The Simple Telnet Honeypot Server offers cybersecurity professionals and enthusiasts a straightforward tool for capturing and analyzing Telnet-based interactions. This Python-scripted server, built upon the Twisted network programming framework, simulates a Telnet server to log unauthorized access attempts and helps in identifying potential security breaches.
- Low-Interaction Honeypot: Simulates a Telnet server to safely log authentication attempts without high risk.
- Configurable Settings: The host and port settings can be easily modified using command-line arguments.
- Extensive Logging: Every interaction, including login credentials, is recorded for in-depth security auditing.
- Interactive Response Simulation: Mimics a live Telnet service, providing automated responses to capture more detailed information.
- Educational Resource: Great for learning about Telnet service vulnerabilities and network security monitoring.
- Python 3.x
- Twisted Python library
Begin by cloning the repository or downloading the telnet.py script. Make sure Python and Twisted are installed on your system.
git clone https://github.com/0xNslabs/telnet-honeypot.git
cd telnet-honeypot
pip install twistedStart the server with the following command, specifying host and port if needed. By default, it binds to all interfaces (0.0.0.0) on port 2323.
python3 telnet.py --host 0.0.0.0 --port 2323Interaction logs are saved in telnet_honeypot.log, which contains detailed records of all Telnet commands and login attempts.
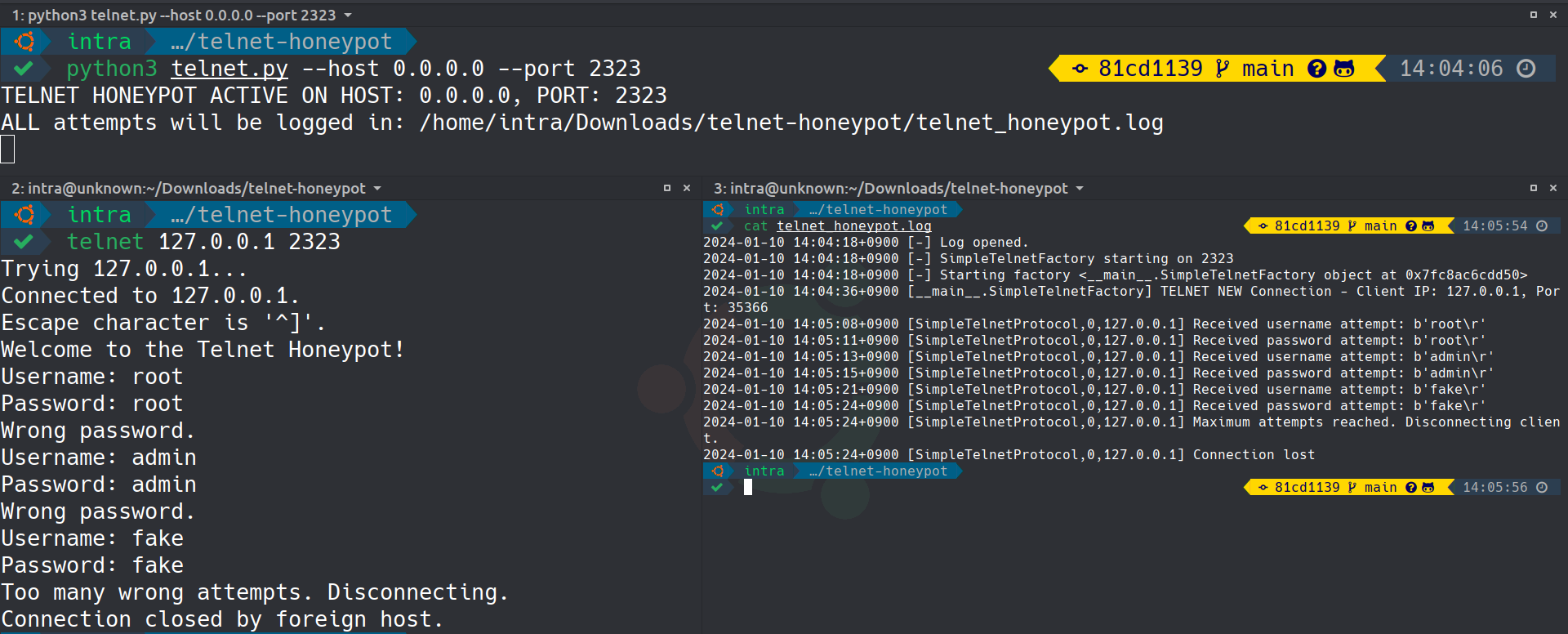 The above image showcases the Simple Telnet Honeypot server capturing login attempts.
The above image showcases the Simple Telnet Honeypot server capturing login attempts.
Check out the other honeypot services for monitoring various network protocols:
- DNS Honeypot - Monitors DNS interactions.
- FTP Honeypot - Simulates an FTP server.
- LDAP Honeypot - Mimics an LDAP server.
- HTTP Honeypot - Monitors HTTP interactions.
- HTTPS Honeypot - Monitors HTTPS interactions.
- NTP Honeypot - Monitors Network Time Protocol interactions.
- PostgreSQL Honeypot - Simulates a PostgreSQL database server.
- SIP Honeypot - Monitors SIP (Session Initiation Protocol) interactions.
- SSH Honeypot - Emulates an SSH server.
- TELNET Honeypot - Simulates a TELNET server.
- Caution: Operate this honeypot within a secure and controlled environment.
- Compliance: Deploy this honeypot in accordance with applicable laws and regulations.
This project is made available under the MIT License. For more information, see the LICENSE file.