-
Notifications
You must be signed in to change notification settings - Fork 210
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Config file printed out to the standard output #294
Comments
|
This is bizarre. No, this behavior is not desired. Note that the code you are pointing to will only be executed if you are using a very alpha feature, where instead of a single configuration file, you have a set of configuration files in a directory. Is this how you are mounting your secret? |
|
Hi there, Sorry for the delay, I had to rebuild the whole cluster (hardware included) and it took a while. So, this is how I am deploying glauth: # kutomization.yaml
---
apiVersion: kustomize.config.k8s.io/v1beta1
kind: Kustomization
helmCharts:
- name: app-template
repo: https://bjw-s.github.io/helm-charts/
version: 1.1.3
releaseName: &releaseName glauth
namespace: &releaseNamespace authentication
valuesFile: values.yaml
commonAnnotations:
meta.helm.sh/release-name: *releaseName
meta.helm.sh/release-namespace: *releaseNamespace
commonLabels:
app.kubernetes.io/managed-by: Helm# vaules.yaml
controller:
replicas: 1
strategy: RollingUpdate
image:
repository: docker.io/glauth/glauth
tag: v2.2.0-RC1
command: ["/app/glauth", "-c", "/vault/secrets/glauth"]
serviceAccount:
create: true
service:
main:
ports:
http:
port: 5555
ldap:
enabled: true
port: 389
serviceMonitor:
main:
enabled: false
podSecurityContext:
runAsUser: 1000
runAsGroup: 1000
fsGroup: 1000
fsGroupChangePolicy: "OnRootMismatch"
topologySpreadConstraints:
- maxSkew: 1
topologyKey: kubernetes.io/hostname
whenUnsatisfiable: DoNotSchedule
labelSelector:
matchLabels:
app.kubernetes.io/name: glauth
resources:
requests:
cpu: 5m
memory: 10Mi
limits:
memory: 50MiOn top of that, I am applying the Vault annotations: # vault-annotations.yaml
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: glauth
spec:
template:
metadata:
annotations:
vault.hashicorp.com/agent-inject: "true"
vault.hashicorp.com/tls-skip-verify: "true"
vault.hashicorp.com/role: "glauth"
vault.hashicorp.com/agent-inject-secret-config: "secret/glauth"
vault.hashicorp.com/agent-inject-template-config: |
{{- with secret "secret/glauth" -}}
{{ .Data.data.server | writeToFile "/vault/secrets/glauth/server.toml" "" "" "0644" }}
{{ .Data.data.groups | writeToFile "/vault/secrets/glauth/groups.toml" "" "" "0644" }}
{{ .Data.data.users | writeToFile "/vault/secrets/glauth/users.toml" "" "" "0644" }}
{{- end -}}Three files are created under the
|
|
I see. Yes, an interesting side effect of using what happens to be an alpha quality feature. |
|
I could also generate just one file. But let me know if you need some hands to finish this feature! |
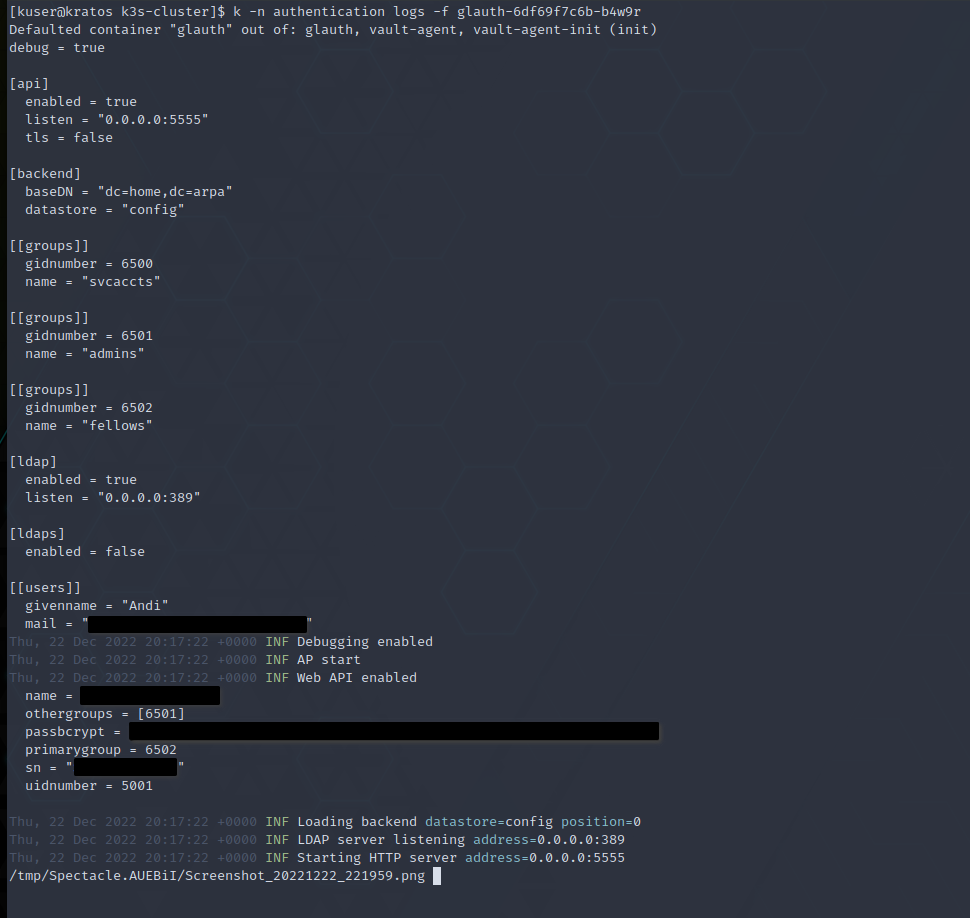
Hi,
I am testing Glauth in my home lab. I am deploying it in a k3s cluster. I would like to have the configuration file defined in secrets. To accomplish this, I am injecting the configuration from Vault. But the process is printing the whole config file to the standard output!!
I'm not 100% sure, but I think the culprit is:
glauth/v2/glauth.go
Line 350 in 7da3859
Is this behavior something desired? Isn't it better to put it as a trace/debug log statement so it can be disabled?
The text was updated successfully, but these errors were encountered: