many entities: logical, administrative, and physical protection mechanisms; procedures; business processes; and people that all work together to provide a protection level for an environment. Each has an important place in the framework, and if one is missing or incomplete, the whole framework may be affected. The program should work in layers: each layer provides support for the layer above it and protection for the layer below it.
What NOT TO DO: Security through Obscurity
- ISO/IEC 27000 series: International standards on how to develop and maintain an ISMS (Information Security Management System; aka Security Program) developed by ISO and IEC. Serves as industry best practices for the management of security controls in a holistic manner within organizations around the world. The list of standards that makes up this series grows each year. Each standard has a specific focus (such as metrics, governance, auditing, and so on).
An architecture is a conceptual construct. It is a tool to help individuals understand a complex item (such as an enterprise) in digestible chunks. An enterprise architecture encompasses the essential and unifying components of an organization. It expresses the enterprise structure (form) and behaviour (function). It embodies the enterprise's components, their relationships to each other, and their relationships to the environment.
You use the framework as a guideline on how to build an architecture that best fits your company's needs.
An enterprise architecture allows you to not only understand the company from several different views, but also understand how a change that takes place at one level will affect items at other levels. It is used to optimize often fragmented processes (both manual and automated) into an integrated environment that is responsive to change and supportive of the business strategy.
When attempting to figure out which architecture framework is best for your organization, you need to find out who the stakeholders are and what information they need from the architecture. One main difference between the various enterprise architecture frameworks is what type of information they provide and how they provide it.
- Zachman Framework: Model for the development of enterprise architectures developed by John Zachman. It is a two-dimensional model that uses six basic communication interrogatives (What, How, Where, Who, When, and Why) intersecting with different perspectives (Executives, Business Managers, System Architects, Engineers, Technicians, and Enterprise-wide) to give a holistic understanding of the enterprise. The goal of this framework is to be able to look at the same organization from different viewpoints. Different groups within a company need the same information, but presented in ways that directly relate to their responsibilities. This framework is not security oriented, but it is a good template to work with because it offers direction on how to understand an actual enterprise in a modular fashion.
- TOGAF: Model and methodology for the development of enterprise architectures developed by The Open Group. It is a framework that can be used to develop the following architecture types: business architecture, data architecture, application architecture, and technology architecture. It can be used to create these individual architecture types through the use of its Architecture Development Method (ADM). This method is an iterative and cyclic process that allows requirements to be continuously reviewed and the individual architectures updated as needed.
- DoDAF: US Department of Defense architecture framework that ensures interoperability of systems to meet military mission goals. The focus of the architecture framework is on command, control, communications, computers, intelligence, surveillance, and reconnaissance systems and processes.
- MODAF: Architecture framework used mainly in military support missions developed by the British Ministry of Defence based upon de DoDAF. The crux of the framework is to be able to get data in the right format to the right people as soon as possible.
An enterprise security architecture is a subset of an enterprise architecture and defines the information security strategy that consists of layers of solutions, processes, and procedures and the way they are linked across an enterprise strategically, tactically, and operationally.
- SABSA model: Model and methodology for the development of information security enterprise architectures
- COBIT 5: A business framework to allow for IT enterprise management and governance that was developed by ISACA
- NIST SP 800-53: Set of controls to protect US federal systems developed by the National Institute of Standards and Technology
- COSO Internal Control-Integrated Framework: Set of internal corporate controls to help reduce the risk of financial fraud developed by the Committee of Sponsoring Organizations (COSO) of the Treadway Commission
- ITIL: Processess to allow for IT service management developed by the United Kingdom's Office of Government Commerce
- Six Sigma: Business management strategy that can be used to carry out process improvement
- Capability Maturity Model Integration (CMMI) : Organizational development for process improvement developed by Carnegie Mellon University