Se trata de una vulnerabilidad de diseño, que se fundamenta en un error del controlador de la pila TCP/IP de Windows, tcpip.sys, que es un controlador de kernel. Entre otras cosas, esta pila analiza paquetes ICMPv6 de Router Advisement que utilizan la opción de servidor DNS recursivo. Cuando se recibe uno de estos paquetes con una longitud par, los últimos 8 bytes del paquete de DNS recursivo se interpretan erróneamente, concretamente como los 8 primeros bytes de una segunda opción, pudiendo así realizar un desbordamiento de búfer o buffer overflow (BO).
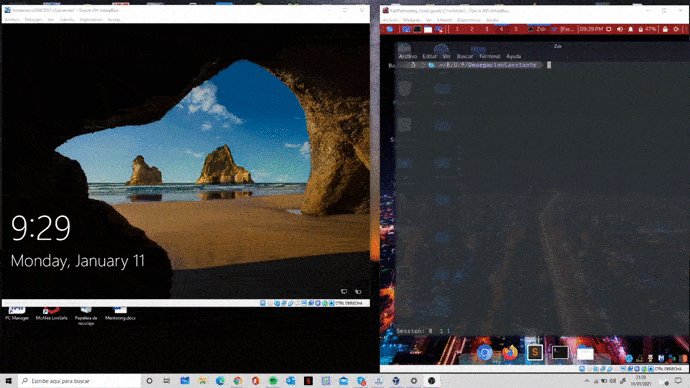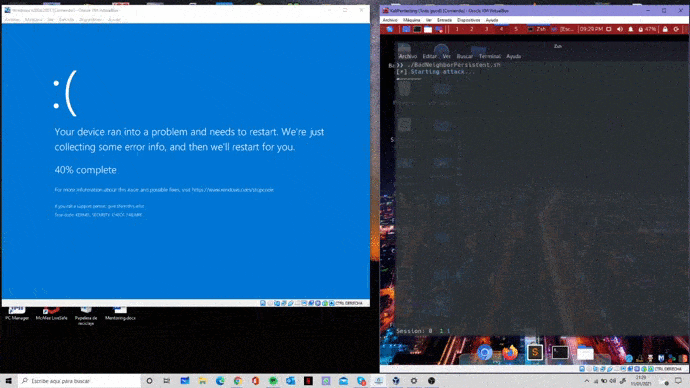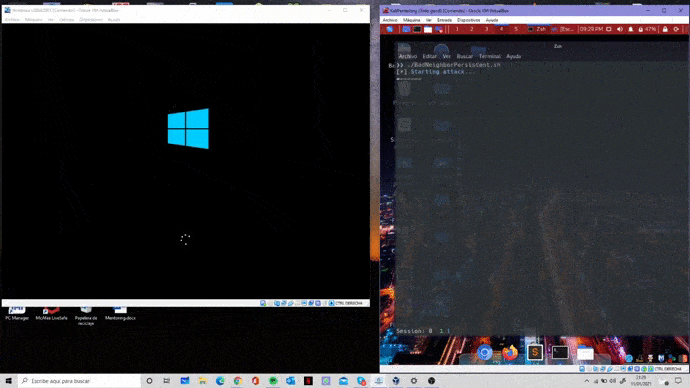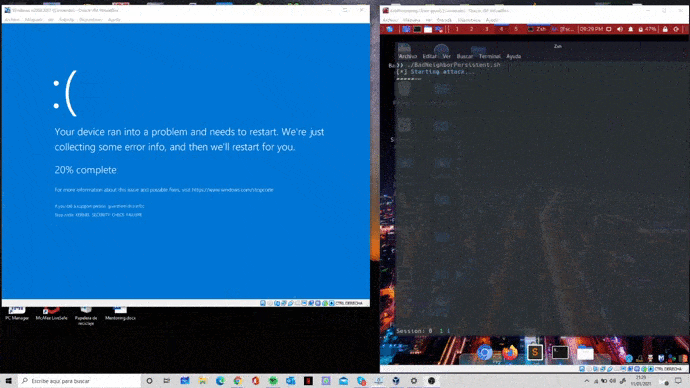
Esto puede utilizarse tanto para ataques de DoS o denegación de servicio (que será nuestro caso, pues provocaremos un BSOD, afectando así a la disponibilidad), como para ataques de ejecución remota de código (RCE). Además, se cree que esta vulnerabilidad podría convertirse en wormable, de ahí su criticidad.
Máquina virtual Necesitamos montar el laboratorio (Windows 10 v2004): https://bit.ly/3nTxWNP
Herramientas necesarias
- Herramientas para el escaneo de la red: nmap, netscan, fing, etc. También podemos hacer uso de scripts de reconocimiento de dispositivos en la red local, como los que adjuntamos o los que ofrece nmap, por ejemplo.
- Consola de comandos e intérprete de python3 para ejecutar nuestro exploit.
- Se hace uso de la librería Scapy de python, que permite crear, modificar y enviar diferentes paquetes de red (IPv6, ICMPv6…)
- Herramientas para analizar el tráfico de red, como Wireshark, para poder ver e interpretar el tráfico de paquetes por la red (no es necesario para su explotación).
- Herramientas que nos permitan realizar ingeniería inversa sobre tcpip.sys para poder entender el funcionamiento de la pila (no es necesario para su explotación).
Para escanear la IPv6:
sudo arp-scan --interface=eth0 –localnet
./ipv4a6.sh direccion_IPv4
Para ver nuestra propia IP:
-
Si es Windows:
ipconfig -
Si es Linux:
sudo ifconfig
Ejecutamos el exploit:
sudo python3 poc.py