-
Notifications
You must be signed in to change notification settings - Fork 98
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Bypass File Uploading restrictions leads to Command Execution #674
Comments
|
Oh, I see. Which version are you using? This is definitely not the current master from here. |
|
@mahotilo 5.1 like the image bellow i got from latest releases. Theres another version ? more recent ? one more time sorry about my explanation :( |
|
i'll testing on that version too =). One question, this issue was reported before ? at the version 5.1 ? |
|
As far as I remember, this was known to the developers. |
|
I can confirm it works in Versions 5 - 5.1.
If you still manage to get it working with current master (5.2-rc) please report.
It was not reported but there were rumors about sth. like that. Allegedly it is part of an exploit suite that can be bought. However, rather dubious sources IMO. While this is an 'authenticated RCE', which clearly contradicts our security policy, Typesetter is not a community platform and there is no way to register user accounts yourself, which could do such things. So, Typesetter admins are considered trustworthy. Nevertheless it is something that must not happen and Typesetter 5.2 will prevent it AFAIK. |
|
@juek thanks to confirm =) i'm testing on version 5.2 and was fixed. |
|
I just tested on 5.2 as well and could not extract the php file. |
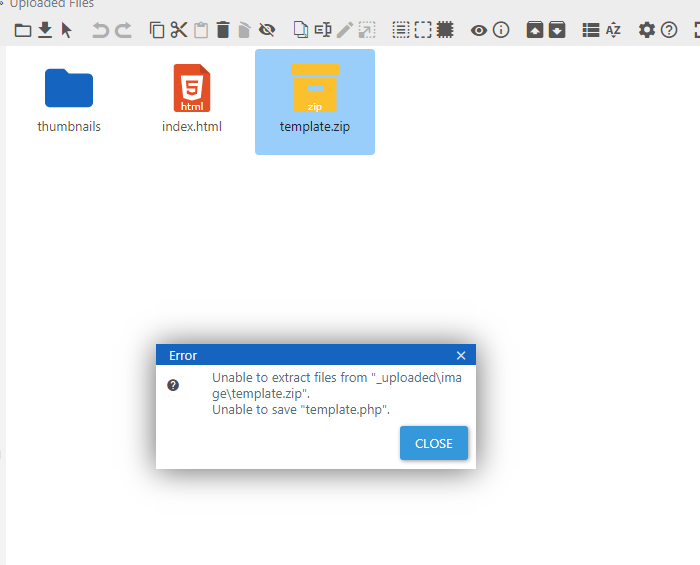
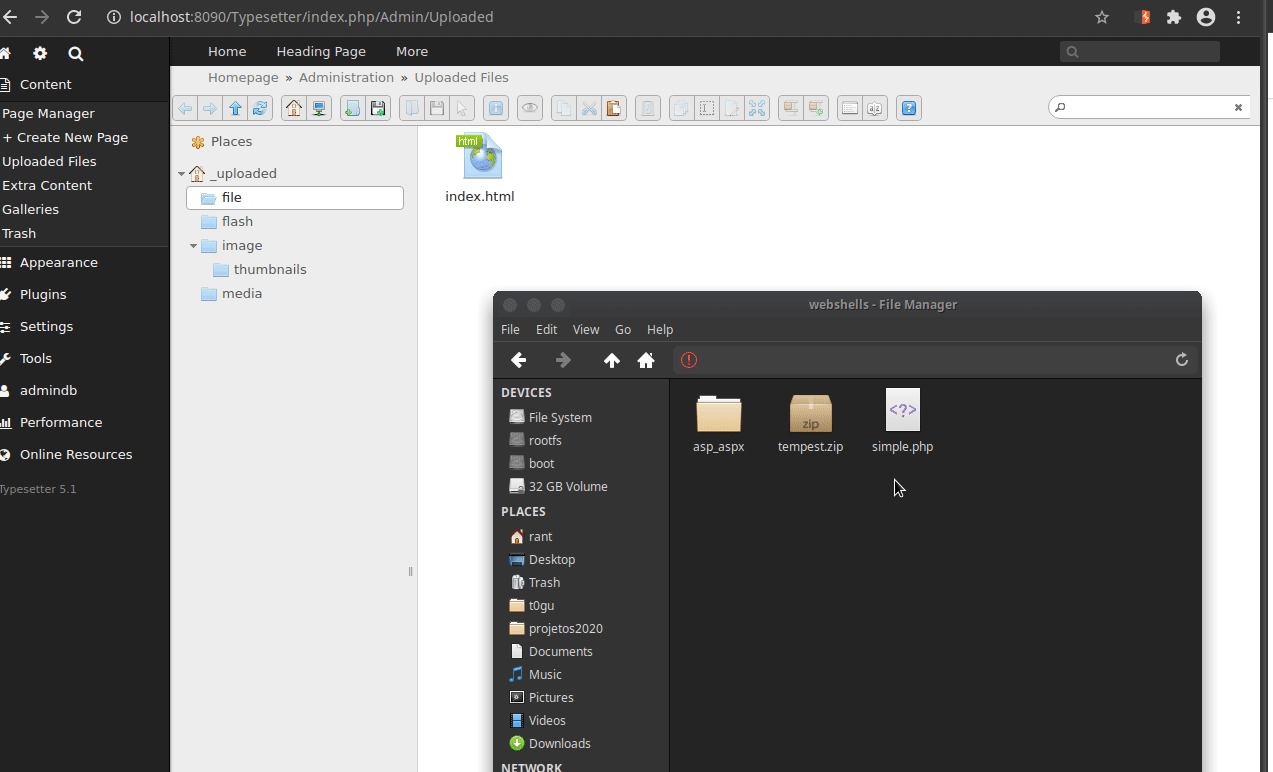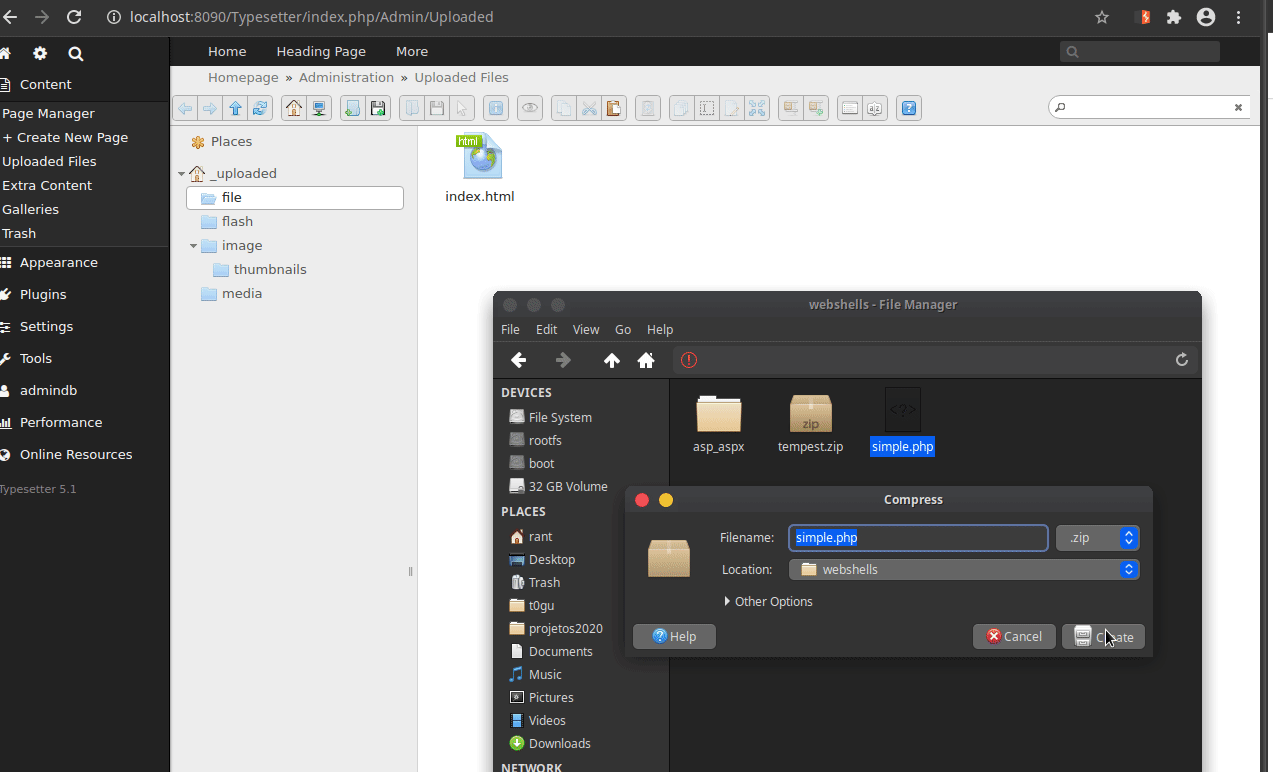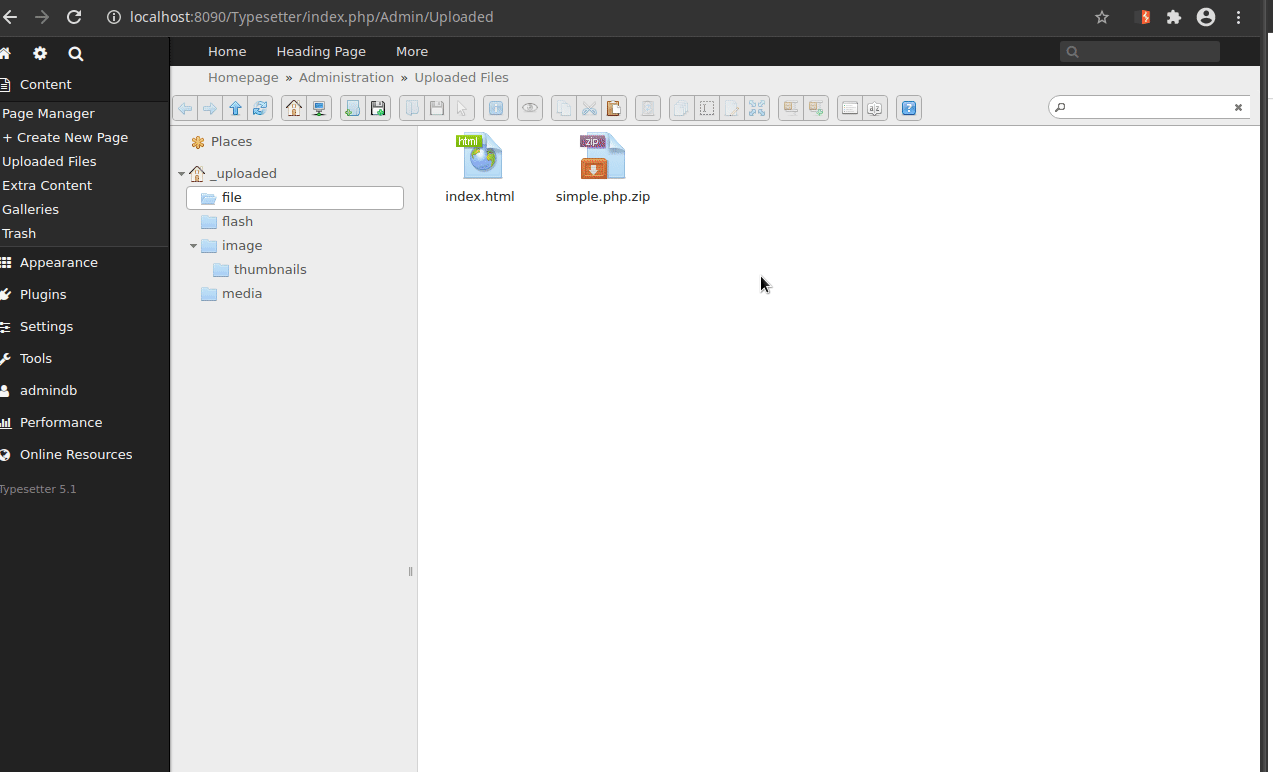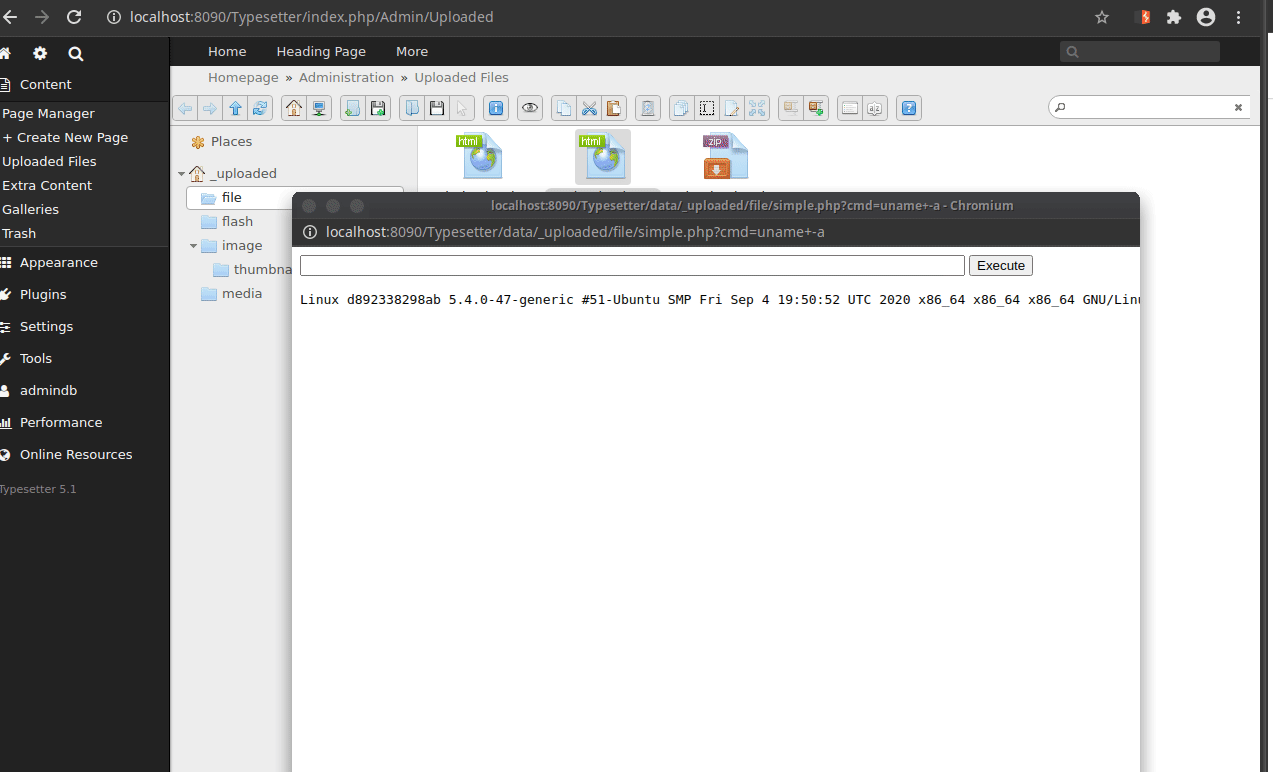
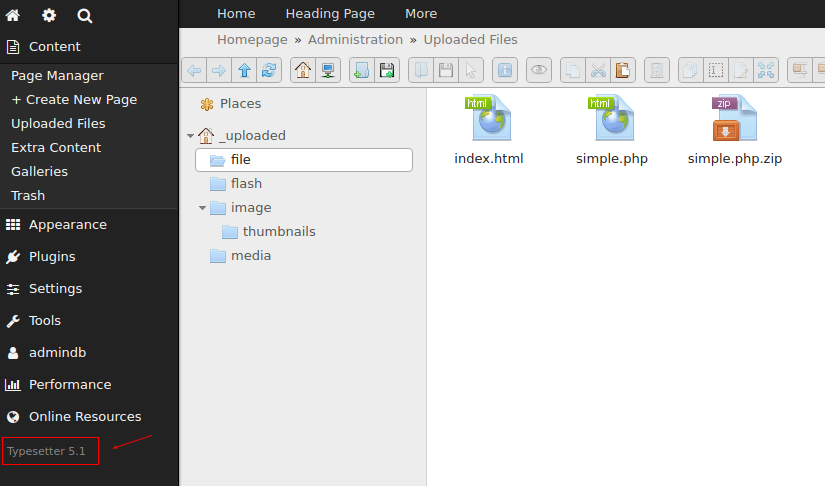

Hello all, I was testing the upload mechanism, and I found that it is possible to bypass the protection for .php files by placing the .php inside a .zip file and extracting it. Once this is done, it is possible to execute commands on the machine using a malicious php file (webshell). Okay, that and the viability decreased a little because it is an admin functionality, however, if it is not allowed to upload a .php file, then placing the same file inside a .zip and extracting and executing it should also not be allowed .
Steps to reproduce
1- As admin go to Content menu and click on Uploaded files
2- Inside the try to upload a .php file, and
3- try to upload a .php file directly, check that it is not possible.
4- Take the same .php file and place it in a .zip and upload it.
5- Extract through functionality and open the .php file
Obs: A strange behavior was that, after extracting the PHP file in functionality, it is seen as HTML.
PoC
==> Executing Commands
==> Try to upload a .php direct
The text was updated successfully, but these errors were encountered: