New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
feat: no-scan mode #4110
Comments
|
@terriko Generating SBOMs from binaries is a very useful feature and not found in many other OSS products. However I wonder whether we need to start thinking about a bit of refactoring to offer a number of different 'scripts' which support the different use cases we are now seeing. There are a number of features which could become useful standalone modules
These could then be put together to create some new apps e.g.
|
|
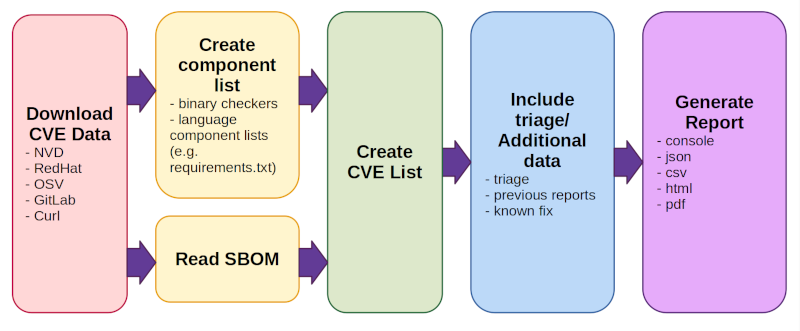
Version compare should probably be a separate module too (see #4801), but I still haven't decided if it should really just be a separate pip dependency or what. Other than the "I really only want component analysis" request, I feel like a lot of our bugs are people who just want to run cve-bin-tool and have it do magic and they don't really know or understand what they're scanning, so the all-in-one we're trending towards may be the right solution for them. But the idea of refactoring is pretty tempting. I'd divide it very subtly differently, more in line with our architecture diagram, and group all of the binary/language parser/sbom parser stuff together into a big "component analysis" blob: We'd want to merge the download and CVE parts (red and green boxes) but the rest could probably be separate:
Some open questions:
|
Description
Add the ability to generate an SBOM without doing a cve scan of the components found. We could potentially make this work for other formats other than SBOM (such as an HTML report) but I suspect that SBOM will be by far the preferred mode.
Right now, the tool expects you to initialize the database with data from NVD and will always provide whatever scan results it finds. But the binary signatures and our collection of parsers could be used just to give you a list of components without any vulnerability information attached. While we've alleviated some of our problems with NVD reliability using the mirror, it's still a lot of data to download if you're not even going to use it, so it would be nice to have a way for people to turn that off if they don't want it.
I'm not sure off the top of my head exactly how much re-wiring this would take. We may be able to fake something up by initializing an empty database if no database exists, but I don't want it generating a bunch of reports that says "0 cves found" if in fact no data was downloaded. At a guess, we'd need to refactor in a few places:
--offlinefor network calls.--no-scan) to trigger the behaviourgenerate-sbomafter they've pip installed cve-bin-tool.csv2cvelink to the syntatic sugar that is that fileWhy?
It turns out that some users. particularly in the embedded community, find our ability to generate SBOMs from binaries useful but don't need to use the cve-scanning portion of cve-bin-tool (either because they only want a component list or because they use another tool for this part of things).
This was a bit of a surprise to me. The embedded tools I use most can generate their own (more accurate) SBOMs, and I'd assumed that existing tools used for licensing had already covered the binary analysis gap reasonably well. But it sounds like we have a little niche with our combo of binary signature and sbom export capabilities. Even if it feels a bit at odds with our original goals for this project, I'd really like to support our users better!
The text was updated successfully, but these errors were encountered: