DAI/USDC/USDT Free Transfer?
DAI/USDC/USDT Free Transfer?
 Learn how to use the latest spy apps to monitor an iPhone remotely! Discover step-by-step instructions on how to spy on an iPhone without them knowing.
Learn how to use the latest spy apps to monitor an iPhone remotely! Discover step-by-step instructions on how to spy on an iPhone without them knowing.
 What do trust & safety leaders expect in 2022 with the rise of blockchain and crypto? Find out why next year is the year for compliance, regtech, trust & safety
What do trust & safety leaders expect in 2022 with the rise of blockchain and crypto? Find out why next year is the year for compliance, regtech, trust & safety
 There are many Hackers in this world who may be currently watching your activities daily and will try to snatch your personal information from you.
There are many Hackers in this world who may be currently watching your activities daily and will try to snatch your personal information from you.
 To take full advantage of the rapidly growing ride-sharing and delivery market, we offer 5 hacks for drivers to maximize their profits by identifying problems.
To take full advantage of the rapidly growing ride-sharing and delivery market, we offer 5 hacks for drivers to maximize their profits by identifying problems.
 This morning I just thinking how to send an empty message on Standuply channel(Slack). Fortunately, I just found an answer at stackexchange, also an article on wikipedia about non-printing character.
This morning I just thinking how to send an empty message on Standuply channel(Slack). Fortunately, I just found an answer at stackexchange, also an article on wikipedia about non-printing character.
 Over the past year, we have seen a massive jump in activity and value for the crypto and decentralized finance (DeFi) spaces.
Over the past year, we have seen a massive jump in activity and value for the crypto and decentralized finance (DeFi) spaces.
 Pokémon Radical Red is one of the best Pokémon ROM hacks available and should be played by any franchise fan.
Pokémon Radical Red is one of the best Pokémon ROM hacks available and should be played by any franchise fan.
 Recently I had the need to change certain classes -from external dependencies- loaded on a Spring Boot application. All this happened in a very restrictive environment, where I was not allowed to use other libraries or tweak the JRE, it was only possible to modify the fat JAR and environment variables or system properties.
Recently I had the need to change certain classes -from external dependencies- loaded on a Spring Boot application. All this happened in a very restrictive environment, where I was not allowed to use other libraries or tweak the JRE, it was only possible to modify the fat JAR and environment variables or system properties.
 This post uses a concrete CTF problem to show you step-by-step how to find and execute a one gadget and eventually spawn a shell.
This post uses a concrete CTF problem to show you step-by-step how to find and execute a one gadget and eventually spawn a shell.
 Lear how you can speed up the process of product creation and how you can create an admin panel in the shortest possible time with Airtable
Lear how you can speed up the process of product creation and how you can create an admin panel in the shortest possible time with Airtable
 The online gambling industry is a lucrative target for various fraudsters and hackers. Mainly, it’s because casino websites are a gateway to the customers’ credit
cards, bank accounts, and other sensitive data. By hacking an online casino, malicious actors can easily get access to the financial and/or personal info of clients. However, there are more reasons for the growing number of gambling-related hacks. What are they? Let’s figure out.
The online gambling industry is a lucrative target for various fraudsters and hackers. Mainly, it’s because casino websites are a gateway to the customers’ credit
cards, bank accounts, and other sensitive data. By hacking an online casino, malicious actors can easily get access to the financial and/or personal info of clients. However, there are more reasons for the growing number of gambling-related hacks. What are they? Let’s figure out.
 Let’s take a look at some of the best coding hacks to remember in the new year.
Let’s take a look at some of the best coding hacks to remember in the new year.
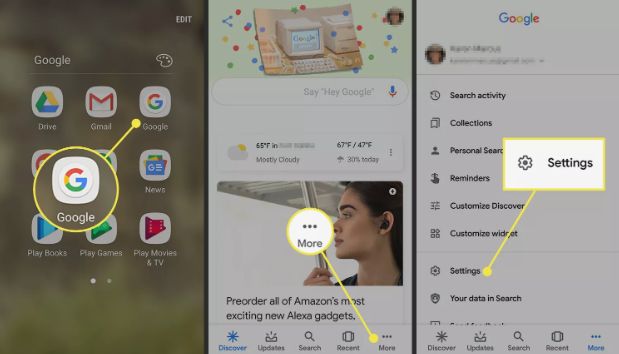
 Give your eyes a rest and permit your Android gadget to peruse your writings to you. This element (just as sending writings utilizing your voice) is accessible through Google and the free applications that you can download from Google Play. Here are the manners in which you can make your Android read instant messages.
Give your eyes a rest and permit your Android gadget to peruse your writings to you. This element (just as sending writings utilizing your voice) is accessible through Google and the free applications that you can download from Google Play. Here are the manners in which you can make your Android read instant messages.
 Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
Ever since it emerged in mid-2020, DeFi has been a major trend in the cryptocurrency industry, which was (and still is) quite understandable. It brought a way to make money passively, it enabled loans that you can get in exchange for providing collateral, but most importantly, it allowed you to use your existing money to make more money, without the risks that accompany crypto trading.
 In 2018, Nintendo filed a lawsuit against a California man accused of selling pirated Nintendo games, modding devices, and modding services.
In 2018, Nintendo filed a lawsuit against a California man accused of selling pirated Nintendo games, modding devices, and modding services.
 Price discrimination have been around for years. It is seen as a benefit for both companies and buyers, but there is a line that price discrimination can cross to become illegal and harmful for our digital life.
Price discrimination have been around for years. It is seen as a benefit for both companies and buyers, but there is a line that price discrimination can cross to become illegal and harmful for our digital life.
 The flow state: A state of hyperfocus where you perform at an amazing level. Read about our different approaches to getting into this wellspring of focus.
The flow state: A state of hyperfocus where you perform at an amazing level. Read about our different approaches to getting into this wellspring of focus.
 Over the last few days, website owners, specifically those hosting on GoDaddy, have been experiencing strange redirects to various websites.
Over the last few days, website owners, specifically those hosting on GoDaddy, have been experiencing strange redirects to various websites.
 In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
In addition to sharing personal data of essential people in Indonesia, Bjorka also studied death cases such as Munir and Brigadier J. Who was Bjorka?
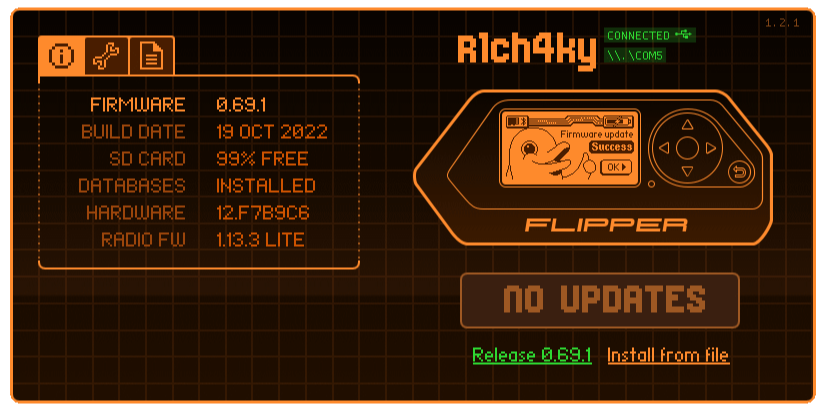
 It is theoretically possible to use these Flipper Zero hacks for nefarious purposes, including the tricks in this article. But you know…don’t do that.
It is theoretically possible to use these Flipper Zero hacks for nefarious purposes, including the tricks in this article. But you know…don’t do that.
 This post shows you how to exploit a v8 heap overflow bug - *CTF 2019 oob-v8. It presents two novel points: similar exploitation, primitive escalation.
This post shows you how to exploit a v8 heap overflow bug - *CTF 2019 oob-v8. It presents two novel points: similar exploitation, primitive escalation.
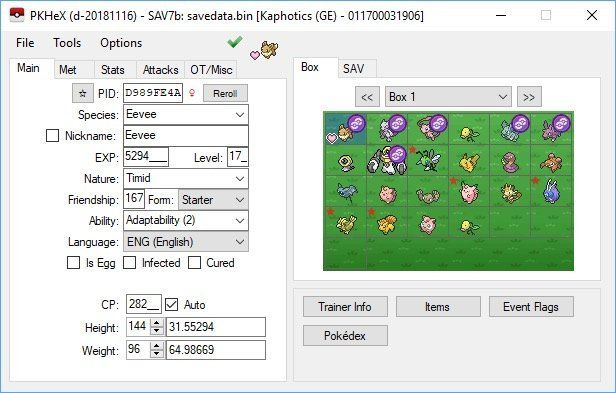
 Here's how to use PKHex on the Nintendo Switch to edit what Pokemon are in your party.
Here's how to use PKHex on the Nintendo Switch to edit what Pokemon are in your party.
 With the COVID-19 pandemic, more and more employees have had to work from home, creating new cybersecurity challenges for businesses. Some workers will have to relearn everything about cybersecurity because they must keep their work documents and email secure even on their home network.
With the COVID-19 pandemic, more and more employees have had to work from home, creating new cybersecurity challenges for businesses. Some workers will have to relearn everything about cybersecurity because they must keep their work documents and email secure even on their home network.
 Unlimited cloud storage for storing photos, videos, and files using the Telegram App. The best alternative to Google Drive and Google Photos.
Unlimited cloud storage for storing photos, videos, and files using the Telegram App. The best alternative to Google Drive and Google Photos.
 If you are here, you have probably heard about how to hire a hacker on the dark or deep web. Using regular web browsers, we can only have access to four percent of the net. The other 96% must be accessed through a unique browser, Tor.
If you are here, you have probably heard about how to hire a hacker on the dark or deep web. Using regular web browsers, we can only have access to four percent of the net. The other 96% must be accessed through a unique browser, Tor.
 This interview with blockchain cybersecurity expert Yotam Dar discusses blockchain cybersecurity and blockchain hacks in detail and with case studies.
This interview with blockchain cybersecurity expert Yotam Dar discusses blockchain cybersecurity and blockchain hacks in detail and with case studies.
 Are you a Linux admin or want to? this is a list of Linux tricks that you might know.
Are you a Linux admin or want to? this is a list of Linux tricks that you might know.
 In this article, I discuss how you can convert one android phone into a fully working Kali Linux hacking machine.
In this article, I discuss how you can convert one android phone into a fully working Kali Linux hacking machine.
 Decentralized finance (DeFi) was created back in 2015, when the pioneer application, MakerDAO, allowed any crypto holders to take out loans in the DAI stablecoin. Years of steady growth followed and a palpable buzz around DeFi started to emerge in the crypto community, leading to the breakout year that was 2020.
Decentralized finance (DeFi) was created back in 2015, when the pioneer application, MakerDAO, allowed any crypto holders to take out loans in the DAI stablecoin. Years of steady growth followed and a palpable buzz around DeFi started to emerge in the crypto community, leading to the breakout year that was 2020.
 When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
When it comes to cyberattacks, everybody is at risk, whether it be big corporations, government bodies, small businesses, or private individuals.
 2021 was marked by multiple DeFi frauds, with rug-pulls and exit scams being among the most popular.
2021 was marked by multiple DeFi frauds, with rug-pulls and exit scams being among the most popular.
 You can Hack WhatsApp chats by syncing the web version of the app, exporting chat logs, using POCWAPP, WhatsAPP Scan Pro, spoofing, and spy apps.
You can Hack WhatsApp chats by syncing the web version of the app, exporting chat logs, using POCWAPP, WhatsAPP Scan Pro, spoofing, and spy apps.