Cleanup CloudFormation stacks respecting the order of dependencies.
-
Stack name pattern matching for deletion. Finds out dependent/importer/child stacks recursively from a root stack.
-
Builds dependency tree for faster teardown. Dependency tree also gives insight on loose/tight coupling of the stacks.
-
Multiple safety checks to prevent accidental deletion.
-
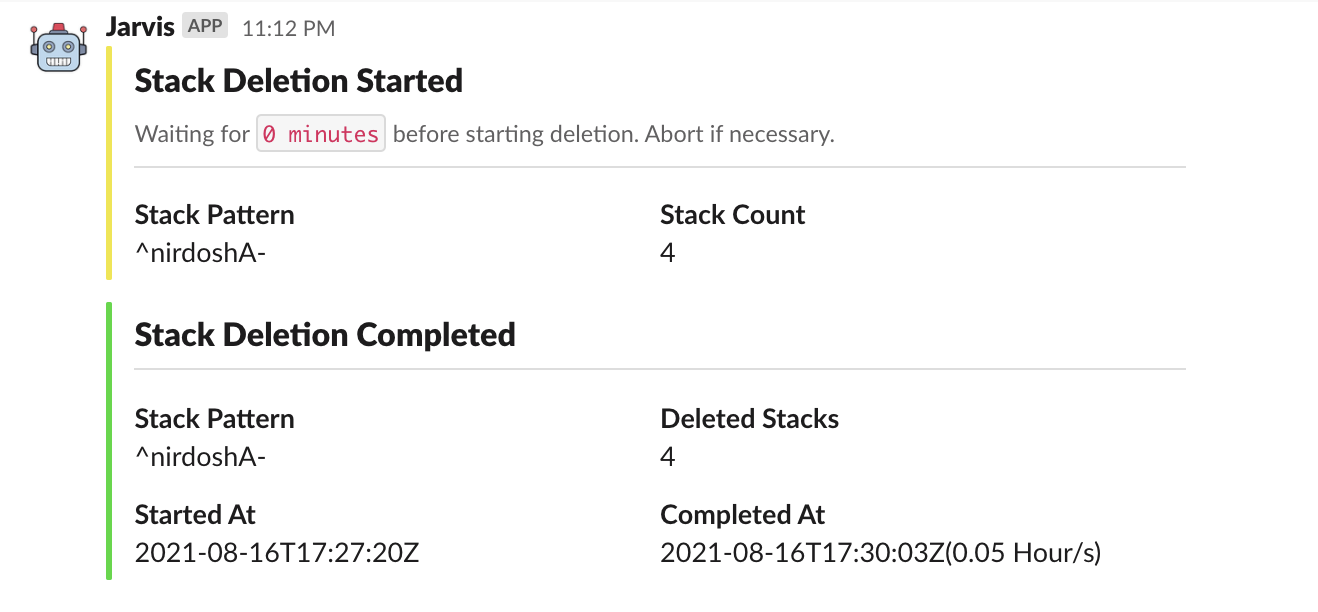
Supports slack notification for deletion status updates via webhook.
Run downloader script:
curl -f https://raw.githubusercontent.com/nirdosh17/cfn-teardown/master/download.sh | shOR
Download binary manually from HERE.
Required global flags for all commands: STACK_PATTERN, AWS_REGION, AWS_PROFILE
-
Run
cfn-teardown -hand see available commands and needed parameters. -
Listing stack dependencies:
cfn-teardown listDependenciesGenerates dependencies in
stack_teardown_details.jsonfile (printed in terminal as well) -
Tear down stacks:
cfn-teardown deleteStacksDeletes matching stacks and updates status in the teardown details file as the script is running.
For stacks with consistent naming convention:
Let's say you have stacks starting with the environment name followed by a hyphen:
- qa-shared-networks
- qa-service-user-management
- qa-service-user-search
In this can, you need to set stack pattern as ^qa- to match stacks starting with qa-.
For stacks which do not follow any naming pattern:
Example:
- qa-shared-networks
- service-user-management (depends on shared networks stack)
- user-search-service (depends on shared networks stack)
Use the root stack's name as the stack pattern i.e. ^qa-shared-networks. The script will find out all dependendent stacks from the root stack recursively until the leaf nodes have zero importer stacks.
Configuration for this command can be set in three different ways in the precedence order defined below:
-
Environment variables(same as flag name)
-
Flags e.g.
cfn-teardown deleteStacks --STACK_PATTERN=qaenv- -
Supplied YAML Config file (default: ~/.cfn-teardown.yaml)
Minimal config file
AWS_REGION: us-east-1 AWS_PROFILE: staging STACK_PATTERN: qa-
All configs present
AWS_REGION: us-east-1 AWS_PROFILE: staging TARGET_ACCOUNT_ID: 121212121212 STACK_PATTERN: qa- ABORT_WAIT_TIME_MINUTES: 20 STACK_WAIT_TIME_SECONDS: 30 MAX_DELETE_RETRY_COUNT: 5 SLACK_WEBHOOK_URL: https://hooks.slack.com/services/dummy/dummy/long_hash ROLE_ARN: "<arn>" DRY_RUN: "false"
See available configurations via: cfn-teardown <command> --help
-
Find matching stacks based on the regex provided
-
Prepare stack dependencies
It looks something like this:
{ "staging-bucket-archived-items": { "StackName": "staging-bucket-archived-items", "Status": "CREATE_COMPLETE", "StackStatusReason": "", "DeleteStartedAt": "2021-02-07T03:35:43Z", "DeleteCompletedAt": "", "DeletionTimeInMinutes": "", "DeleteAttempt": 0, "Exports": [ "staging:ItemsArchiveBucket", "staging:ItemsArchiveBucketArn" ], "ActiveImporterStacks": { "staging-products-service": {} }, "CFNConsoleLink": "https://console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/stackinfo?stackId=staging-bucket-archived-items" }, "staging-products-service": { "StackName": "staging-products-service", "Status": "CREATE_COMPLETE", "StackStatusReason": "", "DeleteStartedAt": "2021-02-07T03:30:54Z", "DeleteCompletedAt": "", "DeletionTimeInMinutes": "", "DeleteAttempt": 0, "Exports": [ "staging:ProductsServiceEndpoint" ], "ActiveImporterStacks": {}, "CFNConsoleLink": "https://console.aws.amazon.com/cloudformation/home?region=us-east-1#/stacks/stackinfo?stackId=staging-products-service" } } -
Alert slack channel(if provided) and waits before initiating deletion. Starts deletion immediately if no wait time is provided.
-
Select stacks which are eligible for deletion. A stack is eligible for deletion if it's exports are imported by no other stacks. In simple terms, it should have no dependencies.
-
Send delete requests for all selected stacks.
-
Wait for 30 seconds(configurable) before scanning eligible stacks again. Checks If the stack has been already deleted and if deleted updates stack status in the dependency tree.
-
This process (sending delete requests, waiting, checking stack status) is repeated until all stacks have status
DELETE_COMPLETE. -
If a stack is not deleted even after exhausting all retries(default 5), teardown is halted and manual intervention is requested.
Only AWS profile based authentication supported at the moment. By default, it tries to use the IAM role of the caller but we can also supply role arn if we want the script to assume a different role.
-
DRY_RUNflag must be explicitely set tofalseto activate delete functionality -
ABORT_WAIT_TIME_MINUTESflag lets us to decide how much to wait before initiating delete as you might want to confirm the stacks that are about to get deleted -
TARGET_ACCOUNT_ID: If provided, this flag confirms that the given aws account id matches with account id in the aws session during runtime to make sure that we are deleting stacks in the desired aws account
If a stack can't be deleted from the AWS Console itself due to some dependencies or some error, then it won't be deleted by this tool as well. In such case, manual intervention is required.
With great power, comes great responsibility
- First try within small number of test stacks in dry run mode.
- Use redundant safety flags
DRY_RUN,TARGET_ACCOUNT_IDandABORT_WAIT_TIME_MINUTES.