-
-
Notifications
You must be signed in to change notification settings - Fork 28
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Support HTTPS #27
Comments
|
Bonjour Nicolas, PG |
|
Ce n'est pas une question de difficulté d'installation. Le problème est double :
|
|
Bonjour Nicolas, Merci pour ta réponse. Ce sont là deux points dont j'avais eu effectivement l'intuition. Cependant, en vadrouillant un peu pour en connaître davantage sur les certificats SSL et HTTPS, j'ai plutôt fini par penser qu'on trouverait une solution :
Il me semble que ta réponse confirme ma vision : rien d'insurmontable pour une personne de ton niveau en informatique ! Nota : je crains cependant que nous garderons toujours des avertissements sur la qualité du certificat auto-attribué. Chaque client devra accepter et enregistrer une clef privée lors de la première connexion. A bientôt, |
C'est pour cela que je vais tenter de faire un "vrai" certificat avec Let's encrypt. |
|
As expected, non-public root domain isn't allowed by Letsencrypt. $ sudo certbot certonly -d moodlebox.home --manual --register-unsafely-without-email --preferred-challenges dns
(several lines omitted)
Obtaining a new certificate
An unexpected error occurred:
The request message was malformed :: Error creating new authz :: Name does not end in a public suffix
Please see the logfiles in /var/log/letsencrypt for more details. |
|
Explanation here: https://www.reddit.com/r/sysadmin/comments/3vyjd9/letsencrypt_non_public_domain/
|
|
Steps required:
|
|
Last point of checklist (Configure automatic renewal of certificate) seems unfortunately no doable: the owner of the domain has to modify the TXT record for each renewal, which is impractical for all the MoodleBoxes in the field, unless it has its own unique domain name. I'm afraid I can't add this feature in the standard image. |
|
Hi Nicolas, Therefore I was searching for some ideas to get a ssl certificate into the Raspberry Pi. What do you think about these ideas?
Best regards, Ralf |
|
I don‘t know of the ssl certificate of a local web server must be updateted online? Therefore the certificate update process should run only when the MoodleBox is connected and online via ethernet. This would be the same condition as needed for time synchronisation or for an updated DNS entry. What will happen when the ssl certificate gets invalid and the MoodleBox is not connected to the internet? You wrote that the users must modify a text record for each renewal. There should be a script for the renewal process. An the url is the same for every MoodleBox. |
|
Hi Ralf, However, I've gotten in a dead end. First of all, as noted here, it is not possible to get a SSL certificate with a non-public root domain. So this will need to change the moodlebox.home FQDN to something like a public one, say moodlebox.me. This is not a problem (except that all the user will have to change their habits, which is bad), I've done it. Secondly, unfortunately though, I've not found any solution the renewal of certificate, since any MoodleBox installation will need a unique certificate, so we are in the situation where we'll have to ask LetsEncrypt different certificates each time for the same FQDN (see explanation here). If you have a solution, I'll be glad to hear you. |
|
Okay ... the problem can not be fixed with thousands of dynamic DNS entries for the MoodleBoxes all over the world. What do you think about a selfsigned certificate on the MoodleBox. The certificate can be installed with an installation script. The admin could start this script in the terminal or it can be started automatically. Yes, I know that every user will get a warning that a selfsigned certificate is not secure. But if every user will trust this certificate the connection should be secure. The web server could provide a download link for the certificate in a profile so every user is able to download it to his devices. A lot of working areas, universities and schools are using selfsigned certificates for their internal server communication and proxy servers. Every MoodleBox will generate its own cerificate. But what will happen when a user has more than only one MoodleBox? He can change the Wi-Fi from MoodleBox1 to Moodlebox4 and then he opens the url https://moodlebox.home. The Wi-Fi is different, but the url is the same. Would it be possible to accept a second profile for a second Wi-Fi but the same url? |
|
I'm afraid that the warning for a unknown (self-signed certificate) will not reassure much more than the one saying that the connection is not secure ;-) I understand that in a big institution, installing a certificate on managed devices is OK. But this is not doable in institutions where devices aren't managed. So I'm not so keen to add such complexity to all users, at least not until it's really blocking. Maybe I'll add some documentation about how to enable HTTPS on the MoodleBox and how to get oneself a self-signed certificate. What do you think? |
|
Yes. I think we should try a Moodlebox version with a selfsigned certificate. To make it a little bit easier for the admin all needed software should be installed and all directory folders should exist. I found some instructions which are showing a lot of installation steps ... no, this should be very easy with the MoodleBox. |
|
Good idea. I'll think I'll publish MoodleBox with an already generated a self-signed certificate, and with a configuration file for nginx prepared with commented out instructions (and documentation). With this done, one could make it with just editing 2 files (nginx and moodle config files). |
|
Tested: it works 👍 |
|
@ralf-krause: if you want to test yourself: login via SSH then
|
|
Yes, it works with https! Very nice! |
|
Hi Nicolas,
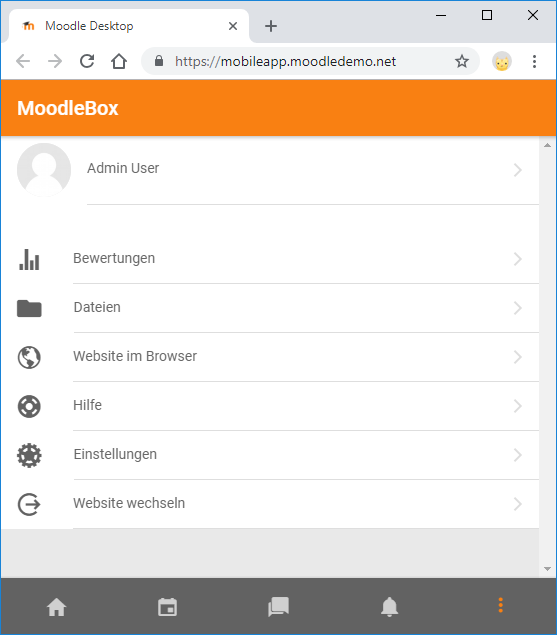
To have an easy access to the MoodleBox we should use it without https. Additional I found a blocker for the self signed certificate ... the Moodle Mobile app does not connect to the MoodleBox with this certificate even if the certificate is installed within a profile (.mobileconfig) and can be used by any app. |
|
Thanks for your feedback. In this case, I'm afraid we're out of luck. Seems there's no good solution for this. I'll leave this open for the moment, if someone have a genius idea. |
|
Will need documentation when (if?) feature is implemented. |
|
Hello @martignoni I just read through this case and think that the solution with Let's Encrypt and real public domains is not the right way. MoodleBox is mostly used in an intranet environment, isn't it? I think what we need to do is create a root certificate on each MoodleBox (i.e. host a own CA), which the user can then add to his "Trusted Certificates" on his client. With this solution it should be possible to generate a self-signed certificate for Moodle from this CA. After that, when the user accesses the platform, the verification chain should be verified as secure, as the root certificate is stored on the client side. So out of the box nginx is listening on port 80/443 but the Moodle wwwroot is per default Let me know what you think about that? I can give it a try. 😙 |
Overview
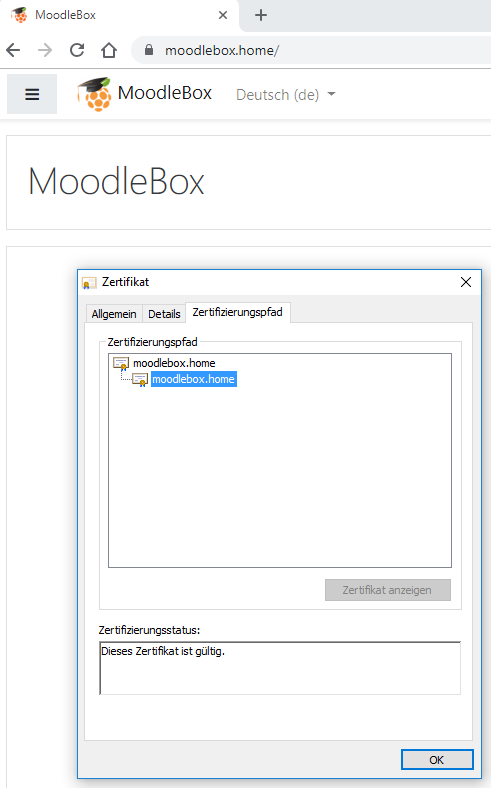
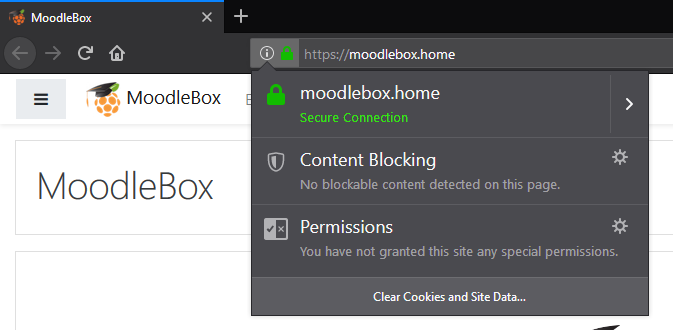
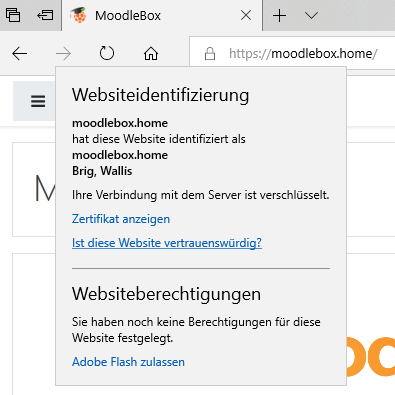
ResultsChromeI just made a straigtforward test and it seems to work with Chrome: You must only add the root certificate as trusted certificate authority on the client-side and the MoodleBox is then trusted: FireFoxWith FF you must import it directly in the browsers certificates storeage: EdgeEdge is working fine (doing the cert import on client, see above): SafariWith Safari I can't do a test... I don't own a Apple device. Moodle MobileIt should work with the Moodle Mobile App if the rootCA is present. I just don't figure out how to add this to my android device. But there's a Moodle Mobile Browser App for testing purposes with the same behaviour: |
|
Thanks. This is very interesting and could be a solution. Main issue then is the diversity of ways to add the root CA to the various browsers, which is unfortunately a mess in term of usability. Could you please point me to a "How to" creating such a root CA and the a SSL cert based on it? |
|
On my Win10 client it's only the FF which doesn't take the root certificate from the OS. I think most users uses Chrome. I used this as guide: https://medium.freecodecamp.org/how-to-get-https-working-on-your-local-development-environment-in-5-minutes-7af615770eec Update
What about a solution with ngrok? |
|
Hi Adrian, |
|
@ralf-krause: the situation is not the same, because at this time we didn't thought to add a root CA to the browser. |
|
Maybe MoodleBox should have this HTTPS as experimental option? Per default is HTTP and HTTPS is for advanced users who are aware where are the limits. It will be hard with a not official certificate to satisfy all needs. Do you know ngrok @martignoni? But for a static domain it's a paid subscription... 😏 |
I worked a bit on this, and will try to implement it in a next version. However, I'll keep port 80 as default port, so that the UX won't change for most people. |
Note to self: implementation instructionsPreparationsudo -s
mkdir /root/CA
mkdir /etc/nginx/sslCertificate authority# Generate our CA private key.
openssl genrsa -out /root/CA/moodlebox.CA.key 2048
# Generate a CA root certificate.
openssl req -x509 -new -extensions v3_ca -nodes -key /root/CA/moodleboxCA.key -sha256 -days 3652 -out /root/CA/moodleboxCA.pem -subj "/C=CH/O=MoodleBoxCA/CN=net.moodlebox.ca"Create SSL certificate signed with above CA root certificate# Generate our website private key.
openssl genrsa -out /etc/nginx/ssl/moodlebox.key 2048
# Create a CSR.
openssl req -new -key /etc/nginx/ssl/moodlebox.key -out /etc/nginx/ssl/moodlebox.csr -subj "/C=CH/O=MoodleBox/CN=moodlebox.home"
# Create the signed SSL certificate.
openssl x509 -req -in /etc/nginx/ssl/moodlebox.csr -CA /root/CA/moodleboxCA.pem -CAkey /root/CA/moodleboxCA.key -CAcreateserial -out /etc/nginx/ssl/moodlebox.pem -days 3652 -sha256
# Delete CSR.
rm /etc/nginx/ssl/moodlebox.csrConfigure nginxAdd following 3 lines to file /etc/nginx/sites-available/default, just after line listen 443 ssl;
ssl_certificate /etc/nginx/ssl/moodlebox.crt;
ssl_certificate_key /etc/nginx/ssl/moodlebox.key;And reload nginx sudo systemctl reload nginx.serviceNoteThis is a cool documentation: https://gist.github.com/Soarez/9688998 |
- SAN needed for Chrome - See issue #27.
|
Hi @martignoni Cool that you are working on this issue. Thumbs up! 👍 Greets |
|
Documentation published. Closing :-) |



MoodleBox is now http only. Find a way to enable https.
The text was updated successfully, but these errors were encountered: