We read every piece of feedback, and take your input very seriously.
To see all available qualifiers, see our documentation.
There is a risk of sensitive information leakage in the user information acquisition of CloudExplorer Lite.
The reproduction steps are as follows:
1.Using the system administrator account to log in, the following interface returns information about all users in the current system, including the password md5: https://cloudexplorer-lite-demo.fit2cloud.com/management-center/api/user/page?currentPage=1&pageSize=1
2.Using the MD5 library to search, you can find the plaintext passwords of some users.
Expected processing logic:
stay https://github.com/CloudExplorer-Dev/CloudExplorer-Lite/blob/main/framework/management-center/backend/src/main/java/com/fit2cloud/controller/UserController.java Although the listUser interface has been set as read-only permission, there should be restrictions on returning data and sensitive credential information such as passwords cannot be returned, resulting in the risk of losing control of permissions.
Affected versions: <= 1.4.0.
The vulnerability has been fixed in v1.4.0.
It is recommended to upgrade the version to v1.4.0.
If you have any questions or comments about this advisory:
Open an issue in https://github.com/CloudExplorer-Dev/CloudExplorer-Lite Email us at xin.bai@fit2cloud.com
Impact
There is a risk of sensitive information leakage in the user information acquisition of CloudExplorer Lite.
The reproduction steps are as follows:
1.Using the system administrator account to log in, the following interface returns information about all users in the current system, including the password md5: https://cloudexplorer-lite-demo.fit2cloud.com/management-center/api/user/page?currentPage=1&pageSize=1
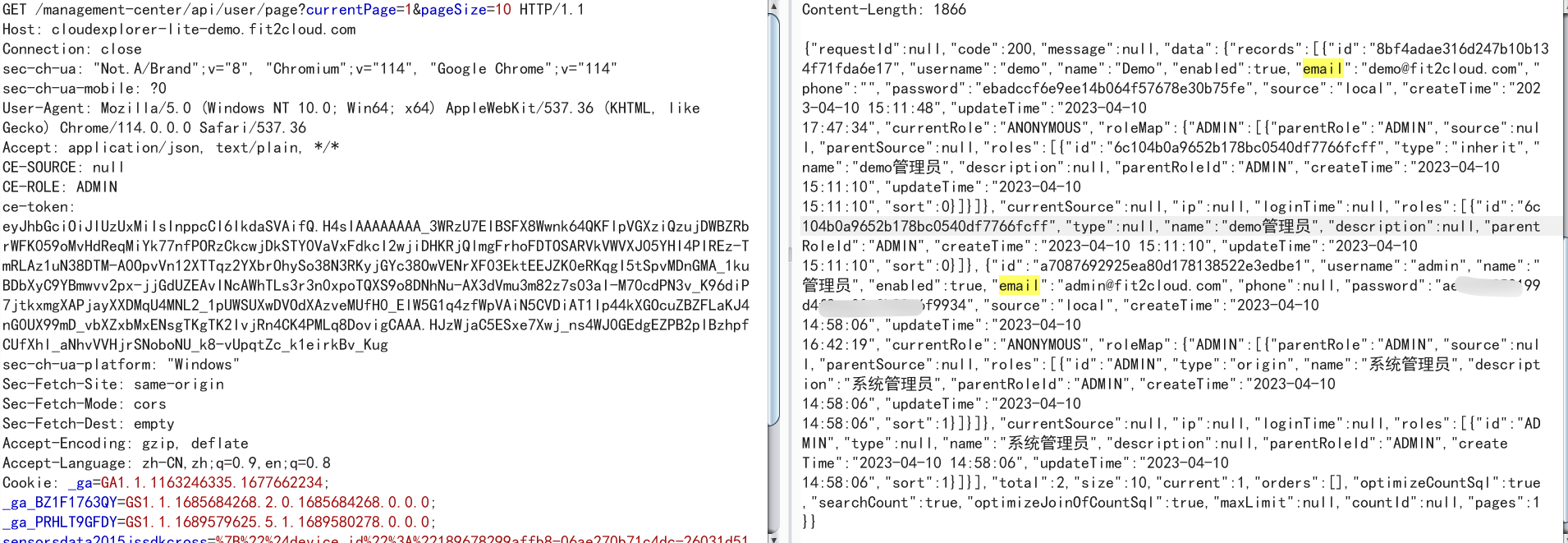
2.Using the MD5 library to search, you can find the plaintext passwords of some users.
Expected processing logic:
stay https://github.com/CloudExplorer-Dev/CloudExplorer-Lite/blob/main/framework/management-center/backend/src/main/java/com/fit2cloud/controller/UserController.java Although the listUser interface has been set as read-only permission, there should be restrictions on returning data and sensitive credential information such as passwords cannot be returned, resulting in the risk of losing control of permissions.
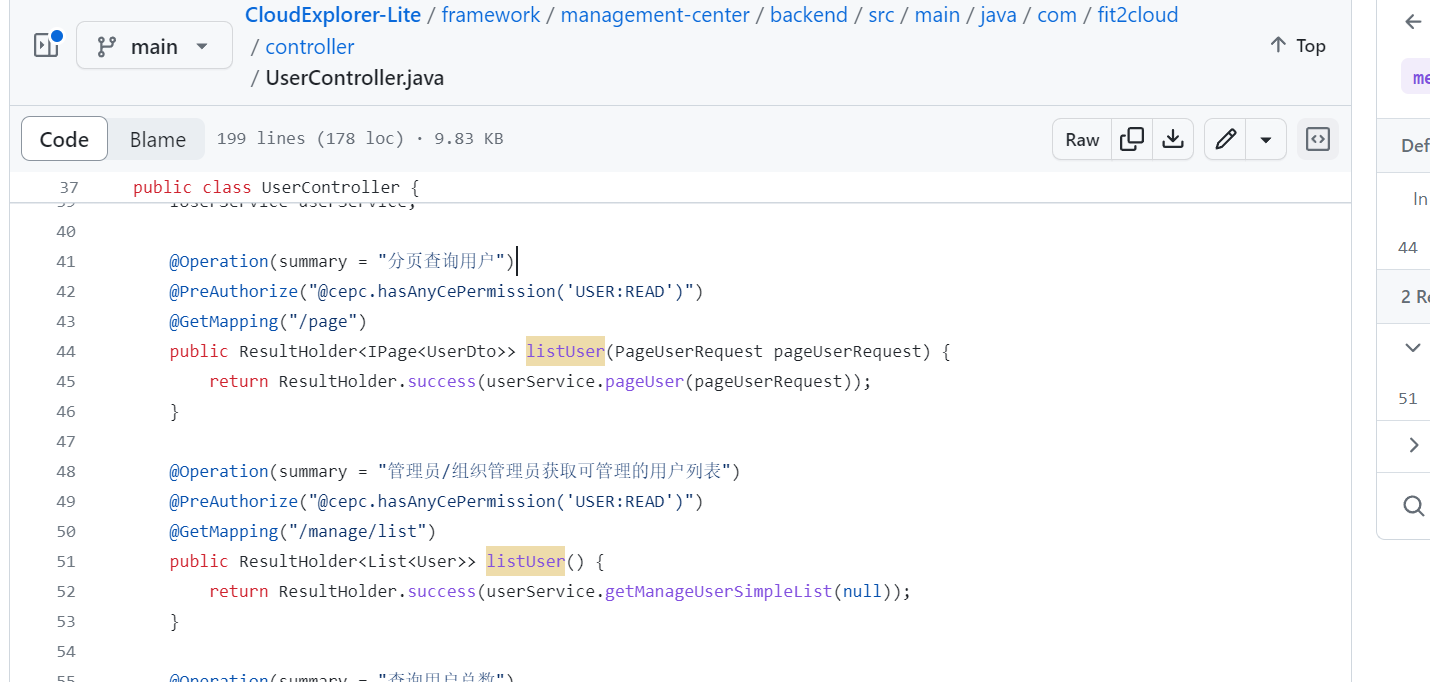
Affected versions: <= 1.4.0.
Patches
The vulnerability has been fixed in v1.4.0.
Workarounds
It is recommended to upgrade the version to v1.4.0.
References
If you have any questions or comments about this advisory:
Open an issue in https://github.com/CloudExplorer-Dev/CloudExplorer-Lite
Email us at xin.bai@fit2cloud.com