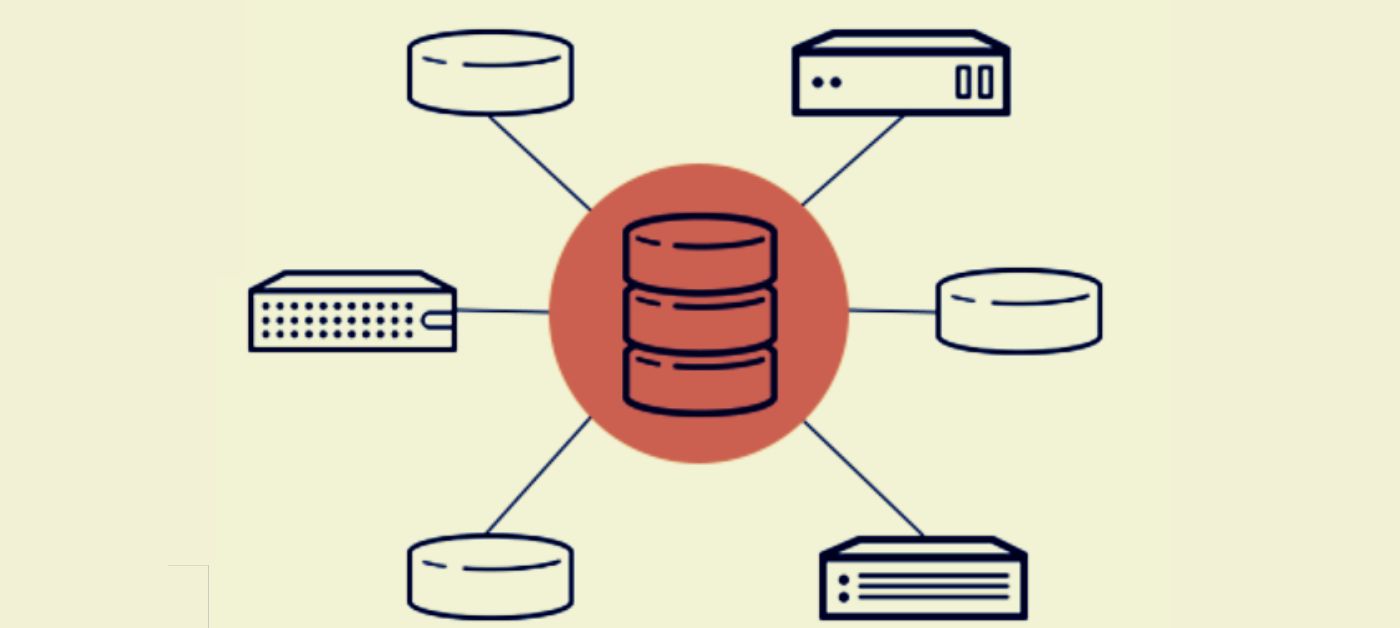
Microservices have helped the backend world to divide backends into smaller, more manageable, and more efficient pieces.
Microservices have helped the backend world to divide backends into smaller, more manageable, and more efficient pieces.
 The successful implementation of digital transformation in the enterprise depends largely on the willingness of the corporate culture to change.
The successful implementation of digital transformation in the enterprise depends largely on the willingness of the corporate culture to change.
 Replicating human interaction and behavior is what artificial intelligence has always been about. In recent times, the peak of technology has well and truly surpassed what was initially thought possible, with countless examples of the prolific nature of AI and other technologies solving problems around the world.
Replicating human interaction and behavior is what artificial intelligence has always been about. In recent times, the peak of technology has well and truly surpassed what was initially thought possible, with countless examples of the prolific nature of AI and other technologies solving problems around the world.
 Learn how B2B and SaaS product managers solve business users problems by building features for enterprise solutions
Learn how B2B and SaaS product managers solve business users problems by building features for enterprise solutions
 A single source of truth (SSOT) enables that synchronization. A company with SSOT relies on one and only one point of reference for the latest, aggregated info.
A single source of truth (SSOT) enables that synchronization. A company with SSOT relies on one and only one point of reference for the latest, aggregated info.
 Contract management software for small businesses optimizes negotiations so you can spend more time expanding your brand.
Contract management software for small businesses optimizes negotiations so you can spend more time expanding your brand.
 The .NET Core platform makes it possible for businesses to develop applications for just about any platform—from Windows, macOS, Linux, and even mobile operating systems. This isn’t just a time saver, but a means to cut back on your budget. You will be able to develop across all platforms, and you won't have to hire developers for each ecosystem. Instead, you can hire one developer or a team of .NET developers to make it all happen.
The .NET Core platform makes it possible for businesses to develop applications for just about any platform—from Windows, macOS, Linux, and even mobile operating systems. This isn’t just a time saver, but a means to cut back on your budget. You will be able to develop across all platforms, and you won't have to hire developers for each ecosystem. Instead, you can hire one developer or a team of .NET developers to make it all happen.
 Built for the creator economy. Empowering small businesses. Expanding spheres of influence. Erik Norgaard shares the origin story of Hollyfy.
Built for the creator economy. Empowering small businesses. Expanding spheres of influence. Erik Norgaard shares the origin story of Hollyfy.
 With over 70% of companies undergoing complete digitization, it might be your company’s chance to reap the benefits of using sales ERP software.
With over 70% of companies undergoing complete digitization, it might be your company’s chance to reap the benefits of using sales ERP software.
 In this article, we'll discuss the ways by which customers can be sure that their information is being kept safe, and they can track their purchases.
In this article, we'll discuss the ways by which customers can be sure that their information is being kept safe, and they can track their purchases.

 New enterprise-ready blockchain revolutionising document management space. DoxyChain brings new online contracting standards to European Union.
New enterprise-ready blockchain revolutionising document management space. DoxyChain brings new online contracting standards to European Union.
 This is making it increasingly important for individuals to develop these skills if they want to remain competitive in the job market.
This is making it increasingly important for individuals to develop these skills if they want to remain competitive in the job market.
 With thousands of security vulnerabilities reported each month in products ranging from hardware devices to firmware to popular software apps, how does one prioritise what needs the most attention? From a business and project management perspective, it makes sense to, first and foremost, allocate engineering and/or risk assessment resources to the most severe vulnerabilities that need immediate patching.
With thousands of security vulnerabilities reported each month in products ranging from hardware devices to firmware to popular software apps, how does one prioritise what needs the most attention? From a business and project management perspective, it makes sense to, first and foremost, allocate engineering and/or risk assessment resources to the most severe vulnerabilities that need immediate patching.
 Serverless in enterprise success stories. Why should enterprise move to serverless? What's important to enterprise in serverless.
Serverless in enterprise success stories. Why should enterprise move to serverless? What's important to enterprise in serverless.
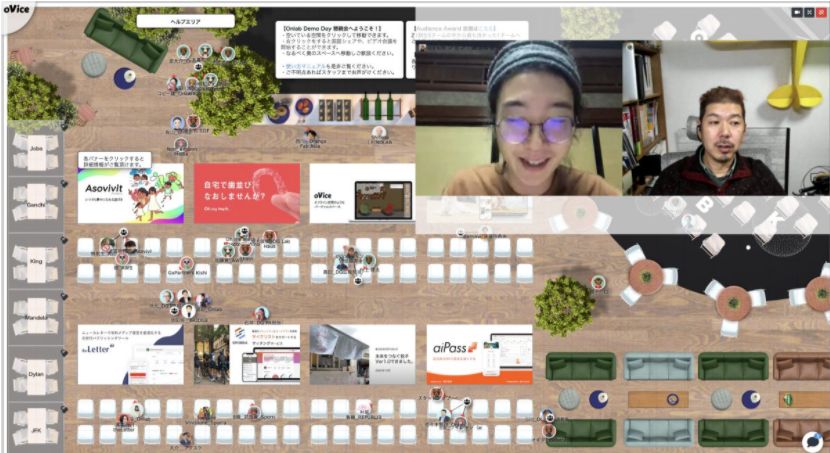
 At oVice, you can virtually walk by moving your avatar and easily join in and out of conversations by bringing your avatar either closer or away from the other.
At oVice, you can virtually walk by moving your avatar and easily join in and out of conversations by bringing your avatar either closer or away from the other.
 This article covers the top eight factors you should consider when choosing a cloud enterprise technology.
This article covers the top eight factors you should consider when choosing a cloud enterprise technology.
 It’s pretty amazing how many tech products expand globally. Reaching new markets and looking for new business opportunities. Even despite today’s economic challenges. What’s much less pleasurable to observe is the amount of effort localization can take if done without proper technology.
It’s pretty amazing how many tech products expand globally. Reaching new markets and looking for new business opportunities. Even despite today’s economic challenges. What’s much less pleasurable to observe is the amount of effort localization can take if done without proper technology.
 Enterprise players across all industries are eager for optimization and improvement of their business processes: administration, customer service, marketing, sales, recruiting, and others. Today AI-driven software can cover the most common Enterprise needs like data security, data processing, resource optimization, and brand awareness. Forrester has reported that AI is also able to improve customer service and quality of existing products, increase revenue streams, and customer lifetime value.
Enterprise players across all industries are eager for optimization and improvement of their business processes: administration, customer service, marketing, sales, recruiting, and others. Today AI-driven software can cover the most common Enterprise needs like data security, data processing, resource optimization, and brand awareness. Forrester has reported that AI is also able to improve customer service and quality of existing products, increase revenue streams, and customer lifetime value.
 Over the last decade, AI has evolved into an all-purpose term for any accomplishments of computer algorithms that formerly required human reasoning and thought
Over the last decade, AI has evolved into an all-purpose term for any accomplishments of computer algorithms that formerly required human reasoning and thought
 What is the matter with Forms’ support? Why migrate to APEX? What are the benefits? In this article, I’ll provide you with answers to these questions.
What is the matter with Forms’ support? Why migrate to APEX? What are the benefits? In this article, I’ll provide you with answers to these questions.
 Businesses have been overlooking employee wellness for a long time. As organizations started re-opening, they must have actionable employee well-being.
Businesses have been overlooking employee wellness for a long time. As organizations started re-opening, they must have actionable employee well-being.
 The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
The notion of “Zero Trust” has been around since the 90s. But, the Zero Trust security model was first coined by John Kindervag to describe stricter access control management and cybersecurity programs, in 2010. Meaning that infinite trust is diminished from all computing infrastructure, and Zero Trust is grounded on the idea “trust none, verify all”.
 The new Securitize tokenized fund (the “Fund”) marks the first time exposure to one of KKR’s alternative investment strategies.
The new Securitize tokenized fund (the “Fund”) marks the first time exposure to one of KKR’s alternative investment strategies.
 Comprehensive data visibility is still a big challenge in enterprise resource planning.
Comprehensive data visibility is still a big challenge in enterprise resource planning.
 Bitcoin was born as a solution to the damage created by money printing. With the decentralised nature of cryptocurrencies, we can solve this problem.
Bitcoin was born as a solution to the damage created by money printing. With the decentralised nature of cryptocurrencies, we can solve this problem.
 This post has been authored by Aakrit Vaish, Co-Founder & CEO of Haptik
This post has been authored by Aakrit Vaish, Co-Founder & CEO of Haptik
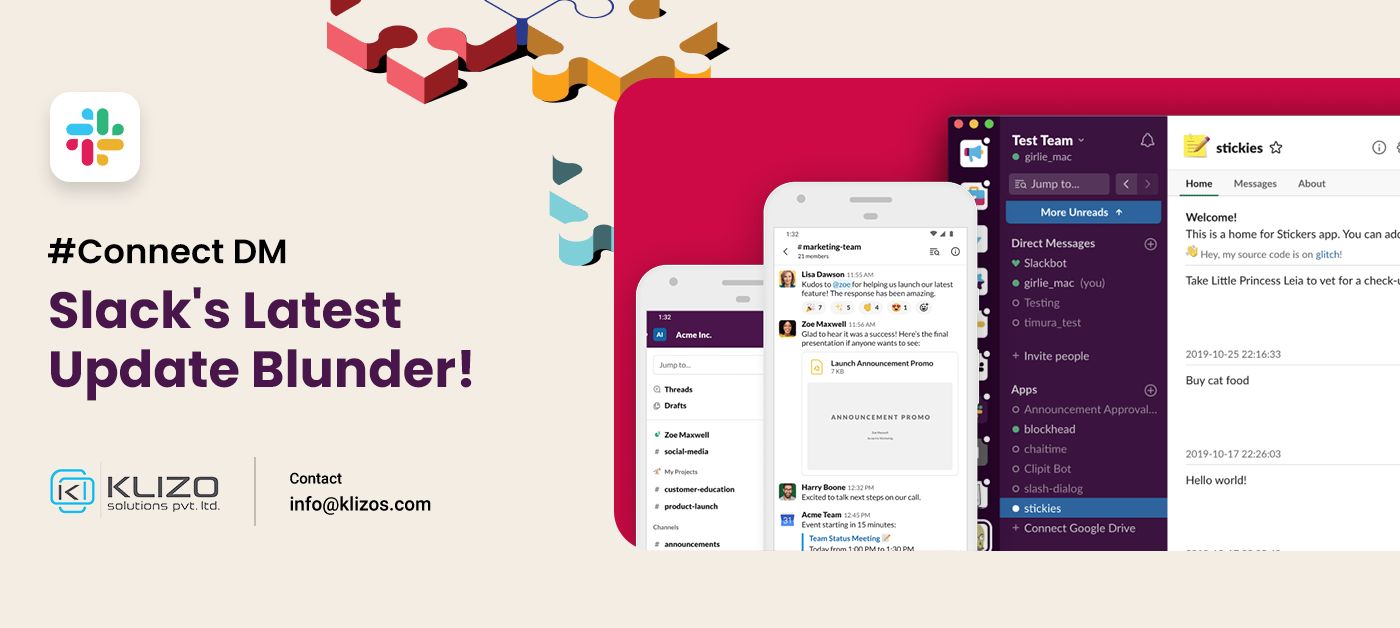
 Slack recently rolled out its "Connect DM” feature that turned out to be a blunder. Know more about it here.
Slack recently rolled out its "Connect DM” feature that turned out to be a blunder. Know more about it here.
 A look at why enterprises are slow in moving to Kubernetes.
A look at why enterprises are slow in moving to Kubernetes.
 These days, a lot of businesses are concentrating on integrating a cloud-based system into their IT infrastructure because they are more dependable, and strong.
These days, a lot of businesses are concentrating on integrating a cloud-based system into their IT infrastructure because they are more dependable, and strong.
 Learn how corporate YouTube automates video content management helping you meet end-to-end enterprise video needs
Learn how corporate YouTube automates video content management helping you meet end-to-end enterprise video needs
 In today’s digital world, data is constantly being generated, evaluated, and updated. It also plays an important role in the work of software engineers by providing accurate, actionable feedback that helps engineers understand where and how to make improvements to a product or process.
In today’s digital world, data is constantly being generated, evaluated, and updated. It also plays an important role in the work of software engineers by providing accurate, actionable feedback that helps engineers understand where and how to make improvements to a product or process.
 Alexei Dulub, CEO & Founder of PixelPlex, discusses consulting & custom development, power of value-driven teams, blockchain's prospects, and unattainable goals
Alexei Dulub, CEO & Founder of PixelPlex, discusses consulting & custom development, power of value-driven teams, blockchain's prospects, and unattainable goals
 This blog will discuss DC/OS and Kubernetes and what challenges you might face when migrating between these container platforms.
This blog will discuss DC/OS and Kubernetes and what challenges you might face when migrating between these container platforms.
 While consumer products get all the hype, B2B products are a quiet gem
While consumer products get all the hype, B2B products are a quiet gem
 The barriers to digital transformation, personal experience of its implementation, and the lessons learned during the evolution of a composable enterprise.
The barriers to digital transformation, personal experience of its implementation, and the lessons learned during the evolution of a composable enterprise.
 AI is everywhere and we should start to intentionally recruit more diverse teams to design and build it.
AI is everywhere and we should start to intentionally recruit more diverse teams to design and build it.
 Photo Credit, Jeremy Weate
Photo Credit, Jeremy Weate
 Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
Digital identities are of crucial importance for cybersecurity of modern enterprises. Let's find out what changes can be expected in the domain of web security.
 As an eternal optimist, I've always wanted to live through an economic recession as a working professional and finally, the time might be here.
As an eternal optimist, I've always wanted to live through an economic recession as a working professional and finally, the time might be here.
 It’s clear to everyone that we’re living in a digital age. In a time when people expect to run their lives through their smartphones, competitive enterprises have no choice but to adopt digital tools.
It’s clear to everyone that we’re living in a digital age. In a time when people expect to run their lives through their smartphones, competitive enterprises have no choice but to adopt digital tools.
 Wondering why your business needs a dedicated ERP system? Read to explore some important use cases of ERP for business growth and profitability.
Wondering why your business needs a dedicated ERP system? Read to explore some important use cases of ERP for business growth and profitability.
 Let us go through 5 proven use cases of intelligent document processing for enterprises.
Let us go through 5 proven use cases of intelligent document processing for enterprises.
 Here's a step-by-step guide for enterprise mobile app development. It is a good read for enterprise executives who don't know where to start.
Here's a step-by-step guide for enterprise mobile app development. It is a good read for enterprise executives who don't know where to start.
 Mobile devices have redefined the way we interact with digital technology, and enterprise mobile applications are probably the most interesting example of this shift. While they hold considerable potential for improving business operations, you’ll be right to wonder whether they can really fulfill all the trendy promises seen in the media. Below is a detailed analysis of what these apps can really do and how to harness their potential while avoiding the risks.
Mobile devices have redefined the way we interact with digital technology, and enterprise mobile applications are probably the most interesting example of this shift. While they hold considerable potential for improving business operations, you’ll be right to wonder whether they can really fulfill all the trendy promises seen in the media. Below is a detailed analysis of what these apps can really do and how to harness their potential while avoiding the risks.
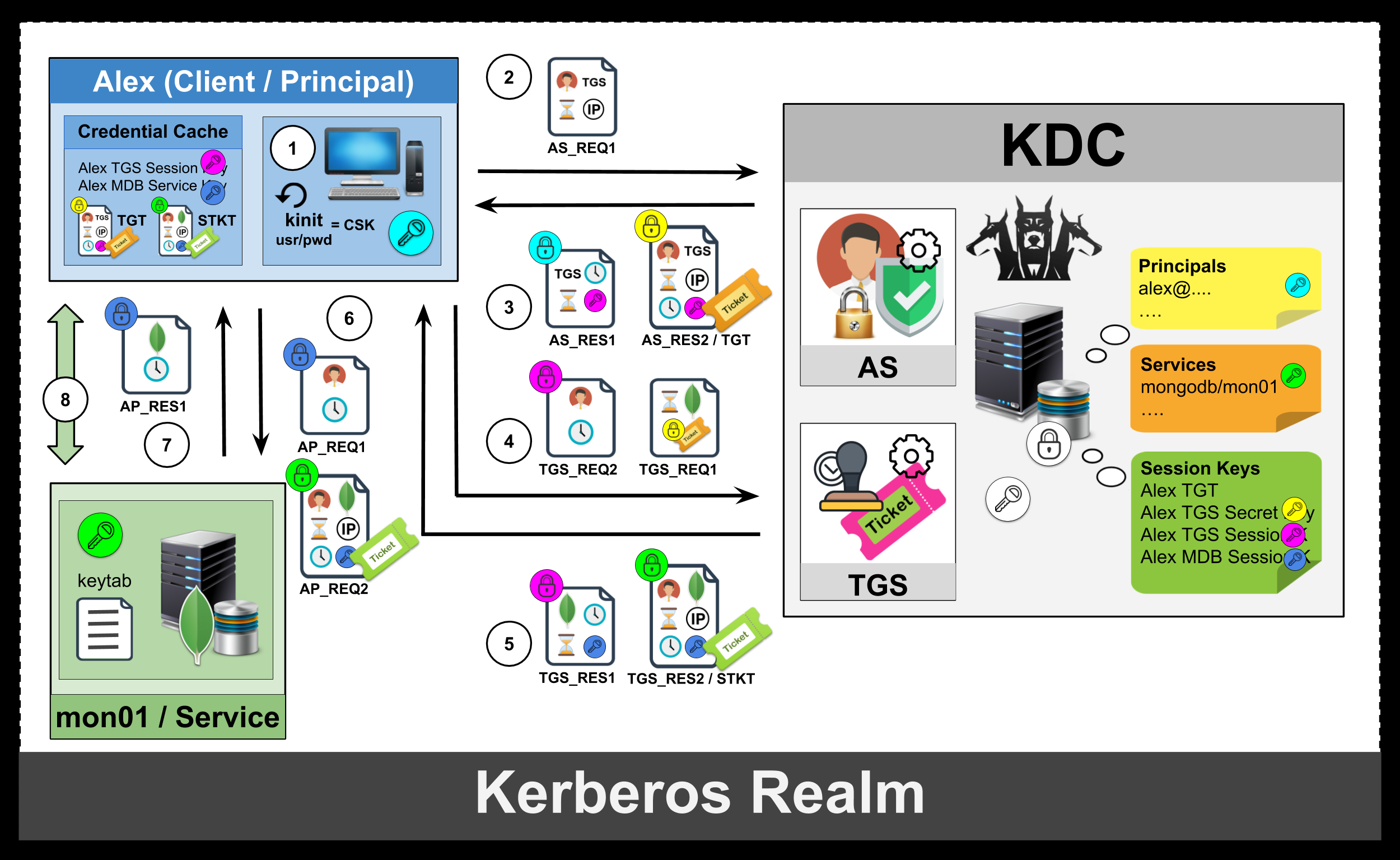
 The MongoDB database administrators in a large enterprise may need to configure MongoDB to support Kerberos Authentication. The configuration of MongoDB with Kerberos authentication is very simple, provided you have some Kerberos knowledge. The MongoDB documentation article, Configure MongoDB with Kerberos Authentication on Linux, is pretty extensive on this topic. However, the article states — “Setting up and configuring a Kerberos deployment is beyond the scope of this document”, resulting in some of the starters/enthusiasts with limited knowledge in Kerberos not proceed any further. This article is geared more towards bridging that gap and to help you understand
The MongoDB database administrators in a large enterprise may need to configure MongoDB to support Kerberos Authentication. The configuration of MongoDB with Kerberos authentication is very simple, provided you have some Kerberos knowledge. The MongoDB documentation article, Configure MongoDB with Kerberos Authentication on Linux, is pretty extensive on this topic. However, the article states — “Setting up and configuring a Kerberos deployment is beyond the scope of this document”, resulting in some of the starters/enthusiasts with limited knowledge in Kerberos not proceed any further. This article is geared more towards bridging that gap and to help you understand
 This blog examines the top Software-Defined-Storage (SDS) market players for 2022 and highlights the importance of each one as an enterprise solution.
This blog examines the top Software-Defined-Storage (SDS) market players for 2022 and highlights the importance of each one as an enterprise solution.

 Replicating human interaction and behavior is what artificial intelligence has always been about. In recent times, the peak of technology has well and truly surpassed what was initially thought possible, with countless examples of the prolific nature of AI and other technologies solving problems around the world.
Replicating human interaction and behavior is what artificial intelligence has always been about. In recent times, the peak of technology has well and truly surpassed what was initially thought possible, with countless examples of the prolific nature of AI and other technologies solving problems around the world.