Manual of resistance to surveillance capitalism - Based on Valentin Delacour version - v2022.08.01
- 0 Comments about fork
- 1 Introduction
- 2 Golden rules
- 3 Computer
- 3-1 Operating Systems
- 3-2 Services and programs
- 4 Smartphone
- 4-1 Operating Systems
- 4-2 Applications
- 5 Browsers
- 5-1 Extensions
- 5-2 Tor Browser
- 6 Service instances
- 6-1 Proxies
- 6-2 Videoconference
- 6-3 DNS Servers
- 7 Additional resources (featured sources)
- 8 Configurations
- 8-1 Operating systems for smartphones
- 8-2 Operating systems for computers
- 8-3 Applications
- 8-4 Services and Programs
- 8-5 Firefox and Add-ons
I have seen the need to fork this document of Valentin Delacour hosted here under his approval and license to give it more visibility, readability, comfort, improvement in some aspects and participation. If someone else forks both his and this one, they should do the same.
I think that we should share the more the better and the knowledge about good practices to follow regarding security, privacy and open source that are detailed are no exception.
We are open to changing the format of this document, for now I have thought that this is a good way, but it could be improved.
I don't consider myself an expert on the subject. In fact I do not follow all the recommendations to the letter. But I would like over time to leave aside services that I think I should not use for various reasons, change ways of accessing certain content, use other strategies, etc.
To actively participate you can:
I recommend you participate in:
The objective of the group is to collectively promote good customs in terms of privacy, security and also open source/free programs/apps, services and operating systems to resist the collection and exploitation of personal data by private companies.
I think that they take advantage of the ignorance of the majority to do things that they should not and benefit from it behind our backs. The good thing is that there are people who realize it because they understand the subject and share it with the community.
This document has been copied 1: 1 with very slight modifications in version 7/12/2020 and from now on it will undergo modifications following the following strategies:
- Following updates of the original file
- Pull requests from the community
- Own discoveries
The most notable improvements are:
- It encourages a more orderly, effective, public participation
- Images of the apps to better identify them
- Links to them to find them quickly
Now, the document begins. Put on your belt curves are coming!
The main goal of this document is to promote tools and alternatives in order to protect data and privacy from private companies predation taking place in the framework of surveillance capitalism current system. However, following this document’s recommendations also allows to improve, to some extent, protection against other actors interested in personal data such as State services or pirates.
This list is intended for every person understanding or becoming aware of what is at stake with data protection in our society, independently of one’s knowledge of the subject. It is not intended for individuals needing a total anonymity due to their sensitive functions such as political opponents or some journalists, even if some of the mentioned options could suit them. Indeed, privacy protection isn’t necessarily equivalent to anonymity.
The list format has been chosen in order to make the document’s reading the most efficient possible. Since this method prevents from detailing actual explanations, you are therefore encouraged to look for the ones you consider needed yourselves or in the additional resources in point 7 of the document. The goal being to promote the most reputed and practical options without being encumbered, the list is not intended to be exhaustive and remains subjective although aiming for the greatest impartiality possible.
In order to help to choose between the different options mentioned, this list offers a first subjective hierarchy (apparition order and parenthesis’ presence or not) based on the privacy/user friendliness ratio. A second hierarchy (colours) is solely based on the estimated privacy:
🟢green (real privacy respect)
🔵blue (respect for privacy under conditions or presence of problematic elements)
🔴red (does not protect or respect privacy but remains preferable to MAGMA options)
⚫colorless (dependence on external factors or lack of elements to form a relevant estimation). The presence of an asterisk indicates that the mentioned option still hasn’t reached maturity.
I hope this document will help you to improve your personal data protection and your relatives’ one. Although being the result of several years of researches and experiences, this work remains obviously perfectible. Any suggestion or remark is consequently more than welcome to the following email address: "privacyfirst@ik.me". Several months after the present document version, some informations given will be obsolete. This document being frequently updated, you are invited to obtain the latest version on the following webpage: "https://codeberg.org/PrivacyFirst/Data_Protection/issues".
- Always avoid using MAGMA (Meta, Amazon, Google, Microsoft and Apple) as well as chinese services and programs when possible. It is recommended to delete your accounts and replace them with a respectful alternative.
- Always review all the settings and authorizations of what is used and optimize them to limit the collection of personal data as much as possible.
- Only install the necessary programs/applications as they are potential accesses to your personal data.
- Use free/open source programs (their codes are public and also verifiable) instead of proprietary/closed source whenever possible.
- Favor the popular free options over the unknown ones (they will be more reviewed/reliable).
- If a company offers its services for free, in general, the product it sells is you (your personal data). Due to the model imposed by the surveillance capitalism, pay now or protect them from also being the product.
- Update your programs/operating systems frequently to benefit from the latest fixes for exploitable security flaws and think about replacing the ones that no longer seem to be up to date.
- Don't use third-party antivirus, they are true vacuum cleaners of personal data. Their contribution is negligible as long as good numerical habits are maintained. Prudence and a good configuration are the best antivirus.
- Privilege Web Apps or shortcuts from the browser to access services instead of applications to install to limit access and the possibilities of collecting personal information.
- Use temporary emails to create accounts for unimportant sites/services.
- Always disable Wi-Fi, Bluetooth, and geolocation on your smartphone when not in use and don't connect to public Wi-Fi without using a VPN.
- Do not use connected objects (their purpose is to collect as much personal data as possible) or not connect them to the internet when they are essential.
Windows currently is the worst operating system in terms of privacy. The only user friendly and, unlike macOS, truly privacy respectful operating systems are GNU/Linux distributions. There are a multitude of them which characteristics vary greatly. Here is a small selection of the ones offering the best user experience (always privacy respectful) or guaranteeing the best data protection. Each distribution offers one or several interfaces (desktop environments) that differ in terms of user experience and resource consumption. For security reasons, preferably favour one supporting Wayland such as Gnome or KDE Plasma. An abundant documentation is available online in order to help identifying which distribution and desktop environment will best suit the capacities of your computer and your personal preferences as well as to learn how to easily install it on your computer.
Desktop :
🟢![]() Fedora Workstation : secure and modern standards (beginner friendly)
Fedora Workstation : secure and modern standards (beginner friendly)
🟢![]() Linux Mint : ideal for beginners and great stability
Linux Mint : ideal for beginners and great stability
🟢![]() MX Linux : great stability and lightweight (beginner friendly)
MX Linux : great stability and lightweight (beginner friendly)
🟢![]() Zorin OS : ideal for beginners coming from Windows or macOS
Zorin OS : ideal for beginners coming from Windows or macOS
🟢![]() Parrot Home OS : system wide anonymity option through Tor (lightweight)
Parrot Home OS : system wide anonymity option through Tor (lightweight)
🟢![]() Fedora Silverblue : high security and modern standards (Flatpak centred)
Fedora Silverblue : high security and modern standards (Flatpak centred)
🟢![]() Qubes OS : extreme security for advanced users (heavyweight)
Qubes OS : extreme security for advanced users (heavyweight)
🟢![]() Whonix : anonymity through Tor and extreme security (to use in KVM or VirtualBox)
Whonix : anonymity through Tor and extreme security (to use in KVM or VirtualBox)
USB live (RAM) :
🟢![]() MX Linux : great stability and lightweight (beginner friendly)
MX Linux : great stability and lightweight (beginner friendly)
🟢![]() Tails : system wide anonymity through Tor and does not leave traces on the hardware
Tails : system wide anonymity through Tor and does not leave traces on the hardware
Raspberry Pi :
🟢![]() LibreELEC : multimedia center for TV
LibreELEC : multimedia center for TV
🟢![]() Batocera : console emulator, retrogaming and multimedia centre for TV (Kodi)
Batocera : console emulator, retrogaming and multimedia centre for TV (Kodi)
🟢![]() Raspberry Pi OS : classic operating system
Raspberry Pi OS : classic operating system
🟢![]() Plasma BigScreen* : multimedia center for TV (voice command with Mycroft AI)
Plasma BigScreen* : multimedia center for TV (voice command with Mycroft AI)
🟢![]() Nymphcast : free and environmentally friendly alternative to Chromecast
Nymphcast : free and environmentally friendly alternative to Chromecast
Hardware :
The following brands sell computers with Linux preinstalled :
Slimbook
Librem
TUXEDO Computers
Laptop with Linux
Juno Computers
Dell (some models)
Vant
PINE64
System 76
Entroware
Vikings
ThinkPenguin
Other lesser known pre-installed Linux computers sellers exist as well. As for companies selling computers with Windows pre-installed, Dell, Asus, Lenovo and HP models are known to offer a good compatibility with Linux. It is recommended to not buy computers that come with a Nvidia graphic card since they are known to suffer from compatibility problems.
Browser :
Search engine :
🔴![]() Startpage (Google proxy)
Startpage (Google proxy)
Instant messaging :
🟢![]() Jami
Jami
Video conferencing :
🟢![]() Jami
Jami
Mail :
⚫![]() Tutanota ⚫free 🔴paid
Tutanota ⚫free 🔴paid
Mail alias manager :
Video platform :
Youtube :
Translation :
🔵![]() DeepL 🔴free 🔵paid
DeepL 🔴free 🔵paid
🟢![]() Firefox Translations(extension)
Firefox Translations(extension)
🔴![]() DuckDuckGo (proxy Microsoft)
DuckDuckGo (proxy Microsoft)
🔴![]() Lingva Translate (proxy Google)
Lingva Translate (proxy Google)
Maps :
Respectful social network :
Abusive social network proxy :
🔵![]() Nitter (Twitter)
Nitter (Twitter)
🔵![]() Libreddit (Reddit)
Libreddit (Reddit)
🔵![]() Bibliogram (Instagram)
Bibliogram (Instagram)
🔵![]() ProxiTok (TikTok)
ProxiTok (TikTok)
Wikipedia Proxy :
Movies and series streaming :
🔴![]() Stremio 🔵without account 🔴with account
Stremio 🔵without account 🔴with account
🟢![]() Kodi
Kodi
Learning platform :
All-in-one ecosystem :
🔵Proton
🔴Infomaniak(sin ZKE)
Ads, trackers and undesired connexions blocker (firewall):
VPN :
🔵IVPN
Temporary email :
Encryption tool :
Metadata eraser :
Blurring or facial recognition resistance :
Network traffic monitor :
Password manager :
Antivirus (ClamAV) :
🟢ClamTK (Linux)
🟢ClamWin (Windows)
Potentially dangerous files sanitizer :
Flatpak permissions manager :
Calendar :
Office suite :
🟢![]() Collabora Office - LibreOffice prof.
Collabora Office - LibreOffice prof.
Notes :
PDF reader :
🟢Sumatra PDF
🟢Okular(KDE)
🟢Evince(Gnome)
Collaboration and organization :
🟢Collabora(profesional)
🟢Skiff
File sharing :
Cloud :
![]() Kdrive 🔴free 🔵paid
Kdrive 🔴free 🔵paid
Backup tool :
🟢Déjà Dup(local)
Synchronisation tool :
Multimedia streaming (self-hosted) :
🟢Jellyfin
🟢Subsonic
Computer – smartphone connexion :
🟢GSConnect
🟢KDE Connect
🟢Zorin Connect
Music player :
🟢Music(Gnome)
🔵Lollipop(Gnome)
🟢Rhythmbox
Multimedia player :
🟢![]() mpv
mpv
🟢![]() VLC
VLC
🟢Kodi
Graphics editor and drawing :
🟢![]() Gimp
Gimp
🟢KolourPaint(KDE)
Pictures editor :
Vectorial drawing :
Layout and edition programm :
Audio edition :
🟢![]() LMMS
LMMS
Video edition :
🟢Blender
🟢Shotcut
CD/DVD burner :
🟢![]() k3b
k3b
Transcoding :
🟢![]() MKV
MKV
Windows programs/games on Linux :
⚫![]() Wine
Wine
Cleaning and system optimisation :
Internet radio :
RSS reader :
Operating system emulator (virtualization) :
🟢![]() KVM
KVM
Android, in its default configuration, is the worst operating system with regard to privacy. Its goal is to continuously send its users’ personal data to Google servers in order to exploit and resell them. The most recommendable solution currently is to use an Android version (custom ROM) modified to respect privacy.
If you do not wish to install or buy a smartphone with a respectful OS (big mistake) and you nevertheless choose to use default Android, follow the few advices detailed in point 8.1 in order to limit as much as possible personal data collection. Apple’s operating system (iOS), in spite of its marketing revolving around privacy, collects and exploits as well the personal data of its users, in addition to considerably limit their freedom.
Linux based options are privacy respectful and promising it terms of independence although they do not offer the same guarantees as Android regarding security. Furthermore, in their current state of development, they are not recommendable for average users (excepting Sailfish OS).
Android modified for privacy: :
🟢![]() GrapheneOS : the most secure and private degoogled Android available
GrapheneOS : the most secure and private degoogled Android available
🔵![]() DivestOS : degoogled LineageOS partially improved for security and privacy
DivestOS : degoogled LineageOS partially improved for security and privacy
🔵![]() CalyxOS : Android partially degoogled but with microG (better compatibility)
CalyxOS : Android partially degoogled but with microG (better compatibility)
🔵![]() /e/ OS : partially degoogled LineageOS but with microG and cloud services
/e/ OS : partially degoogled LineageOS but with microG and cloud services
🔵![]() Volla OS: degoogled LineageOS (locked bootloader)
Volla OS: degoogled LineageOS (locked bootloader)
🔴![]() LineageOS for microG : LineageOS with microG for a better apps compatibility
LineageOS for microG : LineageOS with microG for a better apps compatibility
🔴![]() LineageOS : Android without Google apps but not degoogled (unlocked bootloader)
LineageOS : Android without Google apps but not degoogled (unlocked bootloader)
Pre-installed hardware :
🔵Volla Phone : Volla OS (or Ubuntu Touch)
🔵Fairphone 4 : /e/OS with locked bootloader, only available on (https://murena.com)
🔴Teracube 2e : /e/OS with unlocked bootloader, only available on (https://murena.com)
🔴Pinephone Pro : Manjaro and other compatible Linux OS
Other /e/OS smartphones with unlocked bootloader available on (https://murena.com)
The suggested applications for Android (and derived) should be searched in the first place in the Free app store Neo Store (F-Droid), guarantee that no third party tracker is present, and only if they aren’t available there, in Aurora Store, a Google Play respectful client which allows to access anonymously to its free applications. Please see point 8.3 for all necessary explanations.
Android and derivates :
Browser :
🟢![]() mull
mull
Instant messenger :
🟢![]() Jami
Jami
Videoconference :
🟢![]() Jami
Jami
Email client :
Email aliases manager :
Video platform :
🔵LibreTube(proxy YouTube)
🔴![]() Newpipe (🔴Youtube client 🟢PeerTube)
Newpipe (🔴Youtube client 🟢PeerTube)
🔵Librarian web app(proxy Odysee)
Maps/GPS navigation :
🟢Organic Maps
Translation :
🟢LibreTranslator
🔴DeepL(no oficial)
🔴SimplyTranslate Mobile(proxy Google)
Respectful social network :
🔵![]() Tusky (Mastodon)
Tusky (Mastodon)
🔵![]() Element (Matrix)
Element (Matrix)
🔵![]() Fedilab Mastodon, Pleroma...),
Fedilab Mastodon, Pleroma...),
🔵PixelDroid (PixelFed)
Abusive social network :
⚫Fritter(Twitter sin cuenta)
⚫Infinity for Reddit
⚫Twire(Twitch)
⚫Navegador internet
Movies and series streaming :
🟢CloudStream
🟢![]() Kodi
Kodi
Ads/trackers blocker :
🟢DoT de Android
🟢TrackerControl
Links redirector and cleaner (abusive => respectful) :
Network traffic controller (firewall) :
Third party trackers revealer :
Network anonymization through Tor :
VPN :
🟢IVPN
Pictures metadata eraser and blurring :
🟢ExifEraser
🟢PrivacyBlur
App isolator :
🟢diferente perfil usuario de Android(
Microphone blocker or monitor :
🟢PilferShush Jammer
🟢Vigilante
Google Services replacement :
🔴GmsCore
Password manager :
🟢AuthPass(KeePass)
Two-factor authentication :
Malware scanner :
🟢Hypatia(ClamAV)
Keyboard: :
Calendar :
🟢Proton Calendar
🟢Proton Calendar*
🟢![]() Etar
Etar
Camera :
🟢Secure Camera
Gallery :
File manager :
🟢Material Files
🟢Ghost Commander
Notes :
🟢SilentNotes
🟢Noto
🟢jtx Board
🟢Orgzly
SMS :
Weather :
🟢Geometric Weather
🟢Weather
🟢Clima
Audio player :
🟢Metro
🟢Auxio
PDF readeer :
🟢Secure PDF Viewer
Contacts :
Audio recorder :
Phone calls manager :
Calculator :
🟢OpenCalc
Clock :
Multimedia player :
🟢![]() VLC
VLC
🟢![]() Kodi
Kodi
Synchronisation tool :
⚫DAVx5(servidor elegido).
File sharing :
🟢Warpinator(local)
🟢Sharik(local)
Cloud :
🔵Filen
Cloud encryption tool :
Smartphone – computer connexion :
🟢KDE Connect
🟢Zorin Connect
Web Apps creator :
🟢Mull
🔵Bromite
QR codes scanner :
⚫Secure Camera
⚫QR & Barcode Scanner
⚫QR Scanner
Office suite :
🟢![]() Collabora Office - LibreOffice prof.
Collabora Office - LibreOffice prof.
🟢LibreOffice
RSS feed reader :
🟢Feeder
🟢Read You
🟢News
🟢Handy News Reader
Podcasts manager :
🟢AntennaPod
🟢News
Internet radio :
🟢Transistor – Simple Radio App
Music streaming :
🟢Finamp(Jellyfin)
🟢Subtracks(Subsonic)
🔴Musify(YouTube)
E-book reader :
🟢Librera Reader
🟢KOReader
Respectful interface for smart devices :
⚫Gadgetbridge
Finances :
🟢Unstoppable Wallet
🟢MoneyBuster
🟢Sushi – Personal Finance
Health and Fitness :
🟢OpenFoodFacts
🟢Feeel – home workouts
🟢FitoTracker
🟢openScale
Launcher :
🟢Simple App Launcher
🟢Discreet Launcher
🔵Neo Launcher
Browser (Safari based) :
⚫Firefox Focus
Instant messenger :
🟢![]() Jami
Jami
Videoconference :
🟢![]() Jami
Jami
Email client :
Email aliases manager :
Video platform :
🔵Piped web app(proxy YouTube)
🔵![]() Librarian web app(proxy Odysee)
Librarian web app(proxy Odysee)
Maps/GPS navigation :
🟢Organic Maps
🔵OsmAnd
🔵Magic Earth
Respectful social network :
🔵Mastodon for iPhone
🔵Element(Matrix)
Abusive social network :
⚫Navegador internet
Ads/trackers blocker :
🟢DNS de iOS(ajustes Wi-Fi)
Network anonymization through Tor :
🟢Orbot
VPN:
🔵Mullvad VPN
🔵ProtonVPN
🔵IVPN
Password manager :
⚫![]() Strongbox(KeePass) - KeePass & PwSafe
Strongbox(KeePass) - KeePass & PwSafe
Two-factor authentication :
⚫Raivo OTP
Cloud :
🟢ente Photos
🔵Filen, Nextcloud(auto alojado), (kDrive(sin ZKE))
Cloud encryption tool :
Office suite :
🟢Collabora Office(LibreOffice)
Compartmentalization (using different browsers, with different configurations, de pending on the tasks) is a recommended method in order to protect privacy without sacrificing too much browsing comfort. As an example, the use of Firefox with a restrictive configuration (cf. 8.5) for general browsing. Then, the use of LibreWolf or another profile of the same Firefox configured in a less restrictive way for the websites not displaying correctly or or requiring a connexion to a personal account and another browser to access the most recalcitrant websites to privacy protection (Brave or Ungoogled Chromium in their default configurations are ideal for this purpose). We can also think about a browser solely dedicated to e-banking or Tor Browser for anonymous browsing.
Add-ons are extensions used to add features to the browser. It is recommended to install the least possible and only trustworthy ones since they can have access to the entirety of the browsing and that their usage can be identified by visited websites and thus be used for tracking purpose (fingerprinting). Some of the following extensions are only available for Firefox and its derivatives such as LibreWolf or Mull. Their configurations are detailed in point 8.5.
Recommended extensions :
![]() uBlock Origin - Chrome - Firefox
uBlock Origin - Chrome - Firefox
LocalCDN
LibRedirect
KeePassXC
Bitwarden (if used)
![]() CanvasBlocker - Chrome - Firefox
CanvasBlocker - Chrome - Firefox
Tor’s concept is to route internet traffic through a network anonymizing it. In order for your browser’s fingerprint (given among others by its configuration) not to reveal your identity by its uniqueness, Tor browsers are designed to have the same fingerprint independently from its users. In order to avoid to make your Tor Browser’s fingerprint unique, it is recommended not to install add-ons or to make modifications in the "about:config" settings. If you need the anonymity provided, it is obviously necessary as well not to connect to accounts that would compromise it. Tor network’s anonymization method significantly slows down loadings. Thus, it is not recommended to use it for streaming or sizeable downloads.
The following proxies allow to have access to the content of abusive platforms or services without handing over personal informations to them. However, all their different instances do not necessarily provide the same guarantees regarding privacy protection (IP addresses log or not, etc.). It is recommended to use the browser add-on LibRedirect (cf. 8.5) in order to automatically redirect links of abusive platforms to a respectful proxy and to distribute the activity between several instances of a same proxy in order to prevent a single one from having access to the whole activity content.When using the smartphone, use the application UntrackMe.
With regard to the :
🔵![]() Nitter (Twitter)
Nitter (Twitter)
🔵![]() Libreddit (Reddit)
Libreddit (Reddit)
🔵![]() Bibliogram (Instagram)
Bibliogram (Instagram)
🔵![]() ProxiTok (TikTok)
ProxiTok (TikTok)
please refer directly to the lists included in LibRedirect and UntrackMe.
SearXNG is a FOSS metasearch engine providing the combined results of traditional search engines (Brave Search, Google, Bing, etc.) without giving away the users’ personal data to them. It allows a particularly advanced configuration.
Available instances : ⚫https://searx.space
Recommanded instances (no IP log) : 🟢https://search.sapti.me (Germany)
🟢https://search.disroot.org (Netherlands)
🟢https://search.privacyguides.net (USA)
Piped and Invidious give access to YouTube content without handing over users’ personal data to Google. As for Invidious, depending on the instance, the proxy hiding the IP address isn’t always activated by default. If so, it must be manually activated inthe instance settings. Librarian gives access to the content of Odysee/LBRY (abusive as well).
Invidious instances : ⚫https://api.invidious.io
Recommended instances : 🟢https://yewtu.be (Netherlands)
🟢https://inv.riverside.rocks (USA)
Piped instances : ⚫https://github.com/TeamPiped/Piped/wiki/Instances
Librarian instances : ⚫https://codeberg.org/librarian/librarian
Jitsi Meet :
🟢https://www.kuketz-meet.de : No IP address log (Germany)
🟢https://meet.rollenspiel.monster : No IP address log (Germany)
🟢[Snopyta]https://talk.snopyta.org : No IP address log (Germany)
🔵[Calyx]https://meet.calyx.net : “Temporal” IP address log (United States)
🔵https://www.meet.roflcopter.fr : “Anonymized” IP log (Germany/France)
🔵[Jitsi]https://jitsi.uner.edu.ar : No privacy policy (Argentina)
BigBlueButton :
🔵Grifon France
🔵Nixnet United States
If you use a VPN, it is recommended to not change the default DNS server, in order to not stand out from its other users. Otherwise, replace the DNS server provided by your internet service provider with a respectful among the following recommendations. Always use an encrypted implementation (DoH, DoT, etc.) when it is possible.
🟢AdGuard : advertising, trackers and malicious domains blocking (intercontinental) DoH : https://dns.adguard.com/dns-query DoT : dns.adguard.com
🟢Mullvad : advertising, trackers and malicious domains blocking (intercontinental) DoH : https://adblock.doh.mullvad.net/dns-query DoT : adblock.doh.mullvad.net
🟢BlahDNS : advertising, trackers and malicious domains blocking (Europe et Asia) DoH (Alemania) : https://doh-de.blahdns.com/dns-query DoT (Suiza) : dot-ch.blahdns.com
🟢Control D : advertising, trackers and malicious domains blocking (intercontinental)
🔵Quad9 : malicious domains blocking (intercontinental)
🔵NextDNS : customizable blocking (intercontinental)
General informations
Excellent resources to better understand surveillance capitalism and its threats :
- Nothing to Hide, Marc Meillassoux (documentary)
- El dilema de las redes sociales, Jeff Orlowski (documentary)
- La era del capitalismo de la vigilancia, Shoshana Zuboff (book)
- Diez razones para borrar tus redes sociales de inmediato, Jaron Lanier (book)
Excellent channel about privacy (with tutorials) :
- The Hated One (LibreTube, Newpipe, Invidious o Piped)
Associations for privacy defence :
Specific informations
Excellent tutorials for privacy and data protection :
Complete :
- https://ssd.eff.org
- https://privacyguides.org
- https://dt.gl/privacy-cookbook-the-story-so-far-april-2022
Advanced :
Basic :
- https://spreadprivacy.com/tag/device-privacy-tips (pro DuckDuckGo bias)
- https://www.vice.com/en_us/article/d3devm/motherboard-guide-to-not-getting-hacked-online-safety-guide (pro Apple bias)
Android and derivates :
- The excellent GrapheneOS documentation : https://grapheneos.org/faq
- DivestOS : https://divestos.org
- /e/ OS : https://e.foundation
- Apps compatibility with and without microG : https://plexus.techlore.tech
Firefox and derivates configuration :
VPN use cases and limitations :
Services
Associations offering excellent privacy respectful services :
Privacy respect evaluation of different services :
Websites security evaluation tool :
Privacy and FOSS groups
Telegram :
Matrix :
- #privacy:matrix.org
- #main:privacyguides.org
Global recommendations for Android and derivatives
- see point 4.2 and 8.3 in order to install applications without using Google Play Store
- verify all applications’ permissions in order to revoke them if they are harmful to privacy or simply unnecessary : “Settings” > “Apps” > select the app > “Permissions”
- block the internet access of all unused applications or which do not require internet access in order to work in the apps’ permissions or when it’s not available, thanks to a firewall application such as RethinkDNS
- install and use an application, such as RethinkDNS (cf. 8.3), allowing to block trackers as well as ads and to use a respectful encrypted DNS server (cf. 6.3). As an inferior alternative, use the built-in Android DoT implementation to set a recommended DNS server (DoT) (cf. 6.3): “Settings” > “Network & internet” > “Private DNS” > select “Private DNS provider Hostname” and enter the desired DNS server
- If it is necessary to use abusive applications requiring permissions to function, switch temporarily to a second user profile (or several ones) in order to totally isolate your activities and these applications from the rest of your data: “Settings” > “System” > “Multiple users” > “+ Add user” To receive notifications across different profiles: “Settings” > “System” > “Multiple users” > “Send notifications to current user” (repeat for each desired profile)
Android (original)
The following measures being insufficient for privacy since the OS is abusive in itself, it is recommended to use an Android version modified for privacy (cf. 4.1). That being said, in order to avoid a complete and continuous profiling with original Android:
- avoid all Chinese manufacturers as well as Samsung and favour a brand offering “Android One” (no manufacturer overlay)
- never connect to a Google account
- replace the default applications (especially the keyboard) which can spy on you with the FOSS and respectful ones recommended in point 4.2.
- deactivate all abusive (Google, third party antivirus, etc.) or unused applications and block their internet access (uninstall them when possible)
GrapheneOS
GrapheneOS integrates a powerful built-in firewall, directly in the applications’ settings, which allows you to block totally the internet access of the desired applications. Take this opportunity to deactivate the internet access of all the applications which do not require it in order to work:
“Settings” > “Apps” > select an app > “Permissions” > “Network” > “See all apps with this permission”
Take as well advantage of the option only offered by GrapheneOS to remove the permission to access sensors (insidiously used to collect informations and for tracking) to all commercial or closed source apps and to the ones that do not need it to work properly, as a precaution:
“Settings” > “Apps” > select an app > “Permissions” > “Sensors” > “See all apps with this permission”
CalyxOS
CalyxOS natively integrates a firewall, the application Datura, which allows you to block the internet access of the desired applications with a high degree of control. Take this opportunity to deactivate the internet access of all the applications which do not require it in order to work properly.
/e/OS
Beware, “ecloud” accounts do not have yet end-to-end encryption (planned). Thus it is strongly advised against using one with personal o important data.
For security reasons, it is advised to install and use the app stores Neo Store (F-Droid) and Aurora Store (cf. 4.2 and 8.3) instead of /e/OS’s own which is an imperfect implementation. Likewise, /e/’s default browser which is their own Bromite fork receiving belatedly security updates and with a unique fingerprint, should not be used. Install and use instead a more secure browser such as the ones recommended in the point 4.2.
Windows
The following recommendations being imperfect and not fully guaranteeing data protection, it is recommended to use a Linux distribution (cf. 3.1) rather than Windows. That being said, to avoid suffering from a complete and continuous profiling of your activity as well as your person with Windows, follow these recommendations:
- do not use any prior version to Windows 10 since they are vulnerable/insecure
- never connect to a Microsoft account
- fully deactivate Cortana
- deactivate activity history
- go in settings under "privacy" and deactivate everything in every category except the required authorisations for used applications
- uninstall (or when it’s not possible deactivate) Edge, Microsoft OneDrive, anti-viruses (except Microsoft Defender) and all unused applications
- activate random MAC address in Wi-Fi settings
- preferably use a session without admin privileges for daily usage
- install the program O&O ShutUp10++ in order to have more control over privacy
- install the program Portmaster from safing.io in order to fully control (and block) all inbound and outbound connexions with a high degree of control (manually and with preset blacklists to block trackers and ads) and to set a system wide encrypted DNS server (cf. 6.3)
Linux (general)
For security reasons, favour the installation of Flatpak programs and set their permissions thanks to the program Flatseal.
Wi-Fi configuration with NetworkManager:
Right click on the Wi-Fi icon > modify connections > select active Wi-Fi > under Wi-Fi select cloned MAC address > Random. Under IPv6 settings, select IPv6 privacy extensions: Activated (preferred temporary address).
MX Linux
Stop Pub (Advert Blocker): Select all options except "UNBLOCK" and confirm.
Neo Store (F-Droid) and Aurora Store
These app stores must be downloaded directly from their official source : https://github.com/NeoApplications/Neo-Store/releases/ https://auroraoss.com.
In order to install them, grant the permission to install unknown applications to your browser when prompted and then, remember to withdraw it for security reasons: Android “Settings” > “Applications” > browser used > “installation of unknown applications”
Remember not to connect to Aurora Store with a personal Google account. Use instead the anonymous one.
In order to find and install some applications from Neo Store, it is necessary to add their own repositories. To do that, go in Neo Store settings (top right), then under “repositories” (bottom symbol), add the repositories “DivestOS Official”, “Guardian Project Official” and the other desired ones for applications such as Bromite, Molly (Signal), NewPipe, Bitwarden or Collabora Office.
Mull
During the installation from Neo Store, make sure to select the “DivestOS Official” version instead of the F-Droid one, in order to benefit as quickly as possible from updates and thus from latest security patches. Mull is already mostly configured for privacy protection out of the box. However, it is necessary to install the uBlock Origin add-on from the menu and to set it as explained in point 8.5.
NewPipe
During the installation from Neo Store, make sure to select the “NewPipe upstream repository” version instead of the F-Droid one, in order to receive as quickly as possible the updates fixing possible malfunctions due to YouTube modifications from Google.
To use PeerTube with NewPipe: top left menu > press “YouTube” > select “FramaTube”
Telegram
Settings:
- “Privacy and Security” > “Security” > enable “Two-Step Verification” to protect your account
- “Privacy and Security” > “Secret chats” > disable “Link Previews” in order not to reveal to Telegram the shared links in secret chats
- “Data and Storage” > disable all under “Automatic media download” in order not to automatically download malware in public groups or channels
Always use “secret chats” (unavailable for Telegram desktop) in order for the conversations to be end-to-end encrypted:
Desired contact profile > the three dots at the top on the right > “Start Secret Chat”
RethinkDNS
Activate an encrypted DNS resolver (DoH):
- Android “Settings” > “Network & internet” > “Private DNS” > select “Off”
- open RethinkDNS > click on “START” > select “DNS” on top > Select “Other DNS” > select the “+” below > enter the DoH URL of a recommended DNS resolver (cf. 6.3) > click on “ADD” > tick in the list the entry which has just been added
Activate local blocklists to block trackers, ads and more: click on “DNS” on top > select “On-device blocklists” > click on “Disabled” > confirm “Download blocklists” > tick the desired blocklists (preferably all the lists under “Security” and “Privacy”) > click on “Apply”
UntrackMe
In order to redirect abusive links with UntrackMe, long press a link and select “share link”, then select the app UntrackMe, after click on the desired browser and then select “Always”.
LibreWolf
Since LibreWolf is already optimized for privacy protection, it is recommended not to change its main configuration nor the “about:config” settings in order to prevent altering its fingerprint, thus making it unique. Notable exception: see point 8.5 under “about:config configuration” to enable “privacy.resistFingerprinting.letterboxing”.
Beware, LibreWolf version for Windows does not automatically receive the updates. Thus it is important to manually get them from the official website (by reinstalling the installation .exe file), preferably about once a week, in order to benefit from the latest security patches.
Brave Search
Remember to deactivate telemetry (activated by default) :
Settings: “Show more” > “Anonymous usage metrics”
FreeTube
The following solution being imperfect, it is recommended to use an Invidious or Piped instance directly from the browser.
Use Invidious as a proxy in order to limit connections to Google servers:
Settings: - Player Settings : activate "Proxy Videos Through Invidious"
- Advanced Settings : enter a functional Invidious instance
In case of malfunction, change Invidious instance or simply deactivate "Proxy Videos Through Invidious".
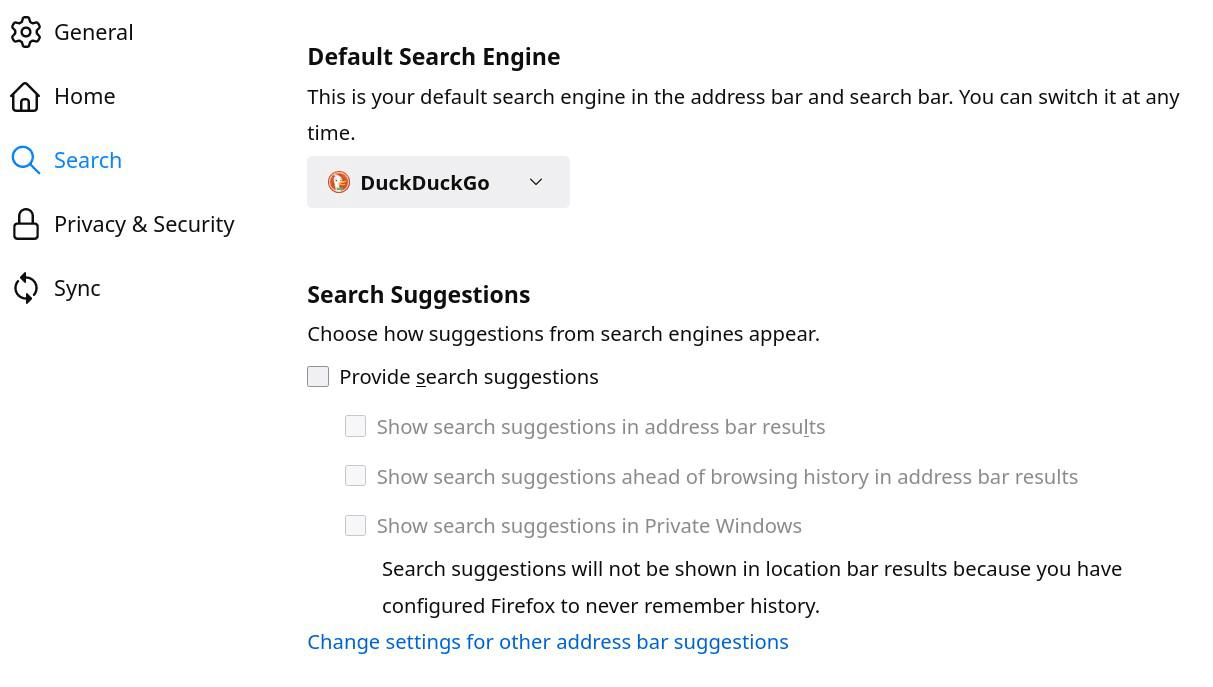
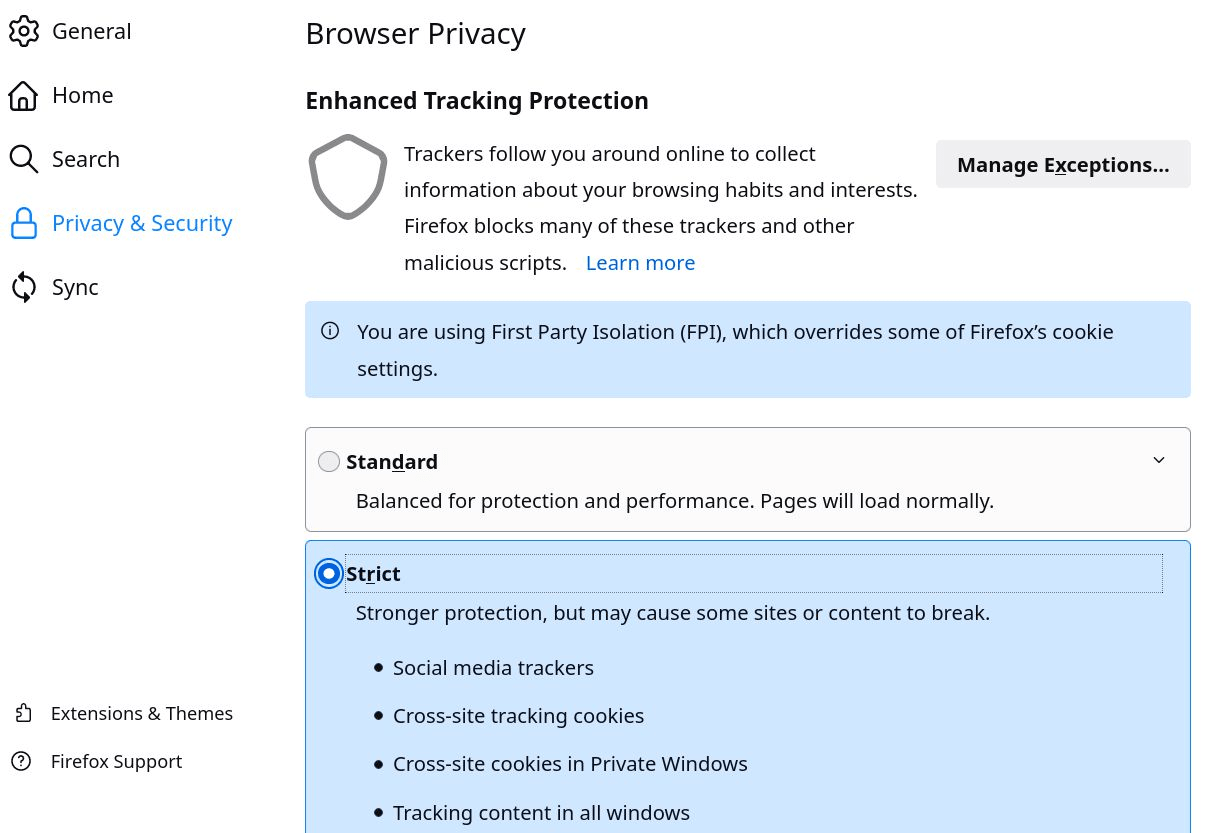
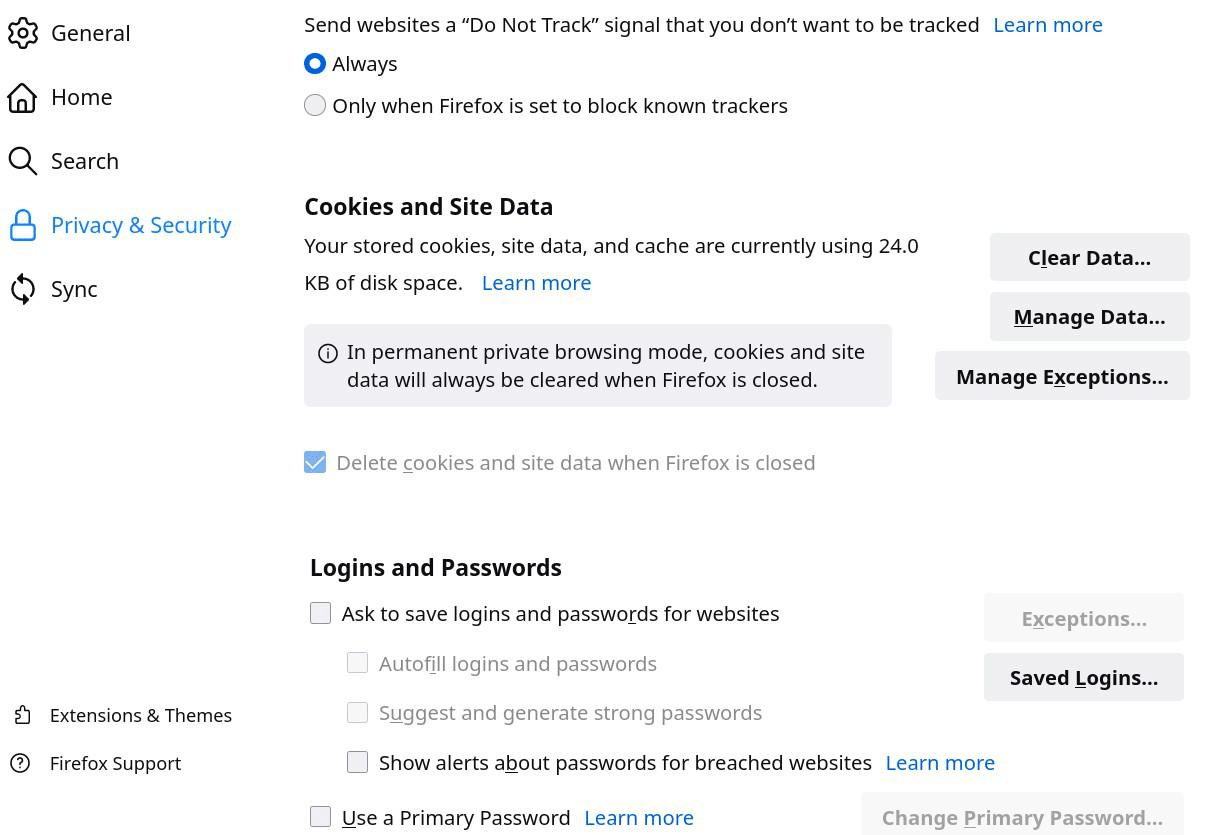
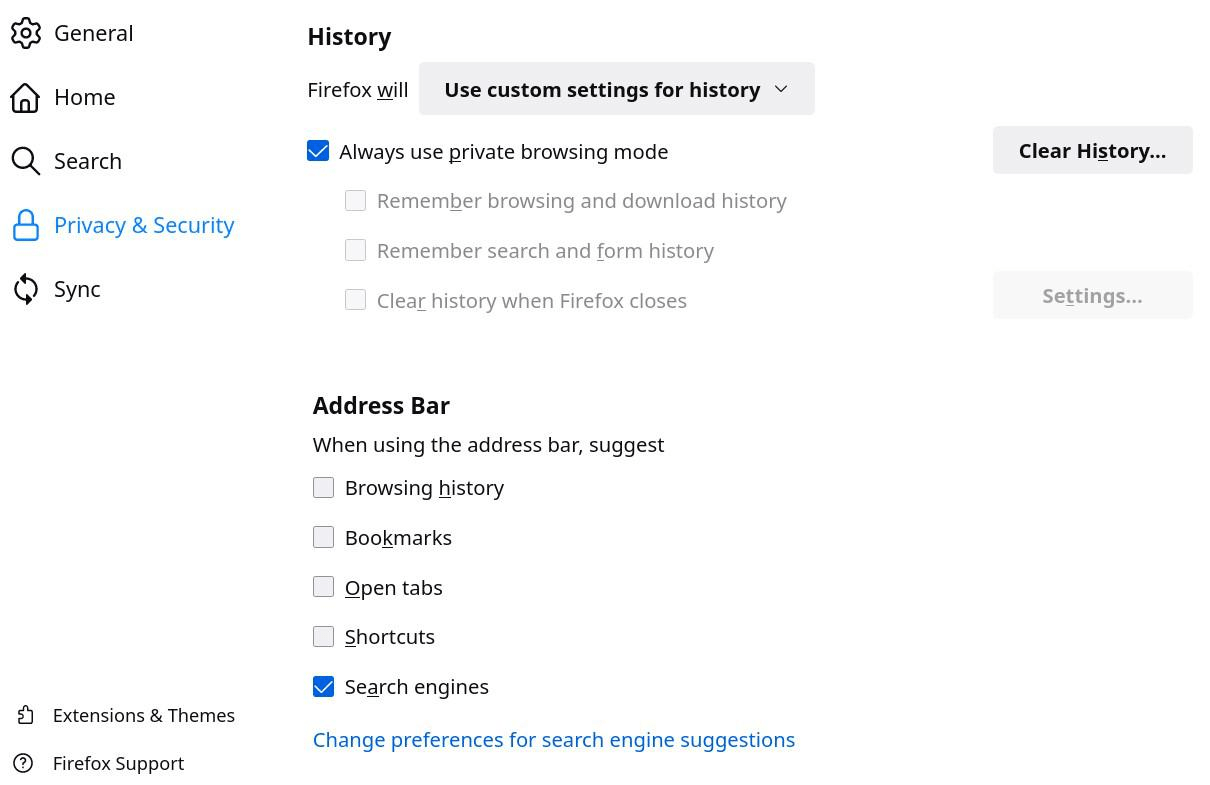
General configuration
In order for Firefox to protect privacy, it is necessary to configure it in an adequate manner. The configuration suggested below being relatively restrictive in order to protect the user’s privacy, it is recommended to practice compartmentalization as described in point 5 of the document and thus to use at least another browser or profile in order to be able to access the websites most recalcitrant to privacy protection.
Profiles :
Firefox offers the possibility to use several different profiles (configurations) at the same time. It’s the ideal solution to quickly and easily switch from a restrictive configuration preventing a website to load correctly to a more flexible one, without having to switch to a different browser. All the settings made, add-ons installed or bookmarks added will be saved in the profile in use. In order to access Firefox’s different profiles, enter "about:profiles" in the URL bar. This page allows you to create new profiles and then to launch them in a new independent window, at any time, by clicking on the button "Launch profile in new browser" under the desired profile.
Language :
In order to prevent being fingerprinted with the use of another language than the most common amongst Firefox’s users, it is recommended to set “English (United States)” as the browser’s language. In order to do that: Top right menu > “Settings” > under “General” > “Language” > click on the current language > “Search for more languages” > “Select a language to add” > “English (United States)” > “Add”
Additionally, deactivate “Check your spelling as you type”.
DNS over HTTPS :
If you are using a VPN or that your network or computer are configured to globally use a respectful and encrypted DNS server, the function "DNS over HTTPS" on by default, should be deactivated in order not to bypass the global setup. If it is not the case (if you don’t know then it’s probably not the case), it is recommended to let this function activated. However, it is necessary to change the default DNS server since Cloudflare is a centralizing actor nefarious for privacy. In place of the latter, it is recommended to choose a respectful option suggested in point 6.3 of the document, depending on your preferences and geographical location. To do this: "General" > all the way down "Network settings" > "Enable DNS over HTTPS"
under “Use Provider” select “Custom” > enter the URL of the desired Doh server.
To be continued, the rest of the general recommended configuration with images :
Add-ons configuration
It is important to authorize the following add-ons to work in private navigation and to activate their automatic updates.
uBlock :
- Settings: tick “I am an advanced user” and tick everything under "Privacy"
- Filter Lists: activate ALL lists except under "Regions" (only activate for used lan- guages) The lists under “Annoyances” and “Multipurpose” can prevent abusive social networks from working
- Add the following lists from filterlists.com: Energized: “Actually Legitimate URL Shortener Tool” (replaces ClearURLs), “Energized Ultimate Protection”, “Energized IP Extension”, “Energized Social Extension”, (“Energized Xtreme Extension”) To add a list from filterlists.com : click on the list’s left button > click on "Subscribe" in the menu appearing
- Follow this website’s tutorial for dynamic filtering rules: https://www.maketecheasier.com/ultimate-ublock-origin-superusers-guide
LocalCDN :
In the settings go to "Advanced" > under "Generate rule sets for your adblocker" select uBlock > copy the rules given > open uBlock Origin extension > in its settings go under "My rules" > paste the copied rules in the part on the right > clic on "Save" > Clic on "Commit".
LibRedirect :
Settings: - Enable or disable platforms and instances of your choice (cf. 6.)
- “YouTube” > “Default Instances” > only activate “https://yewtube.be“ and “https://inv.riverside.rocks”
(CanvasBlocker) :
No further configuration required Note: only use this add-on if “privacy.resistFingerprinting” does not suit you. Otherwise, it is generally more recommendable to activate this parameter in “about:config” (cf. following pages) instead of this add-on.
about:config configuration
Access to those settings by entering "about:config" in Firefox address bar. Those different settings improve privacy, security and, to some extent, performances. The elements between parenthesis are not advisable in all cases.
accessibility.blockautorefresh = true ((accessibility.force_disabled = 1)) beacon.enabled = false browser.backspace_action = 1 browser.cache.offline.capacity = 0 browser.cache.offline.enable = false browser.display.use_document_fonts = 0 browser.send_pings.max_per_link = 0 browser.sessionhistory.max_entries = 15 Nombre maximum de pages disponibles pour "précédent", allège Firefox browser.sessionhistory.max_total_viewers = 4 Nombre maximum de pages chargées pour "précédent", allège Firefox browser.sessionstore.interval = 50000 browser.sessionstore.privacy_level = 2 browser.urlbar.autofill.enabled = false browser.urlbar.speculativeConnect.enabled = false browser.urlbar.trimURLs = false browser.xul.error_pages.expert_bad_cert = true captivedetect.canonicalURL = supprimer device.sensors = false pour tous les éléments dom.allow_cut_copy = false dom.battery.enabled = false dom.enable_performance = false dom.enable_resource_timing = false dom.event.clipboardevents.enabled = false dom.event.contextmenu.enabled = false dom.image-lazy-loading.enabled = false dom.push = false pour tous les éléments + supprimer les adresses et identifiants dom.serviceWorkers.enabled= false dom.vr.oculus.enabled = false dom.webaudio.enabled = false gamepad = false pour tous les éléments geo = supprimer les adresses geo.enabled = false (gfx.font_rendering.graphite.enabled = false) google = false pour tous les éléments + supprimer les adresses javascript.options.baselinejit = false javascript.options.ion = false javascript.options.native_regexp = false layers.acceleration.force-enabled = true layout.css.visited_links_enabled = false mathml.disabled = true ((media.gmp-widevinecdm.enabled = false)) ((Désactive DRM, si vidéos DRM pas nécessaires)) media.navigator.enabled = false media.peerconnection.ice.default_address_only = true media.peerconnection.ice.no_host = true ((media.peerconnection.enabled = false)) media.video_stats.enabled = false network.captive-portal-service.enabled = false network.dnsCacheEntries = 4000 network.dnsCacheExpiration = 43200 network.dnsCacheExpirationGracePeriod = 43200 network.dns.disablePrefetch = true network.IDN_show_punycode = true network.http.referer.XOriginPolicy = 0 network.http.referer.XOriginTrimmingPolicy = 2 network.http.referer.spoofSource = true network.http.referer.trimmingPolicy = 2 network.http.speculative-parallel-limit = 0 network.manage-offline-status = false network.prefetch-next = false network.security.esni.enabled = true normandy = false pour tous les éléments + supprimer les adresses et identifiants pdfjs.enableScripting = false pocket = false pour tous les éléments + tout supprimer privacy.clearOnShutdown.offlineApps = true privacy.query_stripping.enabled.pbmode = true privacy.resistFingerprinting = true (Let "false" if you choose to use CanvasBlocker) privacy.resistFingerprinting.letterboxing = true (Manually enter this hidden preference in the search bar to enable it) privacy.spoof_english = 2 privacy.trackingprotection.enabled = true privacy.trackingprotection.socialtracking.enabled = true report (reporter/reporting) = false pour tous les éléments + supprimer les adresses safebrowsing = false pour tous les éléments + supprimer les adresses et identifiants security.cert_pinning.enforcement_level = 2 security.mixed_content.upgrade_display_content = true security.OCSP.enabled = 0 security.ssl.enable_false_start = false security.ssl.enable_ocsp_must_staple = false security.ssl.enable_ocsp_stapling = false security.ssl.require_safe_negotiation = true security.ssl3.rsa_des_ede3_sha = false security.tls.enable_0rtt_data = false security.tls.version.min = 3 telemetry = false pour tous les éléments + supprimer les adresses et identifiants ui.use_standins_for_native_colors = true webgl.disabled = true webgl.enable-debug-renderer-info = false webgl.enable-webgl2 = false