-
Notifications
You must be signed in to change notification settings - Fork 21.1k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it #29197
Comments
|
@rajmusuku Can you please share the link to the document which you are referring so that we can assign it to the correct team. |
|
@rajmusuku Thank you for the details. We will review and provide an update as appropriate. |
|
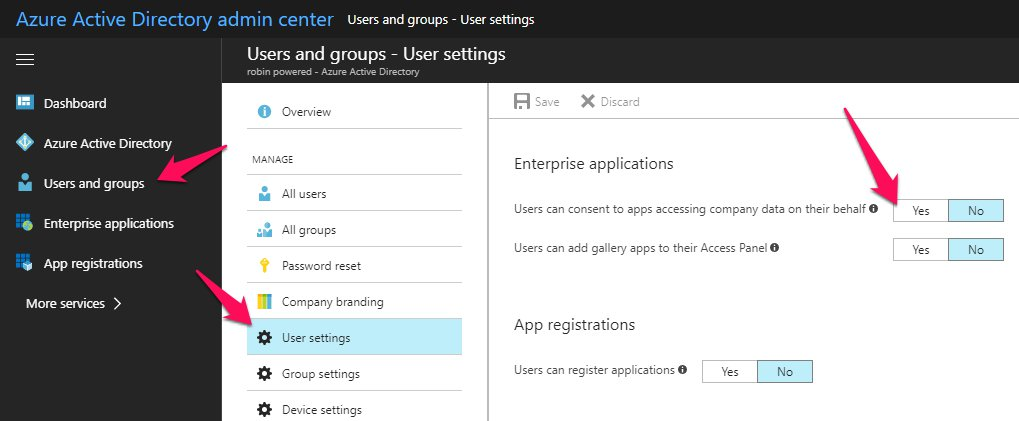
@rajmusuku , The easiest way to allow your service account to connect is to enable user access to Enterprise apps. From your Admin portal, go to Admin Centers > Azure AD > Users and Groups > User Settings then make sure "Users can consent to apps accessing company data on their behalf" is enabled. |
|
@rajmusuku, We will now proceed to close this thread. If there are further questions regarding this matter, please tag me in your reply. We will gladly continue the discussion and we will reopen the issue. |
|
Hi @YASWANTHM-MSFT, I am having the same issue as @rajmusuku's and Admin Centers > Azure AD > Users and Groups > User Settings > "Users can consent to apps accessing company data on their behalf" is already enabled. I want to enable AAD authentication for my Azure Storage Account blobs archive |
|
@YASWANTHM-MSFT I sorted this out with my org's admin, thanks! |
|
Glad to know that your issue is resolved. |
|
Any idea how to solve this? |
What did you do with your organisation admin to resolve this? |
|
Can you please help me with the issue. Can I know what you have done with your Org's Admin to resolve this @YASWANTHM-MSFT |
|
@Karthiktandra your Azure Active Directory Admin must grant admin consent to your app for some azure api, using the button Grant admin consent for Application at the bottom of the API Permissions blade: |
|
To address this part of the original question: Should we always use the resource id as "https://storage.azure.com/"? Will it be changed ever since the id would be different for each storage account You can use the storage account root URI as the resource ID. We've recently updated the documentation to add this information. For example, see Well-known values for authentication with Azure AD. |
|
Hi @patriziobruno, Thanks for the information, I will make the relevant changes. |
|
I am getting the same error. I wanted to understand how can I find out the admin name for my org to login to azure active directory admin portal. This is bit urgent and help here will be highly appreciated. |
|
Any updates here? |
|
Hi @AbhaPatankar , Please check in Subscriptions- Access Control - Classic Admin. List of admins will be visible there. You can ask the global admin to grant the permission. |
|
Hello Greg,
I am Abha, part of Microsoft’s Azure DevOps team. We use “Supa Tool” to create the work items by automatically reding the mailbox/ github source.
To do this, we use GraphMailSouce by creating an App. However, while running the tool, I got the following error:
“Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it”
Please can you grant permissions to the app so that I can start using it to import the work items.
Regards,
Abha
From: Karthiktandra <notifications@github.com>
Sent: Thursday, November 28, 2019 10:35 AM
To: MicrosoftDocs/azure-docs <azure-docs@noreply.github.com>
Cc: Abha Patankar <Abha.Patankar@microsoft.com>; Mention <mention@noreply.github.com>
Subject: Re: [MicrosoftDocs/azure-docs] Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it (#29197)
Hi @AbhaPatankar<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2FAbhaPatankar&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853080679&sdata=cle9Mrzjl%2BSK17hhDTJh1ImFASFM7wPjUMLdx3zGKXU%3D&reserved=0> ,
Please check in Subscriptions- Access Control - Classic Admin.
List of admins will be visible there.
You can ask the global admin to grant the permission.
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2FMicrosoftDocs%2Fazure-docs%2Fissues%2F29197%3Femail_source%3Dnotifications%26email_token%3DAHWLI7QEVZV2OMUE2D2EUKLQV5GOXA5CNFSM4HFCMXYKYY3PNVWWK3TUL52HS4DFVREXG43VMVBW63LNMVXHJKTDN5WW2ZLOORPWSZGOEFLOMPI%23issuecomment-559343165&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853080679&sdata=%2FxqXr3A9C%2Fs5c34BMEinc3W3A6zNXCJhnEHYn09ibW0%3D&reserved=0>, or unsubscribe<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fnotifications%2Funsubscribe-auth%2FAHWLI7SBAPJT4XEKFRTR74DQV5GOXANCNFSM4HFCMXYA&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853090678&sdata=1BzedKawmEaBKSAhaCeYCSLx5mXuGoReLtIZM0tjct0%3D&reserved=0>.
|
|
Hi Greg,
Any update on this? It is a bit urgent for us as it is impacting ~40 people in our org.
Regards,
Abha
From: Abha Patankar
Sent: Thursday, November 28, 2019 11:01 AM
To: Greg Arnits <gregar@microsoft.com>
Cc: Mention <mention@noreply.github.com>; MicrosoftDocs/azure-docs <reply@reply.github.com>; MicrosoftDocs/azure-docs <azure-docs@noreply.github.com>; Sadagopan Rajaram <sadar@microsoft.com>; Vijayaraghavan Vedantham <Vijayaraghavan.Vedantham@microsoft.com>; Madhuri Vadali Vadali (TECH MAHINDRA LTD.) <v-madhva@microsoft.com>
Subject: RE: [MicrosoftDocs/azure-docs] Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it (#29197)
Hello Greg,
I am Abha, part of Microsoft’s Azure DevOps team. We use “Supa Tool” to create the work items by automatically reding the mailbox/ github source.
To do this, we use GraphMailSouce by creating an App. However, while running the tool, I got the following error:
“Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it”
Please can you grant permissions to the app so that I can start using it to import the work items.
Regards,
Abha
From: Karthiktandra <notifications@github.com<mailto:notifications@github.com>>
Sent: Thursday, November 28, 2019 10:35 AM
To: MicrosoftDocs/azure-docs <azure-docs@noreply.github.com<mailto:azure-docs@noreply.github.com>>
Cc: Abha Patankar <Abha.Patankar@microsoft.com<mailto:Abha.Patankar@microsoft.com>>; Mention <mention@noreply.github.com<mailto:mention@noreply.github.com>>
Subject: Re: [MicrosoftDocs/azure-docs] Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it (#29197)
Hi @AbhaPatankar<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2FAbhaPatankar&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853080679&sdata=cle9Mrzjl%2BSK17hhDTJh1ImFASFM7wPjUMLdx3zGKXU%3D&reserved=0> ,
Please check in Subscriptions- Access Control - Classic Admin.
List of admins will be visible there.
You can ask the global admin to grant the permission.
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2FMicrosoftDocs%2Fazure-docs%2Fissues%2F29197%3Femail_source%3Dnotifications%26email_token%3DAHWLI7QEVZV2OMUE2D2EUKLQV5GOXA5CNFSM4HFCMXYKYY3PNVWWK3TUL52HS4DFVREXG43VMVBW63LNMVXHJKTDN5WW2ZLOORPWSZGOEFLOMPI%23issuecomment-559343165&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853080679&sdata=%2FxqXr3A9C%2Fs5c34BMEinc3W3A6zNXCJhnEHYn09ibW0%3D&reserved=0>, or unsubscribe<https://nam06.safelinks.protection.outlook.com/?url=https%3A%2F%2Fgithub.com%2Fnotifications%2Funsubscribe-auth%2FAHWLI7SBAPJT4XEKFRTR74DQV5GOXANCNFSM4HFCMXYA&data=02%7C01%7CAbha.Patankar%40microsoft.com%7C28fb375b5c8740d0002008d773c07b2d%7C72f988bf86f141af91ab2d7cd011db47%7C1%7C0%7C637105142853090678&sdata=1BzedKawmEaBKSAhaCeYCSLx5mXuGoReLtIZM0tjct0%3D&reserved=0>.
|
|
was there a conclusion? |
|
If, by any chance, you found this issue while configuring You're welcome. |
|
as @patriziobruno said, I needed the admin consent in my api permissions and it works perfectly on msdal lib to angular |


Followed all the steps as mentioned in doc, however I see an issue of admin consent although the storage account was created by me. Here is the error notification.
"Application needs permission to access resources in your organization that only an admin can grant. Please ask an admin to grant permission to this app before you can use it"
Document Details
⚠ Do not edit this section. It is required for docs.microsoft.com ➟ GitHub issue linking.
The text was updated successfully, but these errors were encountered: