You signed in with another tab or window. Reload to refresh your session.You signed out in another tab or window. Reload to refresh your session.You switched accounts on another tab or window. Reload to refresh your session.Dismiss alert
This is the base information of the website. It is obviously the latest version of the feehi cms. And in the advertising management of feehi cms v2.1.1, you can upload PHP file by changing the image suffix to PHP, resulting in command execution.It has a file upload vulnerability before V2.0.8 and can directly execute any code. The vulnerability number is CNVD-2022-13190 (CVE-2020-21322). The vulnerability is caused by processing image upload/common/models/AdminUser. PHP when processing image upload, rules rules is not effective, lead to the uploader can control the upload file suffix.
The first time to upload the image directly, the front end will report an error, upload failure. And as you can see, the field of User[avatar] is empty.
Then you need go back to the front end. You need to hit the delete key, at this time, select a new file to upload. After observing that AdminUser[avatar] is 0 in the data packet.
The text was updated successfully, but these errors were encountered:
This is the base information of the website. It is obviously the latest version of the feehi cms. And in the advertising management of feehi cms v2.1.1, you can upload PHP file by changing the image suffix to PHP, resulting in command execution.It has a file upload vulnerability before V2.0.8 and can directly execute any code. The vulnerability number is CNVD-2022-13190 (CVE-2020-21322). The vulnerability is caused by processing image upload/common/models/AdminUser. PHP when processing image upload, rules rules is not effective, lead to the uploader can control the upload file suffix.

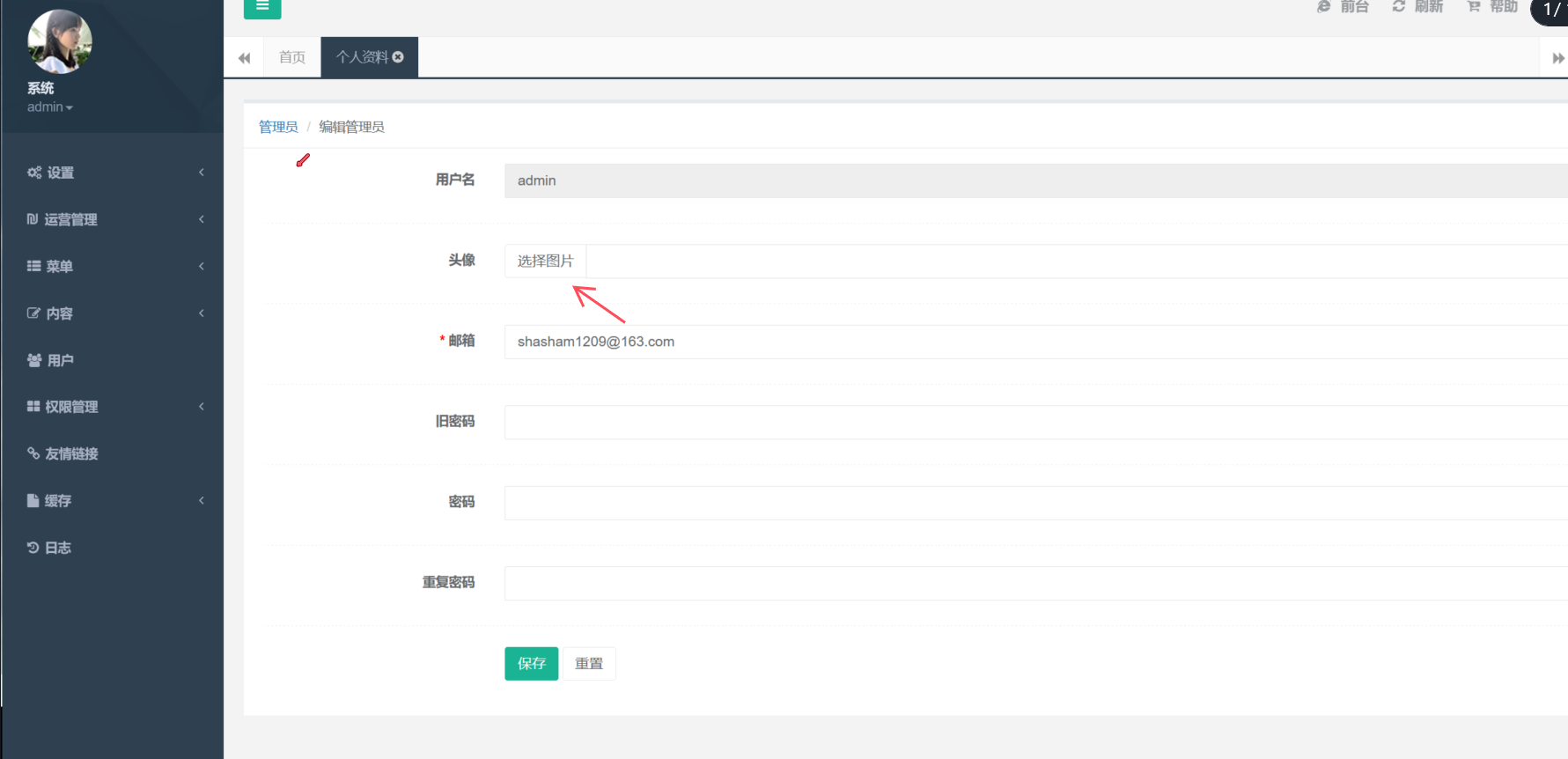









The first time to upload the image directly, the front end will report an error, upload failure. And as you can see, the field of User[avatar] is empty.
Then you need go back to the front end. You need to hit the delete key, at this time, select a new file to upload. After observing that AdminUser[avatar] is 0 in the data packet.
The text was updated successfully, but these errors were encountered: