The Solarwinds Sunburst exploit was a devastating cyber attack that opened up thousands of companies to hackers. There's a lot to learn and understand about it.
The Solarwinds Sunburst exploit was a devastating cyber attack that opened up thousands of companies to hackers. There's a lot to learn and understand about it.
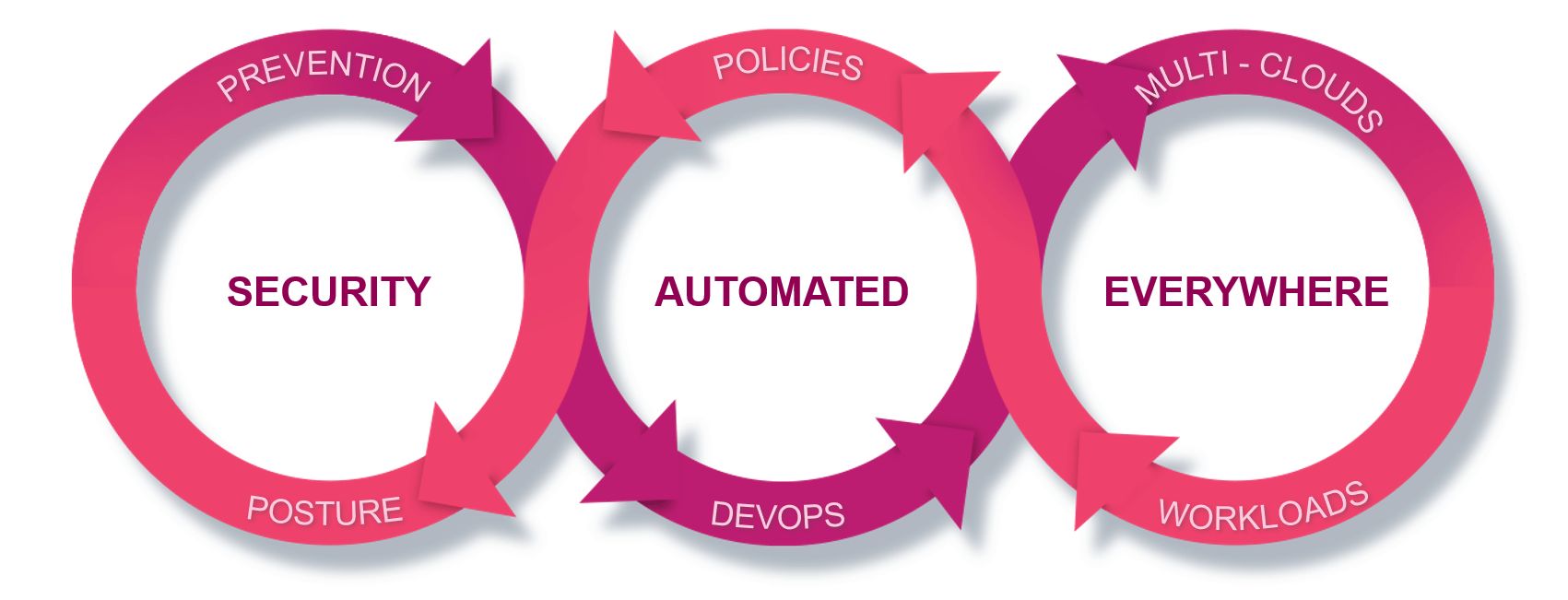
 A unified approach to clould data security has significant advantages to cybersecurity relative to conventional methods of cybersecurity and may be helpful.
A unified approach to clould data security has significant advantages to cybersecurity relative to conventional methods of cybersecurity and may be helpful.
 Threat actors are becoming more and more sophisticated in their ability to exploit vulnerabilities, breach organizations’ IT infrastructures, and hack into data
Threat actors are becoming more and more sophisticated in their ability to exploit vulnerabilities, breach organizations’ IT infrastructures, and hack into data
 To help security professionals assess their options, we’ve listed five guiding principles for choosing optimal endpoint security solution in our previous blog.
To help security professionals assess their options, we’ve listed five guiding principles for choosing optimal endpoint security solution in our previous blog.
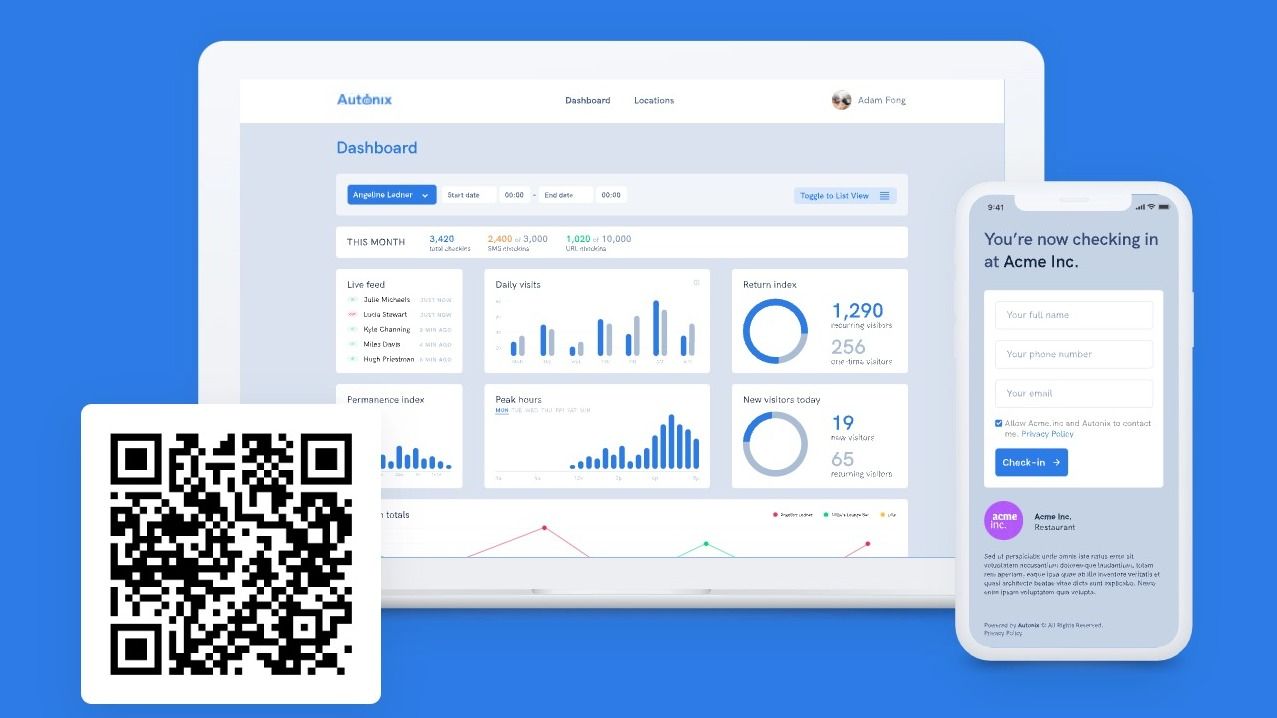
 Unlock the potential of every QR Code! Autonix trackable Link and QR Code Generator lets businesses collect and analyze visitor data for informed decisions.
Unlock the potential of every QR Code! Autonix trackable Link and QR Code Generator lets businesses collect and analyze visitor data for informed decisions.
 A misconception of users had led to over five million records containing personal identifying information to be left on an AWS service, a serious leak.
A misconception of users had led to over five million records containing personal identifying information to be left on an AWS service, a serious leak.
 Ransomware attacks have affected organisations from missile developers to Manchester United. Protecting yourself from them is an important part of security
Ransomware attacks have affected organisations from missile developers to Manchester United. Protecting yourself from them is an important part of security
 Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
Emotet, which was once a Banking Trojan and became a full-blown botnet was the most successful and prevalent malware of 2020 by a long way.
 The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
The Uyghurs, an ethnic minority in China have been targeted by fake human rights documents and websites intended to take advantage of their persecution in China
 With Ransomware attacks increasing rapidly, it ahs become more important for companies to ensure that their network infrastructure is protected from attacks.
With Ransomware attacks increasing rapidly, it ahs become more important for companies to ensure that their network infrastructure is protected from attacks.
 Web Application Firewalls have been a key part of cybersecurity that are facing obsolencence thanks to the significant labour costs associated with WAFs.
Web Application Firewalls have been a key part of cybersecurity that are facing obsolencence thanks to the significant labour costs associated with WAFs.
 Ransomware is becoming more common and with it comes new threats. Triple Extortion Ransomware is a new form of attack that threatens companies across the world.
Ransomware is becoming more common and with it comes new threats. Triple Extortion Ransomware is a new form of attack that threatens companies across the world.
 Remote working and developer infrastructure in the cloud have both served to change the way developer operations work and have new cybersecurity requirements.
Remote working and developer infrastructure in the cloud have both served to change the way developer operations work and have new cybersecurity requirements.
 With Cybersecurity constantly evolving, each month has its own malware that poses the greatest threat. These are the malware threats that were most concerning.
With Cybersecurity constantly evolving, each month has its own malware that poses the greatest threat. These are the malware threats that were most concerning.
 When it comes to security in the cloud, companies face constant, daily threats. This situation has only been exacerbated by the COVID-19 pandemic.
When it comes to security in the cloud, companies face constant, daily threats. This situation has only been exacerbated by the COVID-19 pandemic.
 Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
Multi-cloud gives you much more flexibility because it allows you to find the perfect solution for each of your business requirements.
 Android Malware has started spreading by creating auto-replies to messages in WhatsApp. It's hidden cleverly in dubious apps that are surprisingly good.
Android Malware has started spreading by creating auto-replies to messages in WhatsApp. It's hidden cleverly in dubious apps that are surprisingly good.
 Cyber-warfare and espionage have long been common weapons in the arsenal of governments, armies, and intelligence agencies around the world.
Cyber-warfare and espionage have long been common weapons in the arsenal of governments, armies, and intelligence agencies around the world.
 The AWS Marketplace is a vast and complicated online storefront that has plenty of choice for you to augment your business. Here is a basic explainer.
The AWS Marketplace is a vast and complicated online storefront that has plenty of choice for you to augment your business. Here is a basic explainer.
 Even the greatest cybersecurity arrangements can be vunerable to simple mistakes such as a tiny setting being misconfigured, compromising the entire system.
Even the greatest cybersecurity arrangements can be vunerable to simple mistakes such as a tiny setting being misconfigured, compromising the entire system.
 So what is Infrastructure-as-Code (IaC) anyway? IaC is a process that automates the provisioning and management of cloud resources.
So what is Infrastructure-as-Code (IaC) anyway? IaC is a process that automates the provisioning and management of cloud resources.
 The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
The CDC (The Centers for Disease Control and Prevention) classified “shopping at crowded stores just before, on or after Thanksgiving” on its list
 Mobile App Development is a hugely useful tool but it does come with significant security risks, as the Checkpoint found out when researching threats.
Mobile App Development is a hugely useful tool but it does come with significant security risks, as the Checkpoint found out when researching threats.
 A Chinese threat group managed to hack into a Southeast Asian government by using disguised files to take advantage of a backdoor in the computer infrastructure
A Chinese threat group managed to hack into a Southeast Asian government by using disguised files to take advantage of a backdoor in the computer infrastructure
 On November 16, 2020 Check Point Research (CPR) uncovered chained vulnerabilities that together can be used to take over an account and control Atlassian apps.
On November 16, 2020 Check Point Research (CPR) uncovered chained vulnerabilities that together can be used to take over an account and control Atlassian apps.
 Check Point Research did an investigation about the fake COVID-19 tests out in the Darknet and hacking forums that were sold to help people falsify their status
Check Point Research did an investigation about the fake COVID-19 tests out in the Darknet and hacking forums that were sold to help people falsify their status
 The Sunburst attacks relied on the Cloud model to work successfully. Experts believe that Dark Halo, the group responsible, used priviledges to do it.
The Sunburst attacks relied on the Cloud model to work successfully. Experts believe that Dark Halo, the group responsible, used priviledges to do it.
 Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
Check Point Software’s Incident Response Team's guide for enterprises on how to prevent and deal with ransomware attacks.
 With the revelation of four zero-day vulnerabilities currently affecting Microsoft Exchange Server, Check Point Research (CPR) shares its findings on exploits
With the revelation of four zero-day vulnerabilities currently affecting Microsoft Exchange Server, Check Point Research (CPR) shares its findings on exploits
 What is the most involved attack flow yet? We will break down all of the steps a threat actor took to successfully exfiltrate data out of an AWS account.
What is the most involved attack flow yet? We will break down all of the steps a threat actor took to successfully exfiltrate data out of an AWS account.
 Intuitively, some people believe that “cloud” storage means your data is being held in the air somehow, but this isn’t really the case.
Intuitively, some people believe that “cloud” storage means your data is being held in the air somehow, but this isn’t really the case.
 In this post, we will cover five key areas that are very relevant to most financial services businesses—five topics an organization must “get right”.
In this post, we will cover five key areas that are very relevant to most financial services businesses—five topics an organization must “get right”.
 VPNs might be the most common way of creating network security for remote work but Zero Trust Network Access might be a better designed alternative for you.
VPNs might be the most common way of creating network security for remote work but Zero Trust Network Access might be a better designed alternative for you.
 Ckeckout some significant enhancements to CloudGuard’s integration with new and existing Google Cloud features to benefit from it.
Ckeckout some significant enhancements to CloudGuard’s integration with new and existing Google Cloud features to benefit from it.
 The Snapdragon System on a Chip is a convenient solution for many phone manufacturers when it comes to hardware. However, it comes with its own security risks.
The Snapdragon System on a Chip is a convenient solution for many phone manufacturers when it comes to hardware. However, it comes with its own security risks.
 Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
Attackers initiated a phishing campaign with emails that masqueraded as Xerox scan notifications, prompting users to open a malicious HTML attachment.
 Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
Security for the “Internet of Things” (or IoT) is still relatively new to a majority of organizations.
 Microsoft Office is one of the most commonly used forms of productivity software. The Checkopint has tried to fuzz one part of Office to see how it affects it.
Microsoft Office is one of the most commonly used forms of productivity software. The Checkopint has tried to fuzz one part of Office to see how it affects it.
 In the past month, we noticed that a dark net search for Covid-19 vaccines returns multiple pages of results, amounting to hundreds of advertisements.
In the past month, we noticed that a dark net search for Covid-19 vaccines returns multiple pages of results, amounting to hundreds of advertisements.
 Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
Now more than ever, we rely on our smartphones to keep in touch with our work, our families and the world around us. There are over 3.5 billion smartphone users
 The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
The attack combines a one-on-one phone call with credible-looking phishing sites where the user is required to fill in their credentials and their MFA codes.
 As with any security incident, security practitioners would initially focus on identifying signs of potential Sunburst activities in their networks and systems.
As with any security incident, security practitioners would initially focus on identifying signs of potential Sunburst activities in their networks and systems.
 Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
Cyber weapons are digital and volatile by nature. Stealing them and transferring from one continent to another, can be as simple as sending an email.
 Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers
Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers
 Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
Check Point Research encountered several attacks that exploited multiple vulnerabilities, including some that were only recently published, to inject OS command
 In this research, we were able to find four new vulnerabilities in Valve’s game networking library by taking advantage of two of C++’s language quirks.
In this research, we were able to find four new vulnerabilities in Valve’s game networking library by taking advantage of two of C++’s language quirks.
 When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.
When analyzing a complicated attack against one of our customers, we noticed a very small 64-bit executable that was executed by the malware.