Quick utility to craft executables for pentesting and managing reverse shells.
Requires Python 3.5 or above.
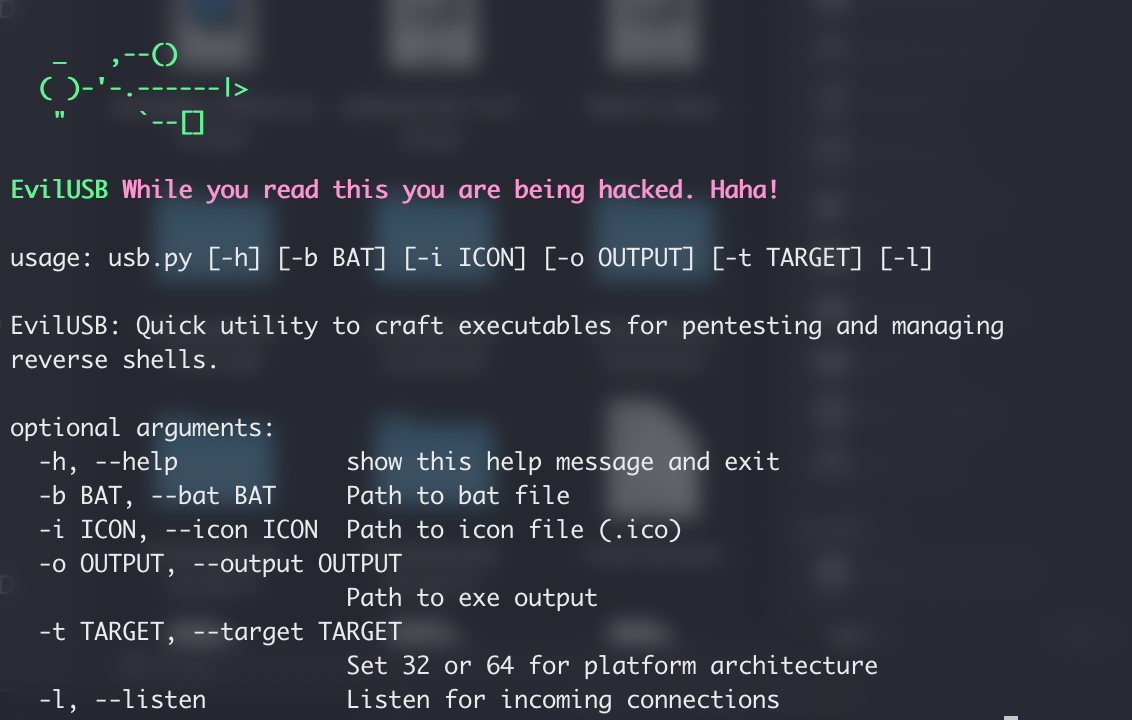
usage: usb.py [-h] [-b BAT] [-i ICON] [-o OUTPUT] [-t TARGET] [-l] [-p PORT]
EvilUSB: Quick utility to craft executables for pentesting and managing
reverse shells.
optional arguments:
-h, --help show this help message and exit
-b BAT, --bat BAT Path to bat file
-i ICON, --icon ICON Path to icon file (.ico)
-o OUTPUT, --output OUTPUT
Path to exe output
-t TARGET, --target TARGET
Set 32 or 64 for platform architecture (Default 32)
-l, --listen Listen for incoming connections
-p PORT, --port PORT Listening port (Default 4444)
Feel free to propose your modifications. It would be a great idea to have an option to send automatic payloads to Windows targets in order to escalate privileges or gain persistence.
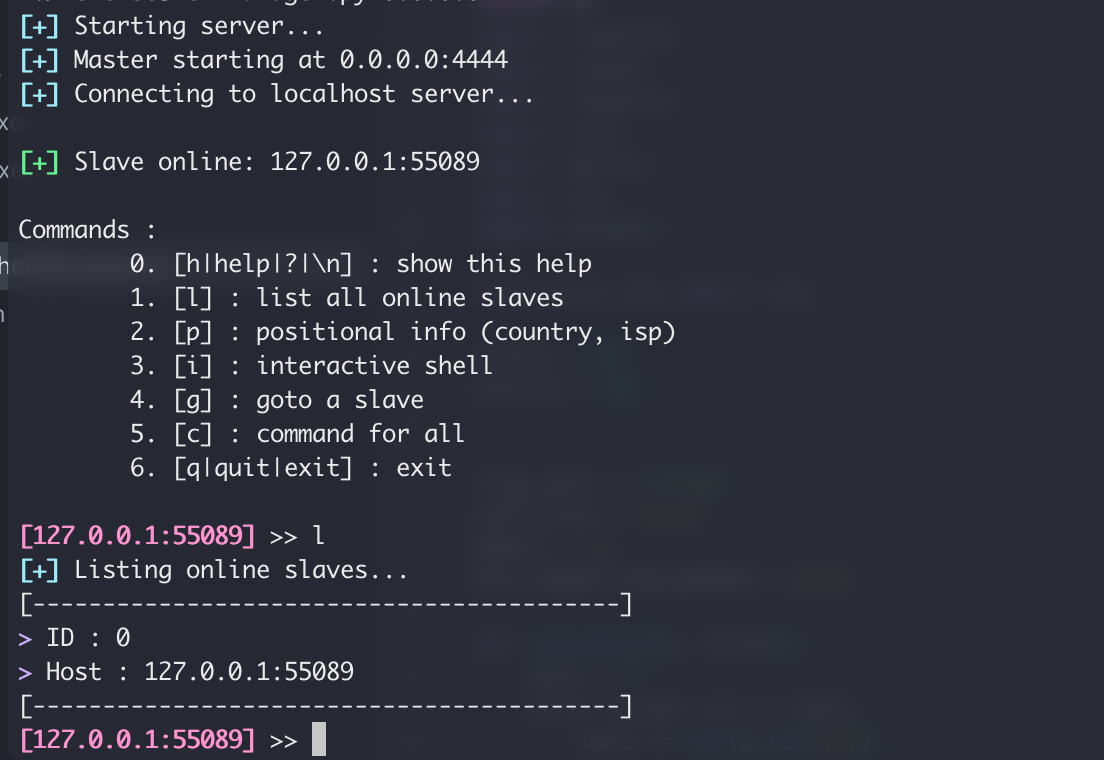
The reverse manager shell was based on Wang Yihang's project.
Thanks to jbelamor for the ideas and tips. This project was based on one of his.